Microsoft Exchange 2010 End of Support and Overall Patching Study

Today’s topic is Exchange 2010, which reaches end of support (EoS) on Oct. 13, 2020, as well as a survey of other versions of Exchange and how well they are being kept up-to-date. During our work with Project Sonar, we consistently see the use of old and EoS software on the internet. This is generally a cause for concern, because this typically means that vulnerabilities will not be fixed. It is also an indicator that the environment the software is running in has other security issues.
The key takeaways from this post are:
- Organizations running Exchange 2010 and earlier should upgrade to supported technology as soon as possible.
- Organizations running Exchange 2013 should begin planning to upgrade to newer technologies.
- Statistically speaking, most organizations running any version of Exchange are missing updates for critical vulnerabilities.
Before I move on, I want to point out that our numbers here will be fairly accurate, but not perfect. This is due to a couple of factors: First, the method that we use to fingerprint Exchange OWA allows us to determine the Exchange version down to <major version>.<minor version>.<build number>, but we cannot see the revision. For example, for Exchange Server 2019 Cumulative Update (CU) 7, with the latest updates the build number is 15.2.721.2, but we only see 15.2.721. This means that we can tell that the server is running 2019 CU7, but we can’t be sure whether this month’s patches were installed. Second, and most frustrating, is that Microsoft’s updates don’t always adjust the version number shown by tooling. Even Microsoft’s own Exchange Admin Center and Get-ExchangeServer command will report incorrect versions in many instances.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe
Exchange 2010: A decade of support ends
Just under 11 years ago, Microsoft released Exchange 2010. On Tuesday, Oct. 13, 2020, Microsoft Exchange 2010 will reach End of Support (EoS) status. Microsoft will not provide any updates, including security fixes, after this date. While the software will keep working after this date, a quick glance at the Exchange vulnerabilities announced in 2020 will quickly show the importance of security updates.
In March 2020, we used Project Sonar to measure the number of Exchange servers that might be vulnerable to CVE-2020-0688. At that time, we found over 166,000 Exchange 2010 servers with internet-facing Outlook Web App (OWA) services. On Monday, Sept. 21, 2020, we looked again and found that while the numbers had decreased, there are still 139,771 OWA services.
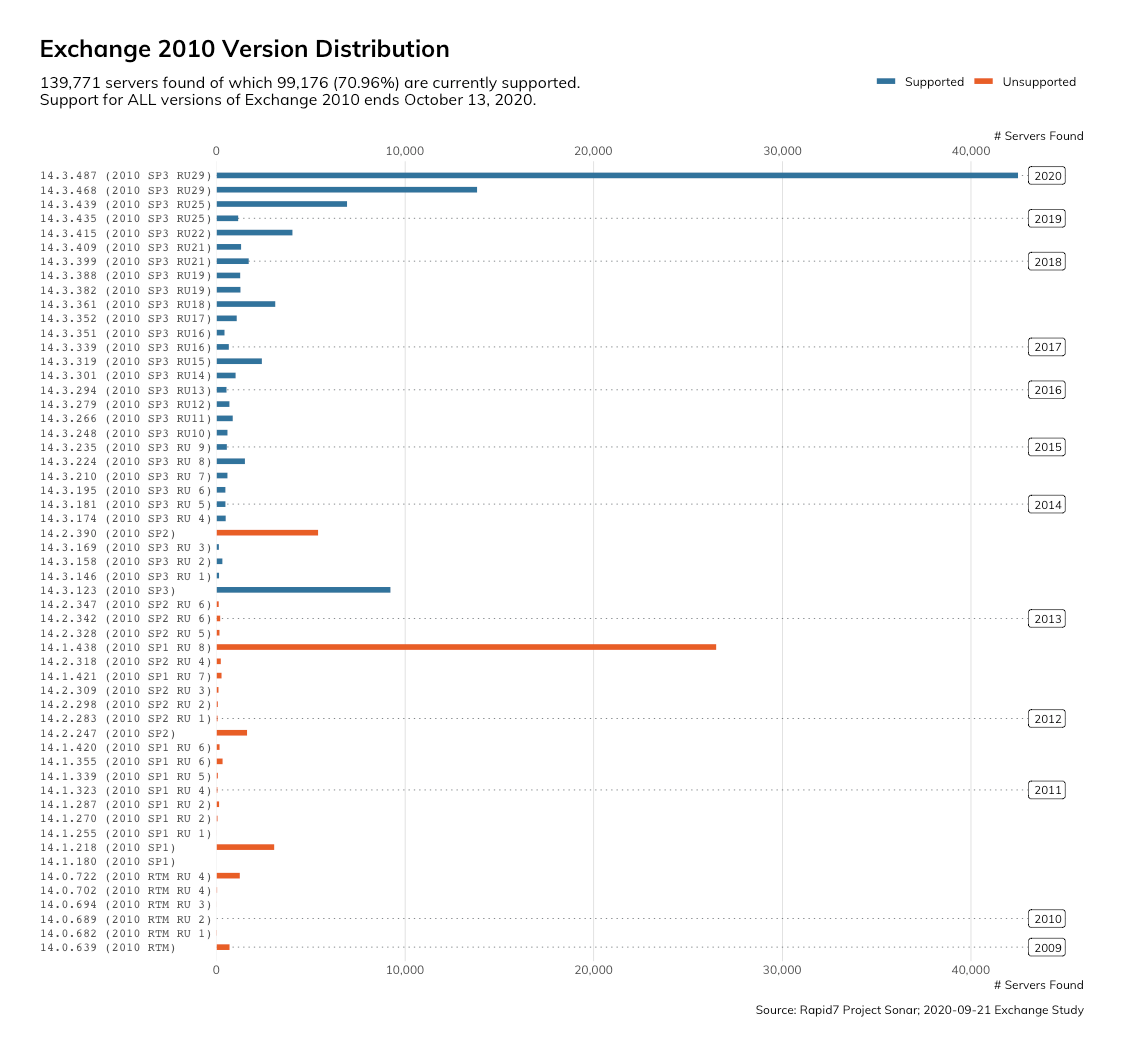
That’s a scary number of servers that will not receive security updates for any future vulnerabilities. Both scary and disappointing is the fact that 40,000 of these were already running unsupported versions of Exchange 2010. Nearly 54,000 of these have not been updated in six years!
Exchange 2007: Long past its expiration date
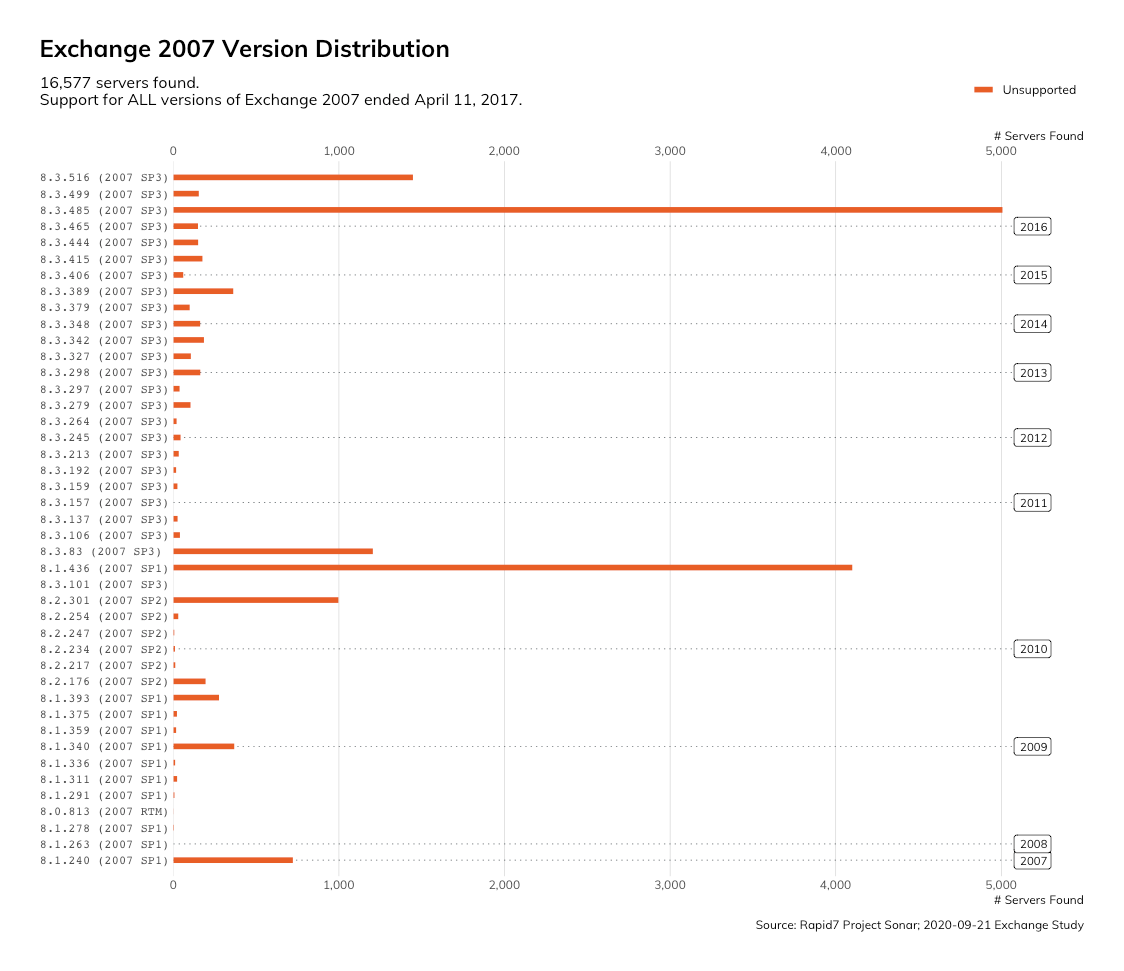
Speaking of software that hasn’t seen updates in years, there are 16,577 Exchange 2007 servers with OWA on the public internet. This product has been out of support for over three years. Additionally, the newest version of Windows Server that Exchange 2007 runs on is Windows Server 2008 R2, which reached EoS in January 2020. In summary, this is a business-critical application running in an environment in which vulnerabilities will not be fixed.
Exchange 2013: The twilight years
Exchange 2013 transitioned to Extended Support in 2018 and will cease to be supported at all on April 11, 2023. Additionally, the newest version of Windows Server that Exchange 2013 runs on is Windows Server 2012 R2, which reaches EoS on Oct. 10, 2023. In short, the full Exchange 2013 environment, other than AD, will be completely unsupported in less than three years.
Our Project Sonar metrics for OWA show that there are at least 102,593 Exchange 2013 servers on the public internet. Further, 67,567 (~66%) are not running a version of Exchange that Microsoft considers “Supported.”
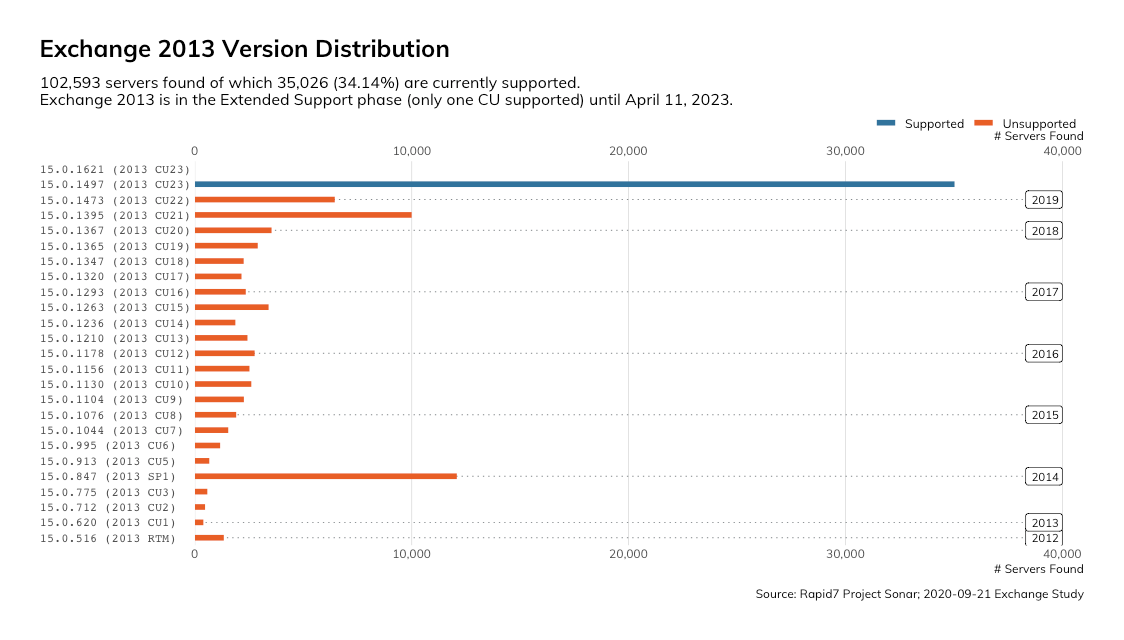
Given that Exchange is typically considered a business-critical application, and how complex an upgrade can be, we strongly recommend that organizations running Exchange 2013 start planning the upgrade process and timeline. The
“Upgrading considerations” portion of the “Taking actions” section at the end of the blog post calls out a few of the considerations that might make this process time-consuming or challenging.
Exchange 2016 and 2019: Newer, but still vulnerable
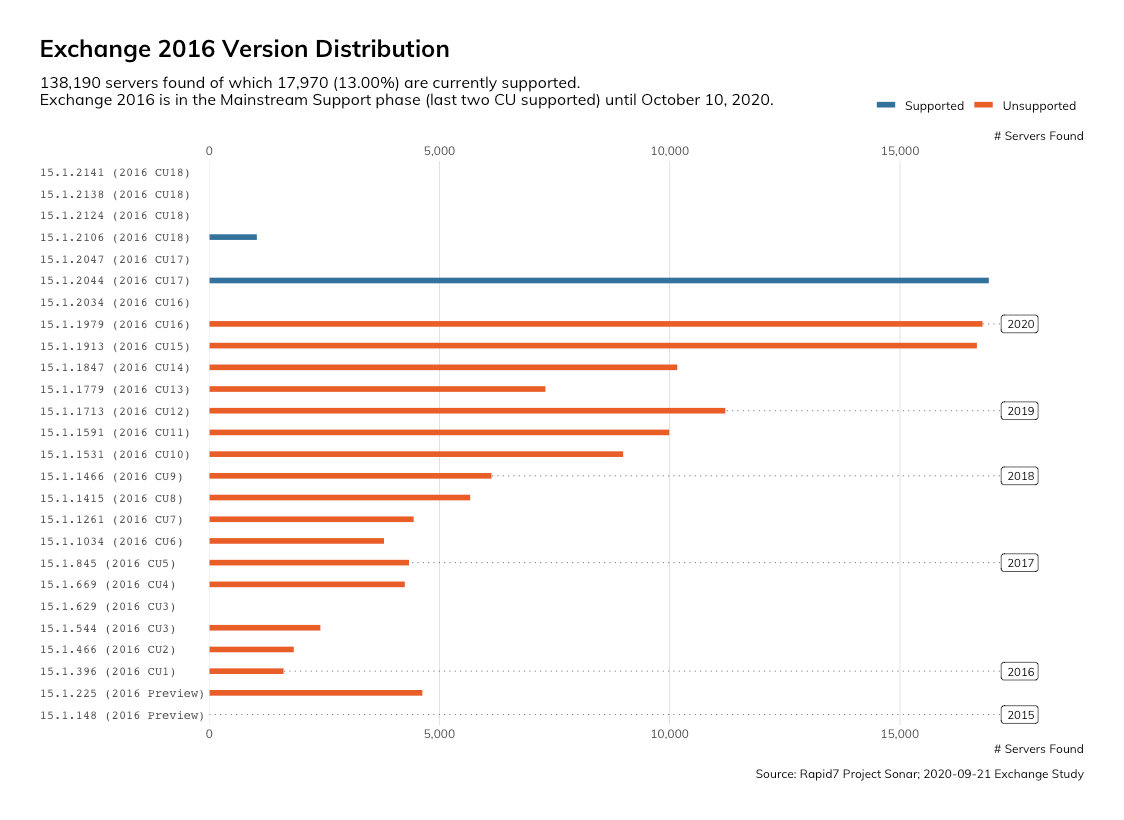
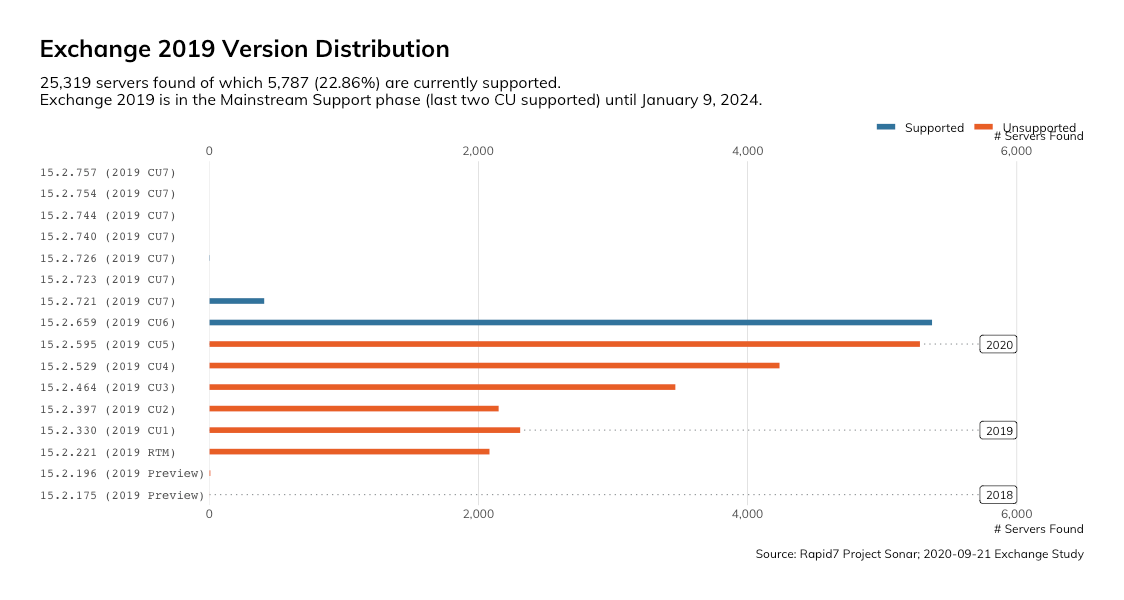
While Exchange 2016 and 2019 will be supported for some time to come, organizations running them appear to be doing a poor job of keeping their environments up-to-date.
Of the ~138,000 Exchange 2016 servers, 87% were missing the most recent updates.
Similarly, 77% of the ~25,000 Exchange 2019 servers we observed were missing updates. There are nearly 2,100 that, as far as we can tell, have never had updates installed.
Taking action
Given the potential risks that a compromised Exchange environment present, we have the following recommendations:
- Organizations using Exchange 2010 or earlier should aggressively pursue upgrading their environment to supported technologies.
- Organizations using Exchange 2013 should ensure they have a plan and timeline for upgrading to supported technologies by April 11, 2023. Remember that the most modern version of Windows Server that 2013 supports is also going EoS that year, so the process may introduce new server OSes into the environment as well. Please see the “Upgrading considerations” section below for some of the challenges that may need to be accounted for.
- Organizations using Exchange 2016 or on-premises 2019 should ensure their Exchange environment is currently up-to-date and that there is a plan and process for keeping it updated.
- Organizations using Exchange hosted by a non-Microsoft vendor should ensure the vendor has a plan and process for keeping the software up-to-date. They should also verify this is being done and hold the vendor accountable if not.
- Leverage vulnerability management tools and other types of tools to detect when Exchange environments are missing updates. They will be particularly helpful when Exchange version numbers cannot be reliably determined.
Upgrading considerations
Upgrading an Exchange environment is a very complex task that is compounded by the server and client dependencies. This is why planning in advances is critical. Here are some examples of some issues organizations may run into when planning an upgrade:
- Upgrading from Exchange 2010: There is no direct upgrade path from Exchange 2010 to Exchange 2019. Organizations will need to upgrade to Exchange 2013 or 2016 first.
- Active Directory (AD) server OS: Exchange 2019 doesn’t support Windows Server 2012 AD servers and requires the AD forest functional level to be at least 2012 R2.
- TLS: Exchange 2019, by default, requires TLS 1.2. This means that clients will need to support TLS 1.2, or other workarounds will need to be implemented in order to support legacy clients.
- Outlook compatibility: Exchange 2019 requires at least Outlook 2013 with the most recent updates. Keep in mind that Outlook 2013 goes EoS April 11, 2023, so those leveraging it should upgrade to Outlook 2016 or higher.
- Unified Messaging (UM): UM was removed in Exchange 2019
- Web browser compatibility: Exchange 2019 doesn’t support Internet Explorer 10 or lower.
Assess Your Environment for Microsoft Exchange Vulnerabilities and Take Action
Get Started
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.




