New SprySOCKS Linux malware used in cyber espionage attacks

A Chinese espionage-focused hacker tracked as ‘Earth Lusca’ was observed targeting government agencies in multiple countries, using a new Linux backdoor dubbed ‘SprySOCKS.’
Trend Micro’s analysis of the novel backdoor showed that it originates from the Trochilus open-source Windows malware, with many of its functions ported to work on Linux systems.
However, the malware appears to be a mixture of multiple malware as the SprySOCKS’ command and control server (C2) communication protocol is similar to RedLeaves, a Windows backdoor. In contrast, the implementation of the interactive shell appears to have been derived from Derusbi, a Linux malware.
Earth Lusca attacks
Earth Lusca remained active throughout the first half of the year, targeting key government entities focused on foreign affairs, technology, and telecommunications in Southeast Asia, Central Asia, the Balkans, and worldwide.
Trend Micro reports seeing exploitation attempts for several n-day unauthenticated remote code execution flaws dated between 2019 and 2022, impacting internet-exposed endpoints.

These flaws are exploited to drop Cobalt Strike beacons, which allow remote access to the breached network. This access is used to spread laterally on the network while exfiltrating files, stealing account credentials, and deploying additional payloads, like ShadowPad.
The threat actors also use the Cobalt Strike beacons to drop the SprySOCKS loader, a variant of the Linux ELF injector called “mandibule,” which arrives on targeted machines in the form of a file named ‘libmonitor.so.2.’
Trend Micro’s researchers say the attackers adapted mandibule for their needs, but in a somewhat rushed manner, leaving debug messages and symbols behind.
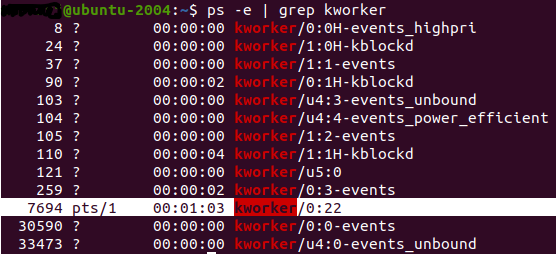
The loader runs under the name “kworker/0:22” to avoid detection by resembling a Linux kernel worker thread, decrypts the second-stage payload (SprySOCKS), and establishes persistence on the infected computer.
SprySOCKS capabilities
The SprySOCKS backdoor uses a high-performance networking framework called ‘HP-Socket’ for its operation, while its TCP communications with the C2 are AES-ECB encrypted.
The main backdoor functionalities of this novel malware include:
- Collecting system information collection (OS details, memory, IP address, group name, language, CPU),
- starting an interactive shell that uses the PTY subsystem,
- listing network connections,
- managing SOCKS proxy configurations,
- and performing basic file operations (uploading, downloading, listing, deleting, renaming, and creating directories.)
The malware also generates a client ID (victim number) using the MAC address of the first listed network interface and some CPU features and then converts it to a 28-byte hexadecimal string.
Trend Micro reports having sampled two versions of SprySOCKS, v1.1 and v.1.3.6, indicating active development of the malware.
The recommended priority for organizations should be to apply the available security updates on public-facing server products, which, in this case, would prevent initial compromise from Earth Lusca.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[GLOBAL] - Ransomware Victim: loraincountyauditor[.]gov 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

