Leveraging Wazuh to combat insider threats
Insider threat refers to the risk posed by individuals with authorized access to an organization’s systems, networks, or sensitive information. These individuals may be employees, contractors, or business partners who possess a deep understanding of the organization’s infrastructure and protocols.
Insider threats can manifest in various forms, such as data theft, sabotage, gaining unauthorized access, or the introduction of malware.
What makes insider threats particularly challenging is that the perpetrators often have legitimate credentials, making it harder to detect their activities and distinguish them from regular users.
Effective strategies for mitigating insider threats involve a combination of detective and preventive controls like continuous monitoring, alerting, and automated incident response. Such controls are provided by the Wazuh SIEM and XDR platform.
Monitoring user activities
By collecting and analyzing log data from various sources, including network devices, servers, applications, and endpoints, organizations can detect and respond to suspicious user behavior in real-time.
Key aspects of user activity monitoring include:
- Log collection and analysis: User activity logs should be aggregated from diverse endpoints and applications, allowing for centralized monitoring and analysis. By collecting and analyzing user activity logs, organizations can detect security incidents and detect abnormal behaviors of legitimate users.
SIEM and XDR solutions facilitate the collection and correlation of security events, providing contextual information to assess the severity and potential impact of insider threats.
- Real-time alerting: Real-time alerting empowers security teams to detect cyber threats as they happen or in the quickest time possible. A reduction in dwell time enables organizations to respond promptly to potential security incidents, minimizing the impact of an attack.
A robust security solution should be able to integrate with third-party solutions for easy alerting. This includes emails, instant messaging, or even incident response pipelines. platforms
- Automated incident response: Insider attacks can occur at any time; their speed and complexity might outrun the manual response approach. Automating responses to threats or incidents helps organizations mitigate attacks and reduce their impact quickly and efficiently.
When dealing with insider threats, automated incident response is important as it allows security teams to swiftly respond to detected threats. Automating incident response helps to achieve a proactive defense against insider threats.
For example, a user account can be automatically locked when suspicious activities are detected from the user account.
How Wazuh helps combat insider threat

Wazuh is a free, open source security platform that offers unified XDR and SIEM capabilities. It provides a wide array of security and protection modules.
It allows users to easily visualize and detect security events on monitored endpoints and services. Some Wazuh features include:
- Log data collection and analysis: Wazuh Log data collection allows integration with a wide variety of products, including common workplace solutions like Microsoft 365, Google Workspace, Active Directory, and GitHub. It also allows monitoring of user activities in Linux and Windows endpoints. It also includes out-of-the-box rules.
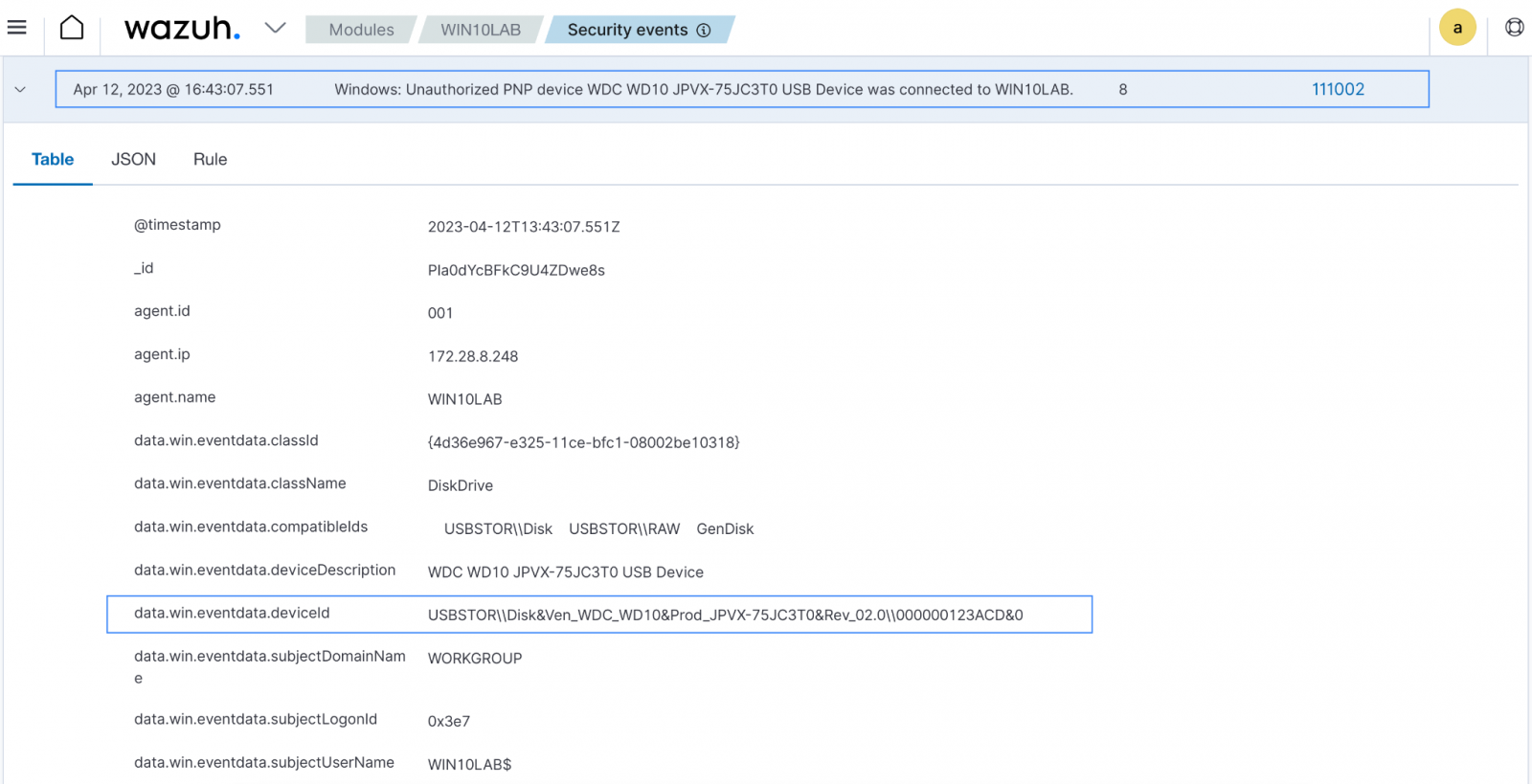
For example, the image below shows when Wazuh detects the use of an unauthorized USB drive on a Windows endpoint.
- File integrity monitoring: The File Integrity Monitoring (FIM) capability of Wazuh allows security teams to monitor files and directories. It detects the creation, modification, or deletion of files in the specified directories on the monitored endpoint. These files could be confidential business data, configuration files, Personally Identifiable Information (PII), or other sensitive files.
By monitoring sensitive files, security teams can quickly identify data breaches or when the integrity of a file is compromised.
- Active response: Wazuh Active Response module automates actions in response to configured triggers. It has out-of-the-box scripts that help security teams automatically trigger responses that mitigate the impact of security incidents. The module is customizable, and security teams can generate their own scripts to carry out the appropriate actions required.
For example, Wazuh can detect malicious user activity and automatically block the user account based on predefined active responses.
- Security configuration assessment: Wazuh Security configuration assessment (SCA) module scans monitored endpoints to detect the presence of misconfiguration flaws that open the endpoint to vulnerabilities. The SCA module is highly customizable and can be configured to identify misconfigurations such as wrongly configured services, the use of insecure protocols, or vendor default credentials.
Reviewing the security configuration of endpoints is critical. It helps organizations identify vulnerabilities, reduce risk, maintain compliance, and ensure that systems are resilient against cyber threats.
Regular and thorough security configuration reviews are essential for establishing a strong defense against cyberattacks.
Conclusion
Mitigating insider threats in cybersecurity requires a proactive approach. By implementing strong access controls and maintaining continuous monitoring and auditing, organizations can significantly reduce the risks posed by insider threats.
Wazuh SIEM and XDR platform integrates with various tools commonly used for productivity in organizations. It provides capabilities such as automated incident response to address insider threats through proactive detection and mitigation of suspicious activities carried out by users.
This ensures the safeguarding of their digital assets from internal vulnerabilities.
You can learn more about Wazuh capabilities by checking out this documentation and joining the community for support and updates.
Sponsored and written by Wazuh.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[QILIN] - Ransomware Victim: www[.]nuphoton[.]com 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)