New Hunters International ransomware possible rebrand of Hive

A new ransomware-as-a-service brand named Hunters International has emerged using code used by the Hive ransomware operation, leading to the valid assumption that the old gang has resumed activity under a different flag.
This theory is supported by analysis of the new encryptor revealing multiple code overlaps between the two ransomware gangs.
Hunters in denial
Security researchers analyzing a sample of the Hunters International malware discovered a striking resemblance to the code used in Hive ransomware attacks.
More specifically, malware analyst and reverse engineer rivitna, who first spotted the new encryptor, came to the conclusion that Hunters International malware was a sample of Hive ransomware version 6.
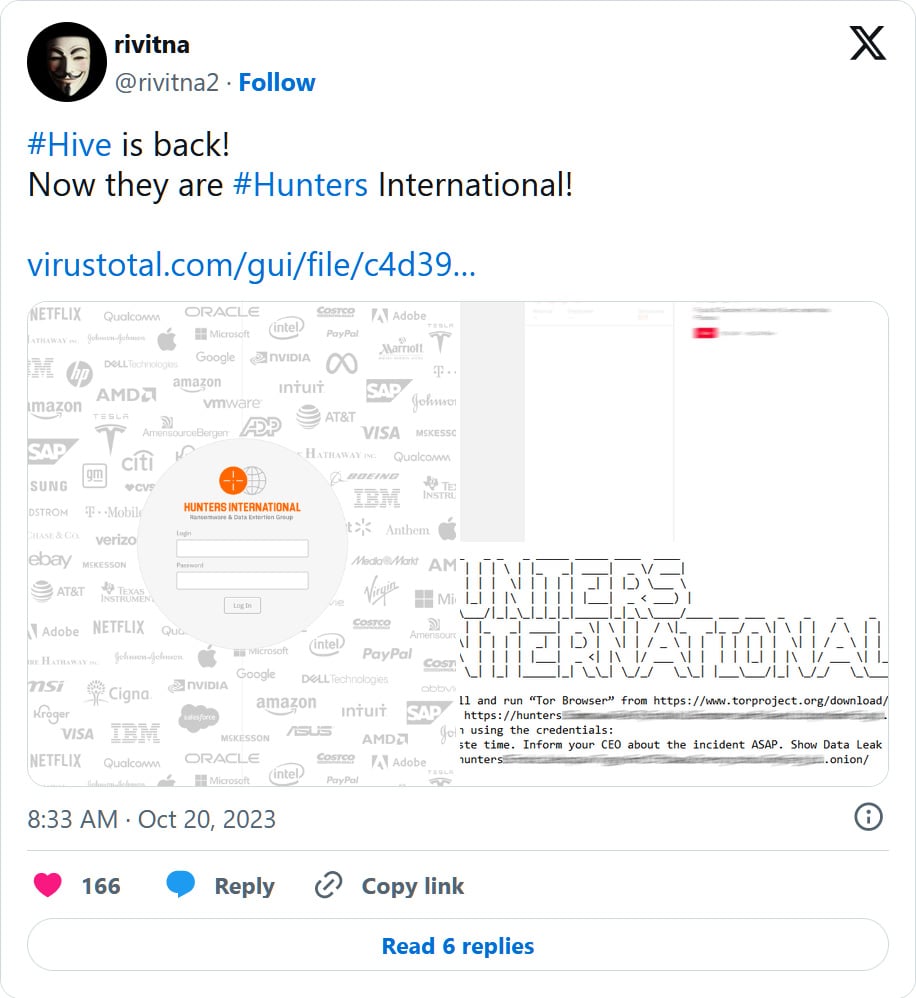
source: rivitna
In replies to the tweet above, security researcher Will Thomas shares that he found “some maintained Hive ransomware strings” in the Hunters International code.
Looking closer at the Hunters International sample, the researcher discovered code overlaps and similarities that match more than 60% of the code in Hive ransomware.
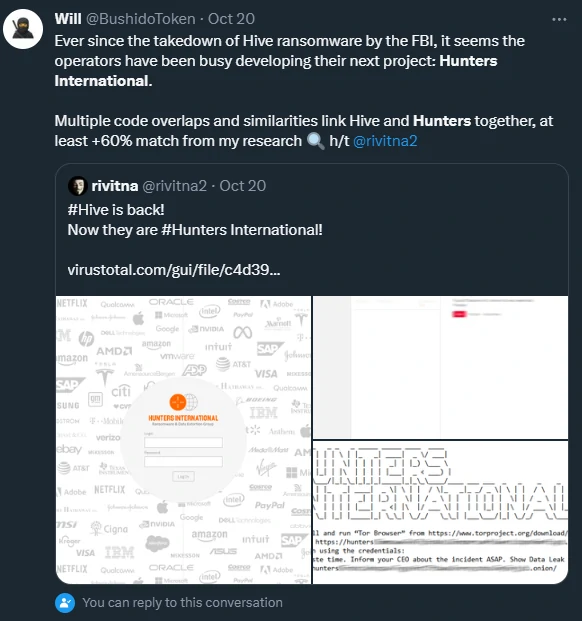
source: Bushido Token
However, the Hunters International group is denying the researchers’ “allegations” saying that they are a new service on the ransomware scene who purchased the encryptor source code from the Hive developers.
“All of the Hive source codes were sold including the website and old Golang and C versions and we are those who purchased them,” the Hunters International gang says.
Hive International claims that Hive’s code contained “a lot of mistakes that caused unavailability for decryption in some cases” but they fixed it.
Furthermore, the new gang says that encryption is not the main goal of their operation, instead focusing on stealing data as leverage when extorting victims into paying a ransom demand.
The Hunters International encryptor
From analysis by BleepingComputer, Hunters International’s encryptor appends the “.LOCKED” extension to the processed files.
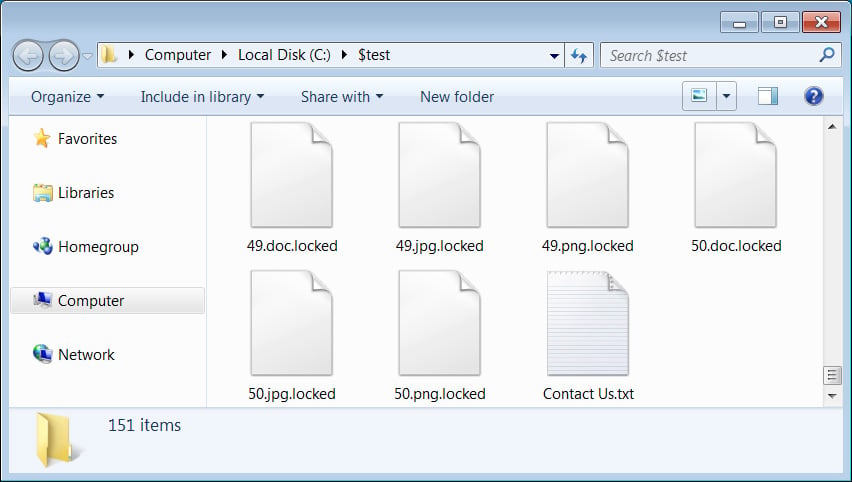
source: BleepingComputer
The malware leaves in each directory a plaintext file named “Contact Us.txt” with instructions for the victim to contact the attacker over Tor, through a chat page that is protected by a login specific for each victim.
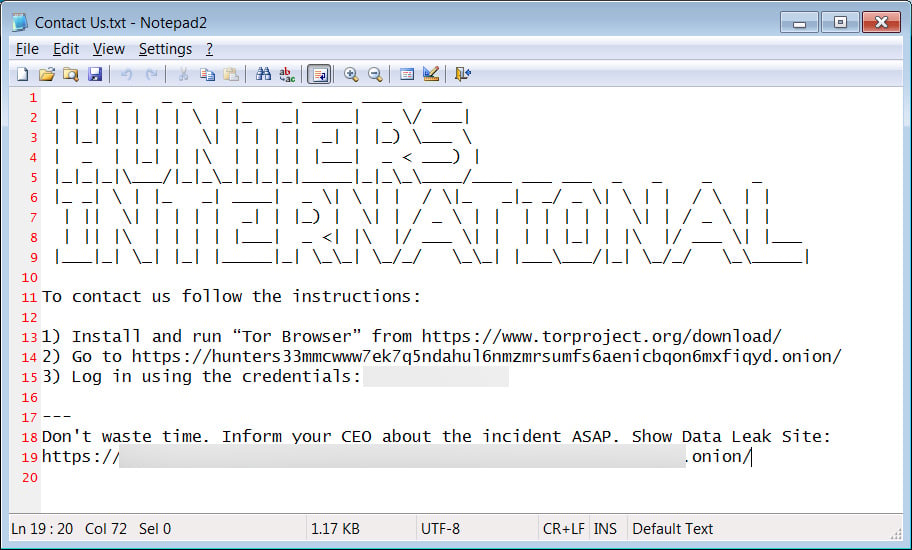
source: BleepingComputer
At the moment, their data leak site lists only one victim, a school in the UK, from where the attackers claim to have stolen almost 50,000 files consisting of data about students and teachers along with network and web credentials.
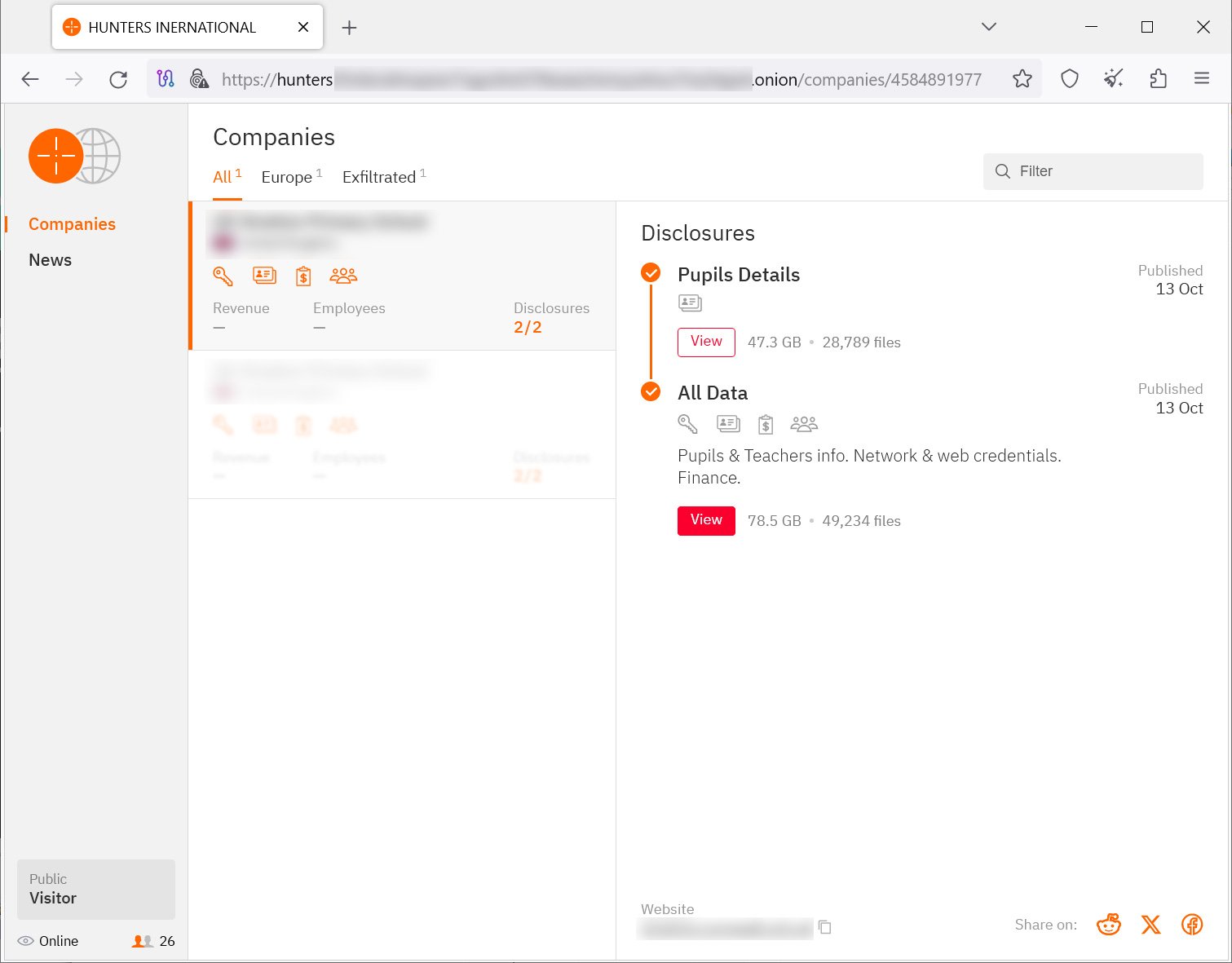
source: BleepingComputer
As spotted by MalwareHunterTeam, Hunters International’s data leak site shows a set of messages, likely in an attempt to share with the world that they mean serious business and “hunting” for victims and extorting them is their main purpose.
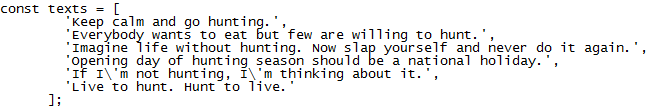
source: MalwareHunterTeam
It remains to be seen what fate awaits Hunters International’s but with one victim published on their data leak site, the group does not appear to be too active.
Hive ransomware’s demise
Whether Hive ransomware sold the source code to other cybercriminals or not, remains unknown at the moment but the gang’s operations came to a sudden stop after its Tor payment and data leak site were seized in an international operation in January.
Disrupting the ransomware operation, which had 250 affiliates, was possible after the FBI had infiltrated the gang’s infrastructure and monitored the activity for six months, since July 2022.
According to the FBI, the gang breached more than 1,300 companies and recived ransom payments of about $100 million.
The agency’s activity allowed it to provide more than 1,300 decryption keys to Hive ransomware victims that had been encrypted before and after the FBI gained access to the attacker’s environments.
