Microsoft Teams phishing attack pushes DarkGate malware

A new phishing campaign is abusing Microsoft Teams messages to send malicious attachments that install the DarkGate Loader malware.
The campaign started in late August 2023, when Microsoft Teams phishing messages were seen being sent by two compromised external Office 365 accounts to other organizations.
These accounts were used to trick other Microsoft Teams users into downloading and opening a ZIP file named “Changes to the vacation schedule.”
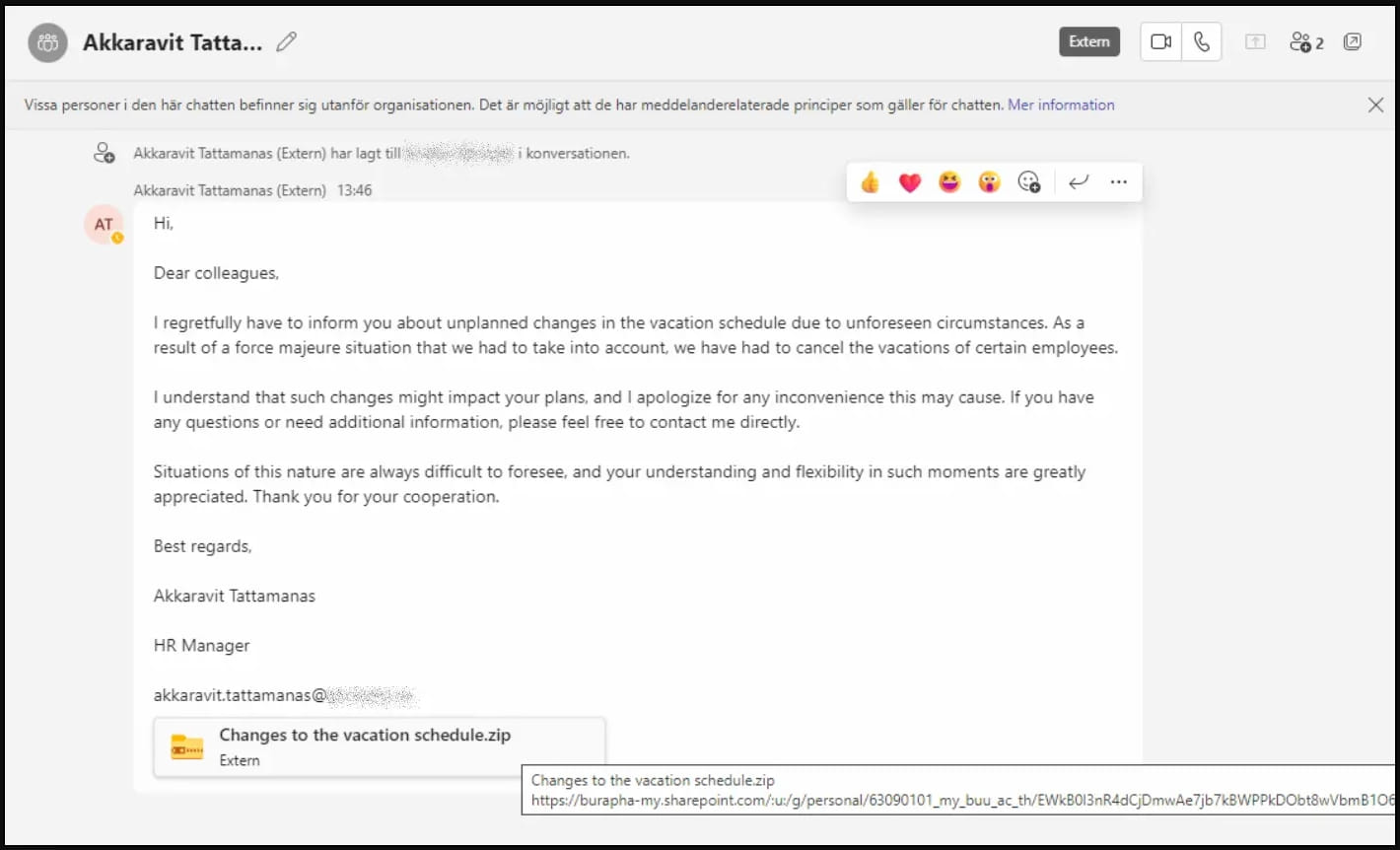
Clicking on the attachment triggers the download of the ZIP from a SharePoint URL and contains a LNK file masquerading as a PDF document.
Researchers at Truesec analyzed the Microsoft Teams phishing campaign and found that it contains malicious VBScript that triggers the infection chain that leads to a payload identified as the DarkGate Loader.
To try and evade detection, the download process utilizes Windows cURL to fetch the malware’s executable and script files.
The script arrived pre-compiled, hiding its malicious code in the middle of the file, beginning with distinguishable “magic bytes” associated with AutoIT scripts.
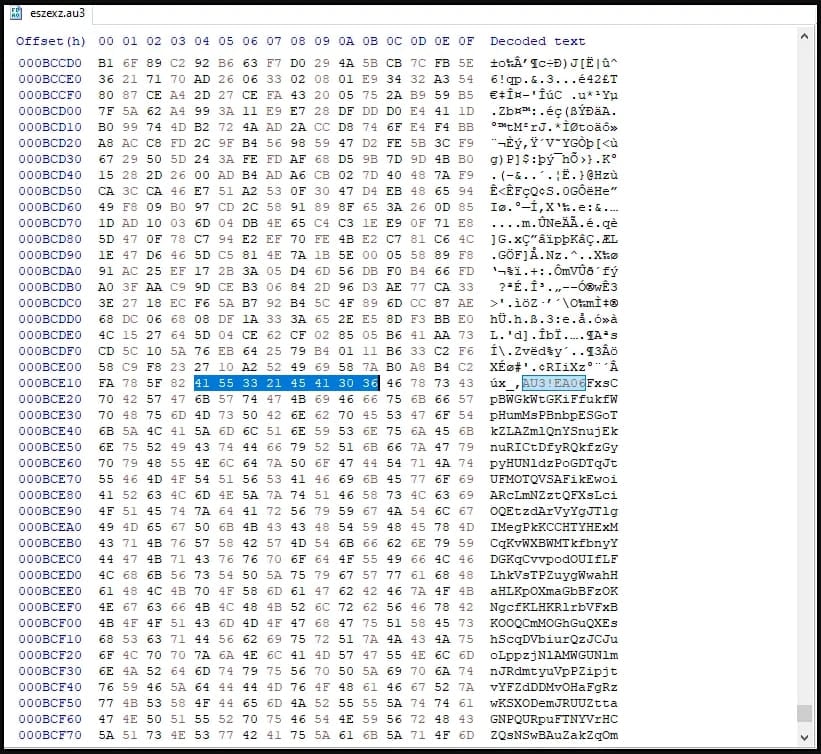
Before proceeding further, the script checks if the Sophos antivirus software is installed on the targeted machine, and if it’s not, it deobfuscates additional code and launches the shellcode.
The shellcode uses a technique called “stacked strings” to construct the DarkGate Windows executable and load it in memory.
Microsoft Teams phishing
The campaign seen by Truesec and Deutsche Telekom CERT utilizes compromised Microsoft Teams accounts to send the malicious attachments to other Teams organizations.
Microsoft Teams phishing was previously demonstrated in a June 2023 report by Jumpsec, who discovered a way to send malicious messages to other organizations through phishing and social engineering, which is similar to what we see in the reported attack.
Despite the stir caused by this discovery, Microsoft decided not to address the risk. Instead, recommending that admins apply safe configurations like narrow-scoped allow-lists and disable external access if communication with external tenants isn’t needed.
A tool that a Red Teamer released in July 2023 streamlined this Microsoft Teams phishing attack, further increasing the likelihood of it being abused in the wild.
However, there’s no indication that this method is involved in the attack chain of the recently observed campaign.
DarkGate opens up
DarkGate has been circulating since 2017, seeing limited use by a small circle of cybercriminals who used it against very specific targets.
It is a potent malware that supports a wide range of malicious activities, including hVNC for remote access, cryptocurrency mining, reverse shell, keylogging, clipboard stealing, and information stealing (files, browser data).
In June 2023, ZeroFox reported that someone claiming to be the original author of DarkGate attempted to sell access to the malware to ten people for the absurd cost of $100k/year.
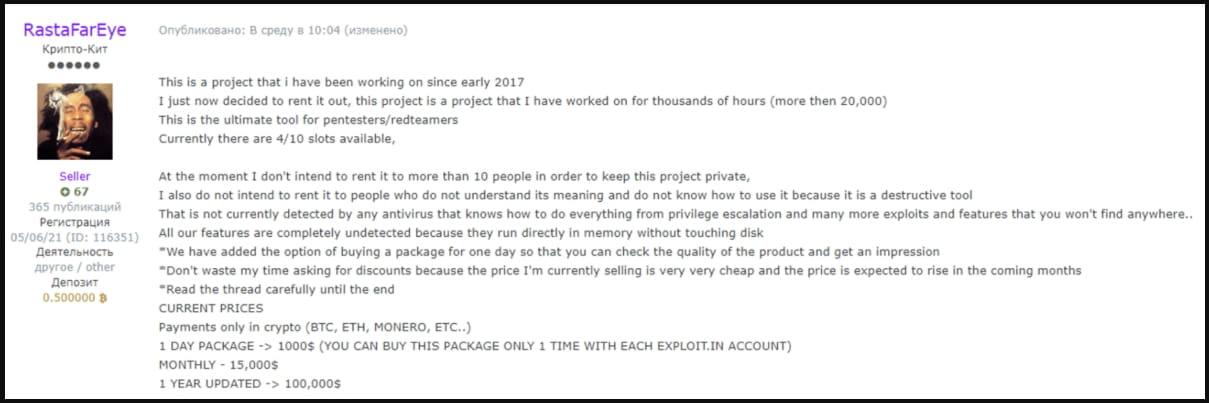
In the following months, there have been multiple reports of DarkGate distribution ramping up and using various channels, including phishing and malvertising.
While DarkGate may not be a widespread threat yet, its expanding targeting and adoption of multiple infection avenues make it an emerging threat to monitor closely.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


![[QILIN] - Ransomware Victim: vresystems[.]com 7 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

