Microsoft Suffered A Rare Cyber-Security Lapse When One of Bing’s Backend Servers Were Exposed Online

Microsoft endured a rather rare cyber-security lapse just this month when the company’s IT staff incidentally left one of Bing’s backend servers exposed on the web.
Discovered by Ata Hakcil, a security researcher at WizCase, only imparted his discoveries to ZDNet the previous week. As per Hakcil’s investigation, the server is said to have exposed more than 6.5 TB of log documents containing 13 billion records coming from the Bing search engine.
Hakcil said the server was exposed from September 10 to September 16, when he initially had informed the Microsoft Security Response Center (MSRC), and the server was made secure one more time with a password.
The Wizcase researcher had the option to check and re-check his discoveries by finding search queries he performed in the Bing Android app in the server’s logs.
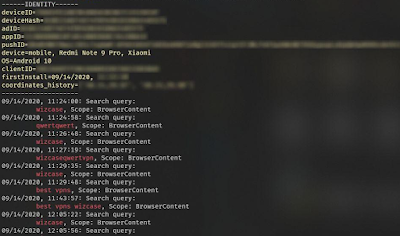
Microsoft admitted to committing this mistake and commented last week,
“We’ve fixed a misconfiguration that caused a small amount of search query data to be exposed,” a Microsoft spokesperson told ZDNet in an email last week. After analysis, we’ve determined that the exposed data was limited and de-identified.” ZDNet, which was provided access to the server while it was exposed without a password, can affirm that no personal user info was made public.
Rather, the server exposed specialized details, like search inquiries, details regarding the client’s system (device, OS, browser, etc.), geo-location details (wherever accessible), and various tokens, hashes, and coupon codes.

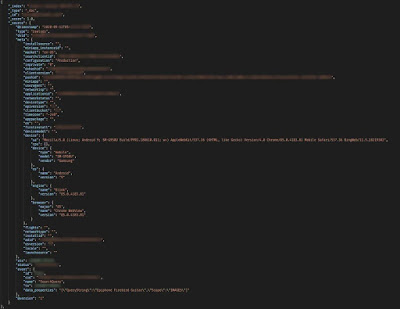
The leaky server was distinguished as an Elasticsearch system. Elasticsearch servers are high-grade systems where organizations collect huge amounts of information to handily search and channel through billions of records easily.
Throughout the previous four years, Elasticsearch servers have frequently been the source of numerous coincidental information leaks.
The reasons are known to fluctuate and can go from administrators neglecting to set a password; firewalls or VPN frameworks unexpectedly going down and uncovering an organization’s normally-internal servers; or organizations duplicating production data to test systems that aren’t always secured as rigorously as their essential infrastructure.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[LYNX] - Ransomware Victim: Greta Group 5 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
