New Dark Power ransomware claims 10 victims in its first month

A new ransomware operation named ‘Dark Power’ has appeared, and it has already listed its first victims on a dark web data leak site, threatening to publish the data if a ransom is not paid.
The ransomware gang’s encryptor has a compilation date of January 29, 2023, when the attacks started.
Furthermore, the operation has not been promoted on any hacker forums or dark web spaces yet; hence it’s likely a private project.
According to Trellix, which analyzed Dark Power, this is an opportunistic ransomware operation that targets organizations worldwide, asking for relatively small ransom payments of $10,000.
Dark Power attack details
The Dark Power payload was written in Nim, a cross-platform programming language with several speed-related advantages, making it suitable for performance-critical applications like ransomware.
Also, because Nim is only now starting to get more popular among cybercriminals, it is generally considered a niche choice that is unlikely to be detected by defense tools.
Trellix does not provide details regarding Dark Power’s infection point, but it could be an exploit, phishing emails, or other means.
Upon execution, the ransomware creates a randomized 64-character long ASCII string for initializing the encryption algorithm with a unique key on each execution.
Next, the ransomware terminates specific services and processes on the victim’s machine to free up files for encryption and minimize the chances of anything blocking the file-locking process.
During that stage, the ransomware also stops the Volume Shadow Copy Service (VSS), data backup services, and anti-malware products in its hardcoded list.
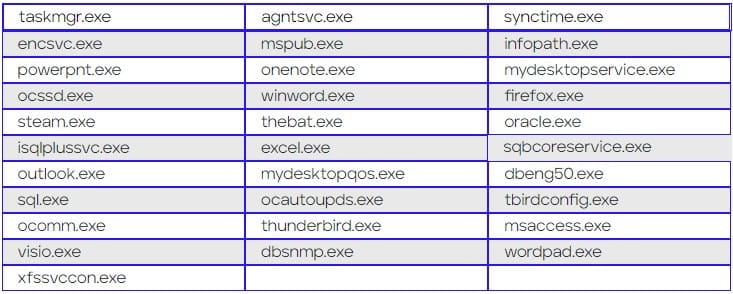
After all of the above services are killed, the ransomware sleeps for 30 seconds and clears the console and Windows system logs to prevent analysis from data recovery experts.
The encryption uses AES (CRT mode) and the ASCII string generated upon launch. The resulting files are renamed with the “.dark_power” extension.
Interestingly, two versions of the ransomware circulated in the wild, each with a different encryption key scheme.
The first variant hashes the ASCII string with the SHA-256 algorithm and then splits the result into two halves, using the first as the AES key and the second as the initialization vector (nonce).
The second variant uses the SHA-256 digest as the AES key and a fixed 128-bit value as the encryption nonce.
System-critical files like DLLs, LIBs, INIs, CDMs, LNKs, BINs, and MSIs, as well as the Program Files and web browser folders, are excluded from encryption to keep the infected computer operational, thus allowing the victim to view the ransom note and contact the attackers.
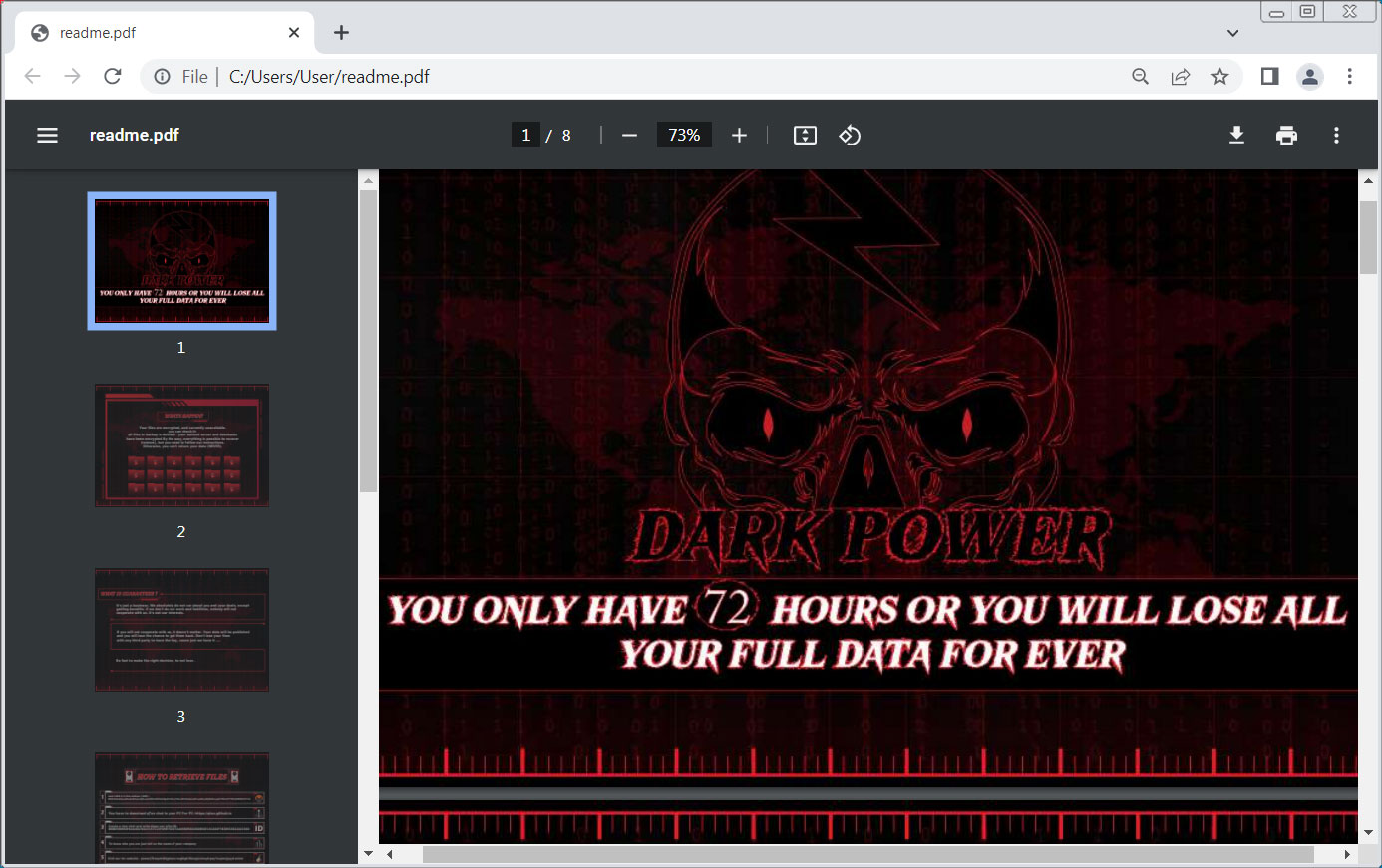
The ransom note, which was last modified on February 9, 2023, gives victims 72 hours to send $10,000 in XMR (Monero) to the provided wallet address to get a working decryptor.
Dark Power’s ransom note stands out compared to other ransomware operations as it is an 8-page PDF document containing information about what happened and how to contact them over the qTox messenger.
Victims and activity
When writing this, the Tor site of Dark Power was offline. However, it is not uncommon for ransomware portals to go offline periodically as negotiations with victims develop.
Trellix reports that it has seen ten victims from the USA, France, Israel, Turkey, the Czech Republic, Algeria, Egypt, and Peru, so the targeting scope is global.
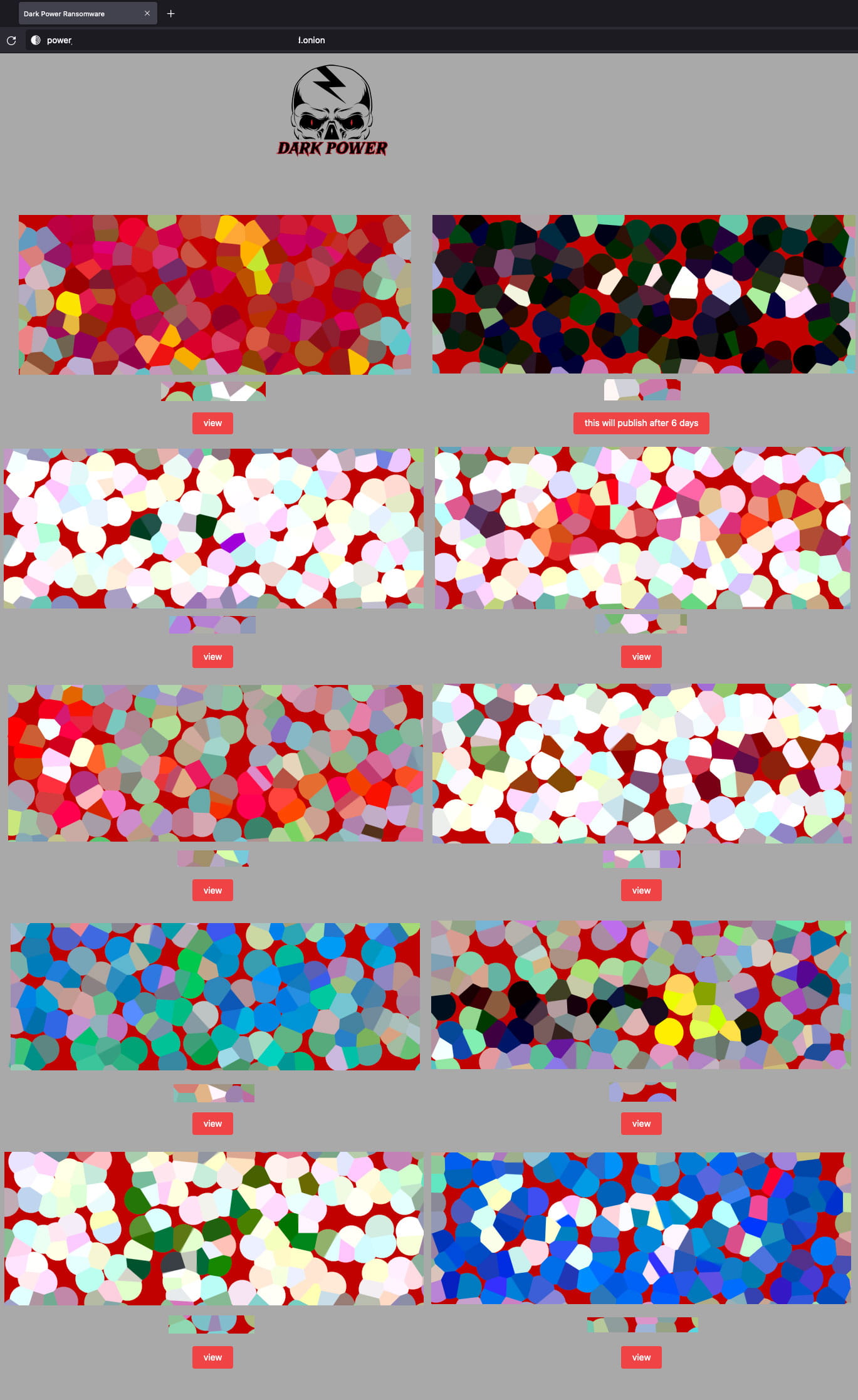
The Dark Power group claims to have stolen data from the networks of these organizations and threatens to publish them if they don’t pay the ransom, so it’s yet another double-extortion group.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.






