Need To Know Key Takeaways From The Latest Phishing Attacks

These days, cyber threat actors continue to rely just as much on psychological manipulation in the form of convincing phishing emails as they do on technical hacks to infiltrate networks.
This article takes a look at some lessons from recent phishing attacks and highlights actionable tips to limit the risks of phishing affecting your company.
High-Profile Recent Phishing Attacks
Phishing is the number one way threat actors gain initial access to systems and networks. The most recent version of IBM’s Threat Intelligence report identified phishing as the initial infection vector in 41 percent of analyzed cyber incidents.
Here’s a look at a couple of high-profile recent phishing attacks and some lessons from them.
Malicious Microsoft Teams Chats
AT&T security researchers spotted a new phishing campaign that pushed DarkGate malware payloads via malicious Microsoft Teams chats. Threat actors, appearing as compromised Teams users, sent over 1,000 malicious chat invites.
Once recipients accepted and downloaded a disguised file, the malware would connect to a command-and-control server.
Takeaways from this incident include:
- Threat actors now extend the focus on phishing attacks beyond just email to incorporate direct messaging and group chats within team collaboration platforms. Increased reliance on these tools stems from the shift to remote work that the COVID-19 pandemic accelerated.
- Disabling external access in Microsoft Teams is crucial unless your business absolutely needs to allow external Microsoft Teams users to send messages to your employees.
Open Redirect Phishing via Indeed
An interesting phishing campaign from 2023 saw hacking group EvilProxy abusing open redirects from the Indeed employment site to target Microsoft 365 accounts. These open redirects are flaws in the site’s code that allow redirects to arbitrary locations by simply manipulating URLs. Executives and high-ranking employees received emails with seemingly real indeed.com links that linked them to copycat login pages for their Microsoft 365 accounts from which their login sessions were hijacked.
Some takeaways from this campaign are:
- Even large platforms like Indeed can have security lapses that make hackers’ jobs easier.
- Senior employees are lucrative targets for phishing campaigns because accessing their accounts often leads to easy access to sensitive data or communications.
NATO Summit Attendees
A mid-2023 phishing campaign saw threat actors targeting attendees of a NATO summit supporting Ukraine during its ongoing war against Russia. The hacking group, known as RomCom, set up a copy of the Ukrainian World Congress website using a .info domain (the genuine site uses .org). On the phony website, there are malicious documents that load malware onto victims’ systems once downloaded.
Lessons here are:
- Threat actors still regularly use replicas of legitimate websites with only slight deviations from the real site’s spelling (typo-squatting) to lure victims in. Carefully analyzing URLs is worth promoting for general phishing awareness.
- Phishing attacks are not solely motivated by profit; they are increasingly used in espionage and geopolitical cybercrime to gather sensitive information and disrupt operations in targeted countries or organizations.
What Organizations Can Do To Limit Phishing Risks
In the face of rampant phishing attacks that can cause large-scale data breaches, here are some ways you can limit phishing risks.
Employee Training & Awareness
Educated and aware employees serve as the first line of defense against phishing and other forms of social engineering. Effective training equips staff with essential theoretical knowledge and practical skills to recognize and avoid falling victim to phishing attempts.
Theoretical training helps your employees understand different phishing tactics used by attackers, such as email phishing, spear phishing, and whaling. This training should also cover company policies and procedures for dealing with suspicious emails, including who to contact and how to respond to phishing attacks.
Practical exercises help employees learn to spot tell-tale signs of phishing, such as suspicious email addresses, grammar mistakes, and urgent or threatening language. Conducting regular, unexpected phishing simulation exercises to test your employees’ readiness is good for reinforcing knowledge and awareness.
Advanced Email Filtering
While training users is worth the investment, depending on effective training to stop all phishing attacks is too risky. People can and will make mistakes. Advanced email filtering is a technological solution that reduces the likelihood of phishing attacks succeeding and minimizes your reliance on user vigilance alone.
Elements that make modern email filtering solutions better include:
- Natural language processing (NLP) techniques that enable email filters to understand the context and intent of the text within emails.
- Machine learning algorithms that recognize normal communication patterns within your organization and spot emails that deviate from these patterns.
- URL analysis and reputation scoring systems to assess the trustworthiness of links and block emails containing links to known phishing or malware sites. Some tools inspect the content of the webpage linked by the URL within emails for suspicious elements, including phishing forms designed to capture credentials or personal data.
- Attachment scanning scrutinizes files attached to emails or downloaded from links and helps to detect malware, ransomware, or other malicious payloads before one of your unsuspecting users opens them. You can use a security automation platform to automatically scan and respond to suspicious attachments.
Multi-Factor Authentication (MFA)
Multi-factor authentication calls for users to provide two or more verification factors to gain access to an account, system, or application. The link to reducing phishing risks here is that even if a phishing attack successfully dupes a user into revealing their password, the additional authentication factors add an extra barrier against unauthorized access.
Having a user’s password compromised by phishing is a far less severe outcome than sensitive company or customer data being accessed or stolen.
With a security automation copilot like Blink, you can automatically check that employers are actually enabling MFA across devices. For instance, the automated workflow below reports on any MFA gaps in Okta.
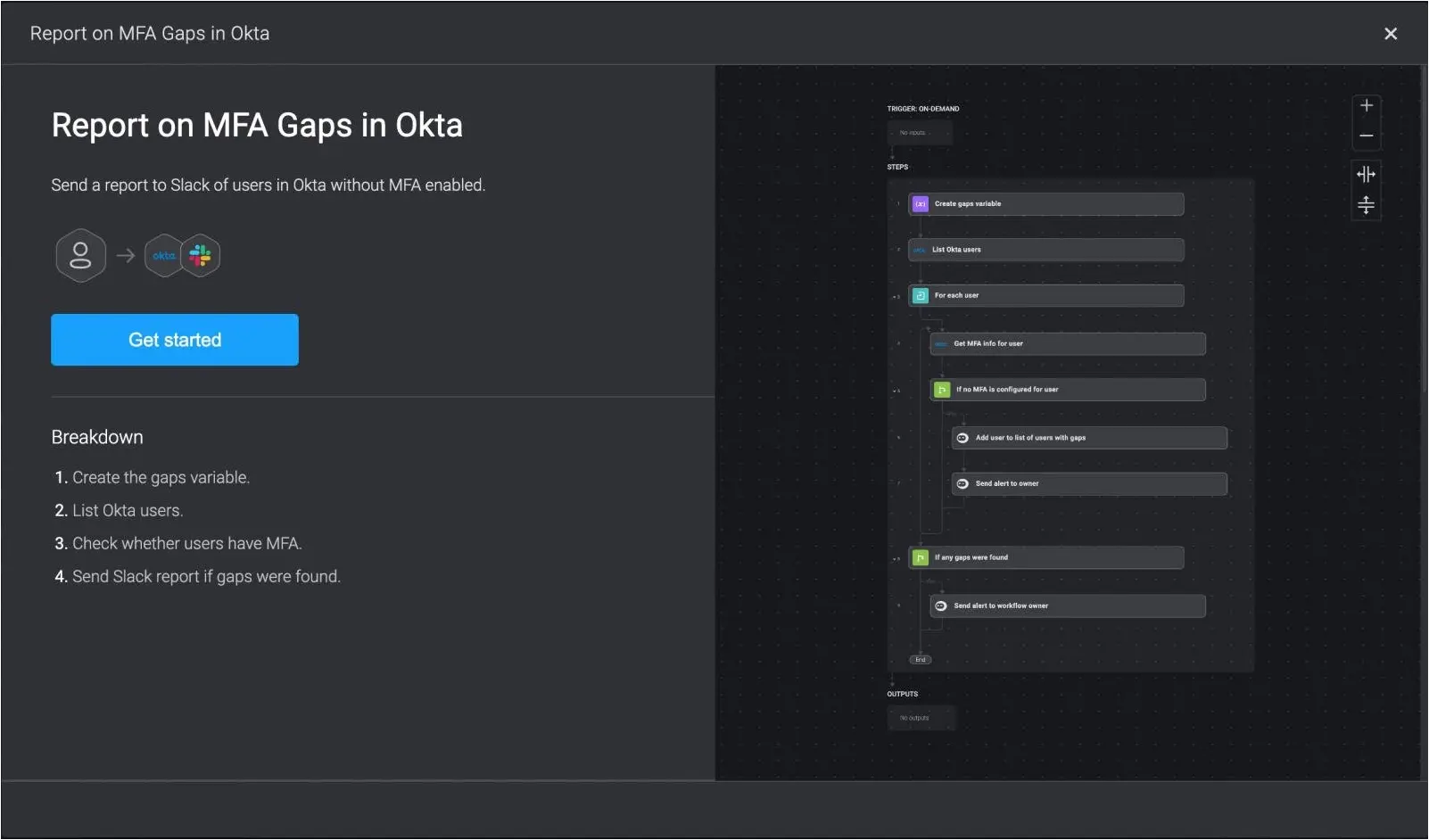
How Security Automation Can Help
Building automated security workflows limits phishing risks by streamlining incident response. An effective automated email security workflow can facilitate automatic scanning, instant alerts, and responses to suspected phishing incidents (e.g. by notifying internal teams or Slack channels).
This type of quickfire response ensures swift action without manual intervention to mitigate any potential phishing damage.
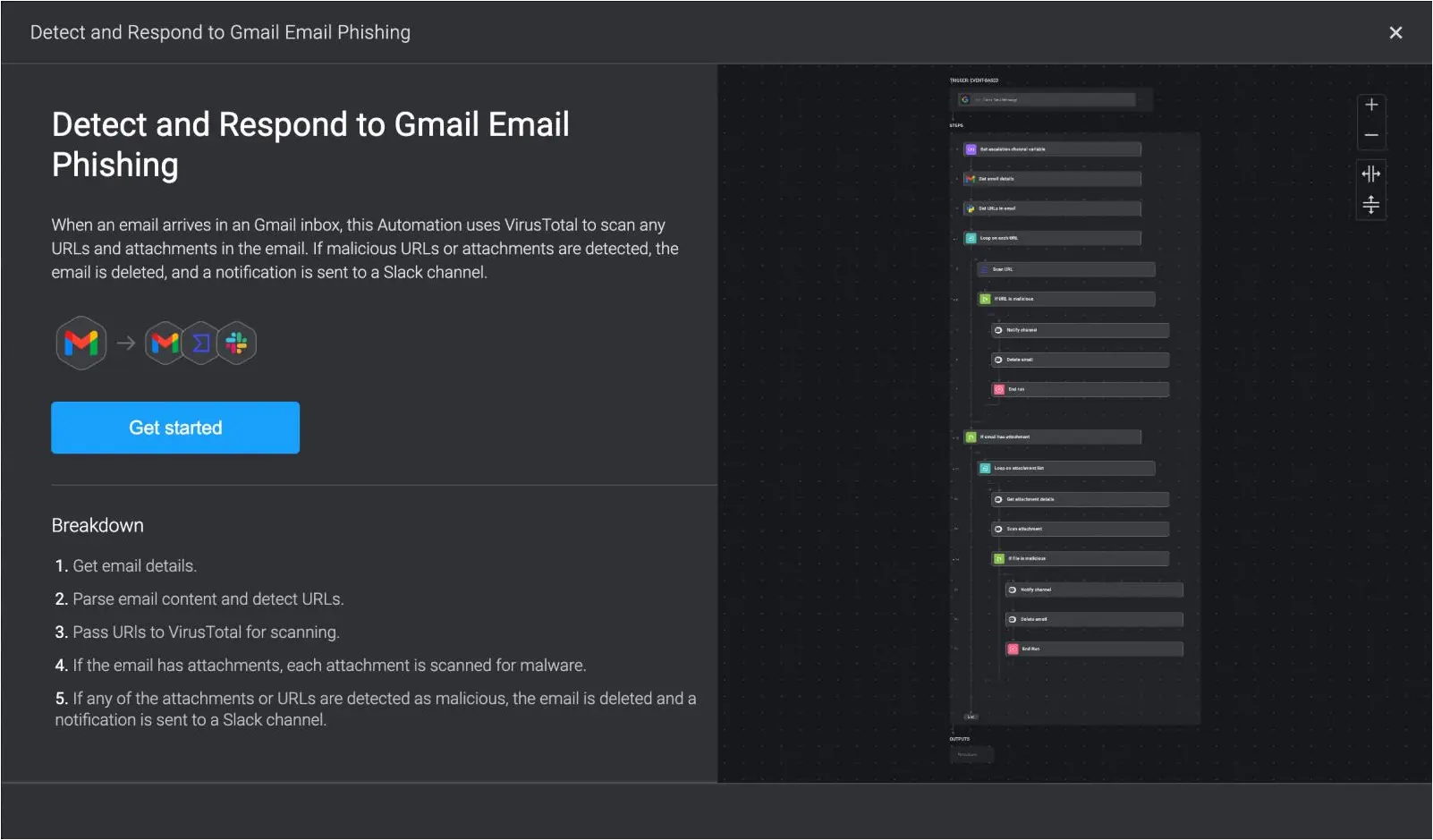
With Blink, anyone can generate an automated security workflow – simply by typing a prompt.
Whether it’s securing MFA gaps or responding to Gmail phishing attacks, Blink enables you to start automating without the need to code. See it in action and schedule a demo today.
Sponsored and written by Blink Ops.
