New BiBi-Linux wiper malware targets Israeli orgs in destructive attacks

A new malware wiper known as BiBi-Linux is being used to destroy data in attacks targeting Linux systems belonging to Israeli companies.
Security Joes’ Incident Response team discovered the malicious payload while investigating the breach of an Israeli organization’s network. Currently, only two security vendors’ malware scanning engines detect BiBi-Linux as malicious, according to VirusTotal.
The malware reveals its true nature by not dropping a ransom note or providing victims with a way to reach out to the attackers to negotiate payment for a decryptor, even though it fakes file encryption,
“This new threat does not establish communication with remote Command & Control (C2) servers for data exfiltration, employ reversible encryption algorithms, or leave ransom notes as a means to coerce victims into making payments,” said Security Joes.
“Instead, it conducts file corruption by overwriting files with useless data, damaging both the data and the operating system.”
The payload (an x64 ELF executable named bibi-linux.out) found on the victim’s systems allows the attackers to choose what folders to encrypt via command-line parameters.
It can completely wipe a compromised device’s operating system when run with root privileges if the attackers do not provide a target path, as it will attempt to delete the entire ‘/’ root directory.
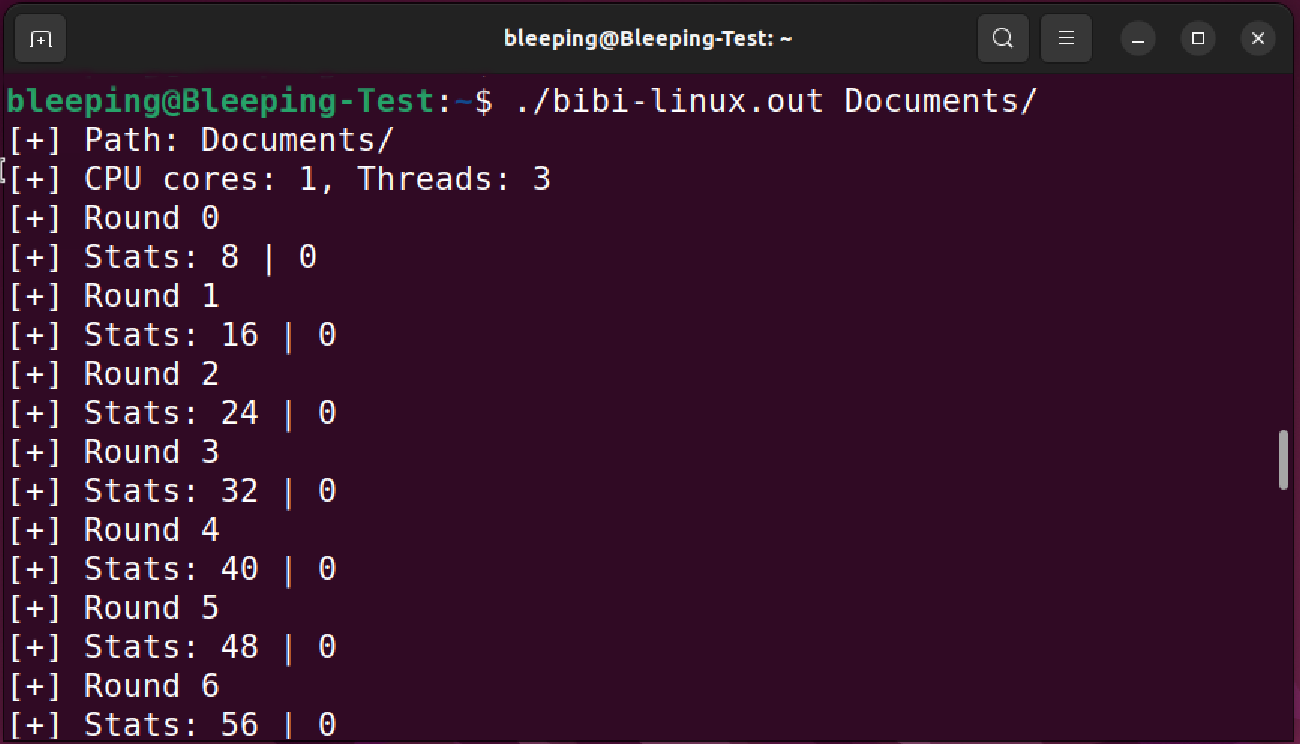
BiBi-Linux uses multiple threads and a queue system for improved speed and effectiveness. It will overwrite files’ contents to destroy them, renaming them using a ransom name and an extension made out of the ‘BiBi’ string (Bibi is a nickname used for Israel’s Prime Minister, Benjamin Netanyahu) followed by a number.
As seen by BleepingComputer, the number appended to the extension is the number of rounds a file has been wiped.
The wiper sample discovered by Security Joes also features no obfuscation, packing, or other protective measures, making malware analysts’ jobs much easier.
This shows the threat actors are not concerned about their tools being captured and dissected, instead focusing on maximizing their attack’s impact.
Destructive malware has also been used extensively by Russian threat groups to target the systems of Ukrainian organizations since Russia invaded Ukraine in February 2022.
The list of wiper malware used to target Ukraine includes the likes of DoubleZero, HermeticWiper, IsaacWiper, WhisperKill, WhisperGate, CaddyWiper, and AcidRain.
For instance, Russian Sandworm military hackers deployed five different data-wiping malware strains on the network of the country’s national news agency (Ukrinform) in January.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.



