NERVE – Network Exploitation, Reconnaissance & Vulnerability Engine
NERVE is a vulnerability scanner tailored to find low-hanging fruit level vulnerabilities, in specific application configurations, network services, and unpatched services.
It is not a replacement for Qualys, Nessus, or OpenVAS. It does not do authenticated scans, and operates in black-box mode only.
NERVE will do “some” CVE checks, but this is primarily coming from version fingerprinting.
Example of some of NERVE’s detection capabilities:
- Interesting Panels (Solr, Django, PHPMyAdmin, etc.)
- Subdomain takeovers
- Open Repositories
- Information Disclosures
- Abandoned / Default Web Pages
- Misconfigurations in services (Nginx, Apache, IIS, etc.)
- SSH Servers
- Open Databases
- Open Caches
- Directory Indexing
- Best Practices
Features
NERVE offers the following features:
- Dashboard (With a Login interface)
- REST API (Scheduling assessments, Obtaining results, etc)
- Notifications
- Slack
- Webhook
- Reports
- TXT
- CSV
- HTML
- Customizable scans
- Configurable intrusiveness levels
- Scan depth
- Exclusions
- DNS / IP Based
- Threading
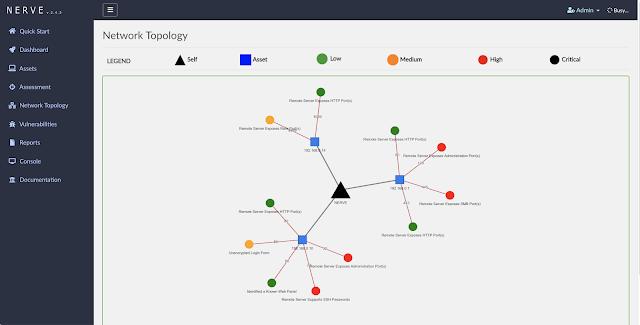
- Network Topology Graphs
We put together Graphical User Interface primarily for ease of use, but we will be putting more emphasis on detections and new signatures than creating full blown user interface.
Prerequisites
NERVE will install all the prerequisites for you automatically if you choose the Server installation (CentOS 7.x and Ubuntu 18.x were tested) (by using install/setup.sh script). It also comes with a Dockerfile for your convenience.
Keep in mind, NERVE requires python 3.x and libraries such as python-nmap, requests, etc. and needs root access for the initial setup.
Installation
Deployment Recommendation
The best way to deploy it, is to run it against your infrastructure from multiple regions (e.g. multiple instances of NERVE, in multiple countries), and toggle continuous mode so that you can catch short-lived vulnerabilities in dynamic environments/cloud.
We typically recommend not to whitelist the IP addresses where NERVE will be initiating the scans from, to truly test your infrastructure from an attacker standpoint.
To make NERVE fairly lightweight, there’s no use of a database other than Redis.
If you want to store your vulnerabilities long term, we recommend using the Web hook feature. At the end of each scan cycle, NERVE will dispatch a JSON payload to an endpoint of your choice, and you can then store it in a database for further analysis.
Here are the high level steps we recommend to get the most optimal results:
- Deploy NERVE on 1 or more servers.
- Create a script that fetches your Cloud services (such as AWS Route53 to get the DNS, AWS EC2 to get the instance IPs, AWS RDS to get the database IPs, etc.) and maybe a static list of IP addresses if you have assets in a Datacenter.
- Call NERVE API (
POST /api/scan/submit) and schedule a scan using the assets you gathered in step #2. - Fetch the results programmatically and act on them (SOAR, JIRA, SIEM, etc.)
- Add your own logic (exclude certain alerts, add to database, etc.)
Docker
Clone the repository
git clone [email protected]:PaytmLabs/nerve.git && cd nerve
Build the Docker image
docker build -t nerve .
Create a container from the image
docker run -e username="YOUR_USER" -e password="YOUR_PASSWORD" -d -p 80:8080 nerve
In your browser, navigate to http://ip.add.re.ss:80 and login with the credentials you specified to in the previous command.
Server
Navigate to /opt
cd /opt/
Clone the repository
git clone [email protected]:PaytmLabs/nerve.git && cd nerve
Run Installer (requires root)
bash install/setup.sh
Check NERVE is running
systemctl status nerve
In your browser, navigate to http://ip.add.re.ss:8080 and use the credentials printed in your terminal.
Security
There are a few security mechanisms implemented into NERVE you need to be aware of.
- Content Security Policy – A response header which controls where resource scan be loaded from.
- Other Security Policies – These Response headers are enabled: Content-Type Options, X-XSS-Protection, X-Frame-Options, Referer-Policy
- Brute Force Protection – A user will get locked if more than 5 incorrect login attempts are made.
- Cookie Protection – Cookie security flags are used, such as SameSite, HttpOnly, etc.
If you identify a security vulnerability, please submit a bug to us on GitHub.
Usage
To learn about NERVE (GUI, API, etc.) we advise you to check out the documentation available to you via the platform. Once you deploy it, authenticate and on the left sidebar you will find a documentation link for API and GUI usage.
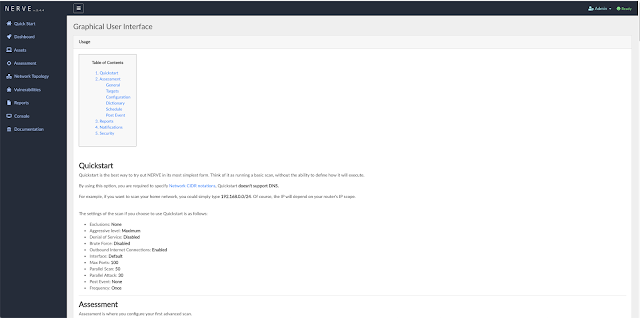
GUI Documentation
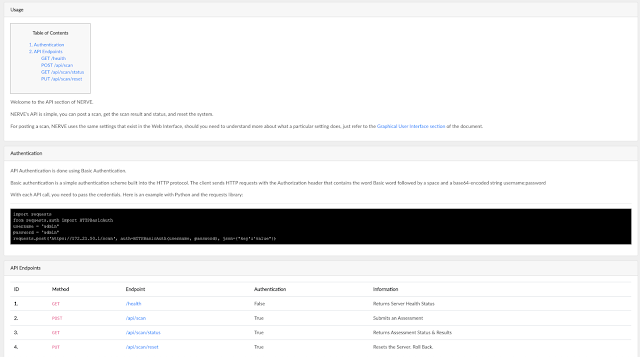
API Documentation
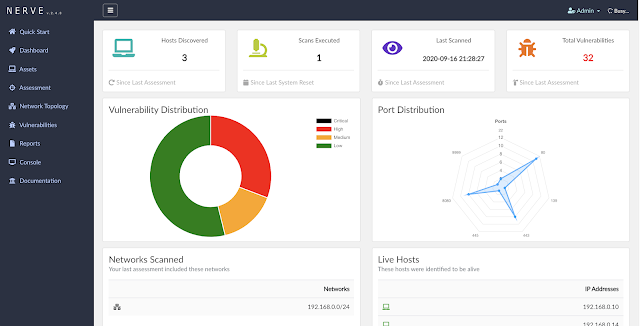
Screenshots
Login Screen
Dashboard Screen
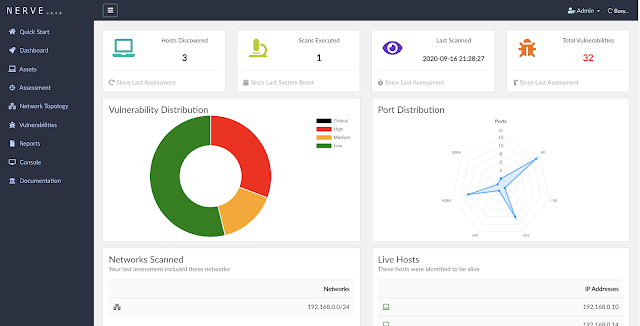
Assessment Configuration
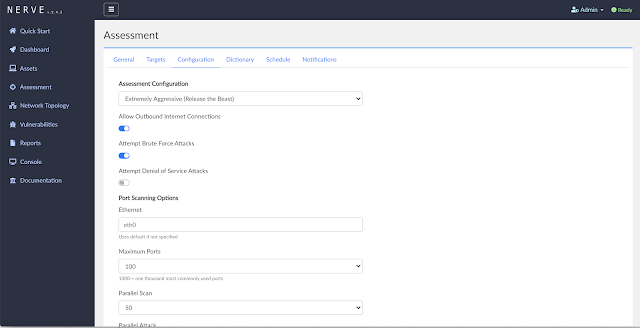
API Documentation
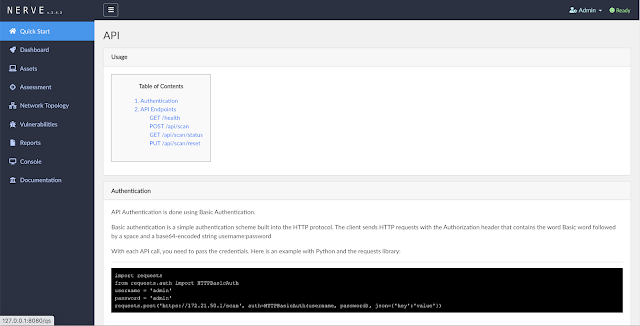
Reporting
Network Map
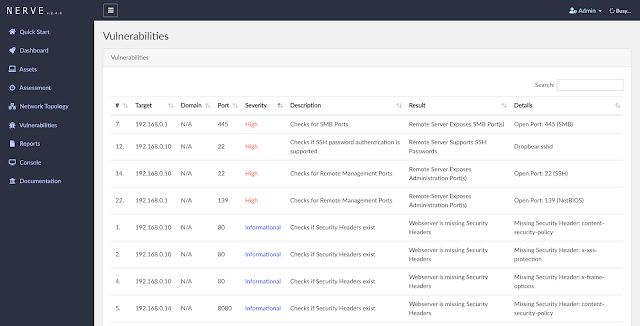
Vulnerability page
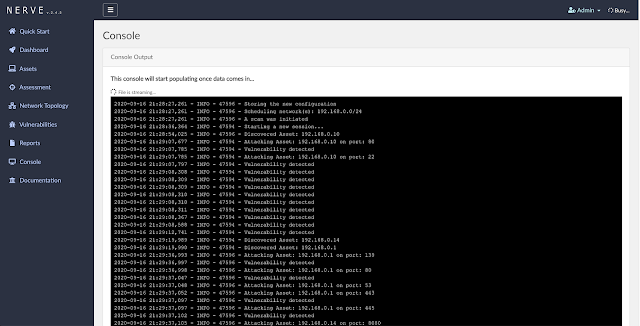
Log Console
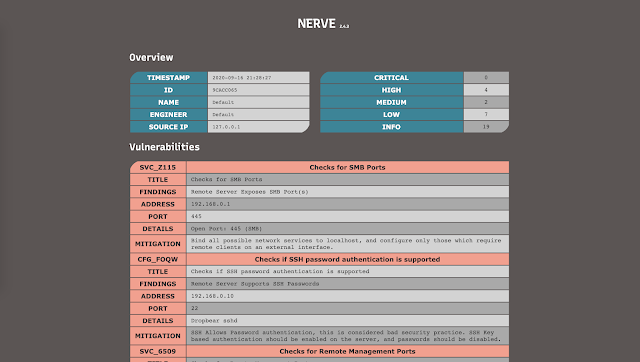
HTML Report
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[QILIN] - Ransomware Victim: Culver's Lawn & Landscape, Inc[.] 14 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

