New stealthy and modular Deadglyph malware used in govt attacks

A novel and sophisticated backdoor malware named ‘Deadglyph’ was seen used in a cyberespionage attack against a government agency in the Middle East.
The Deadglyph malware is attributed to the Stealth Falcon APT (aka Project Raven or FruityArmor), a state-sponsored hacking group from the United Arab Emirates (UAE).
The hacking group has been known for targeting activists, journalists, and dissidents for almost a decade.
In a new report released at the LABScon cybersecurity conference, ESET researcher Filip Jurčacko shares analysis of the new modular malware and how it infects Windows devices.
Deadglyph attacks
ESET does not have insight into the means of initial infection, but it is suspected that a malicious executable, possibly a program installer, is used.
However, ESET obtained most of the components of the infection chain to paint a picture of how the malware operates and attempts to evade detection.
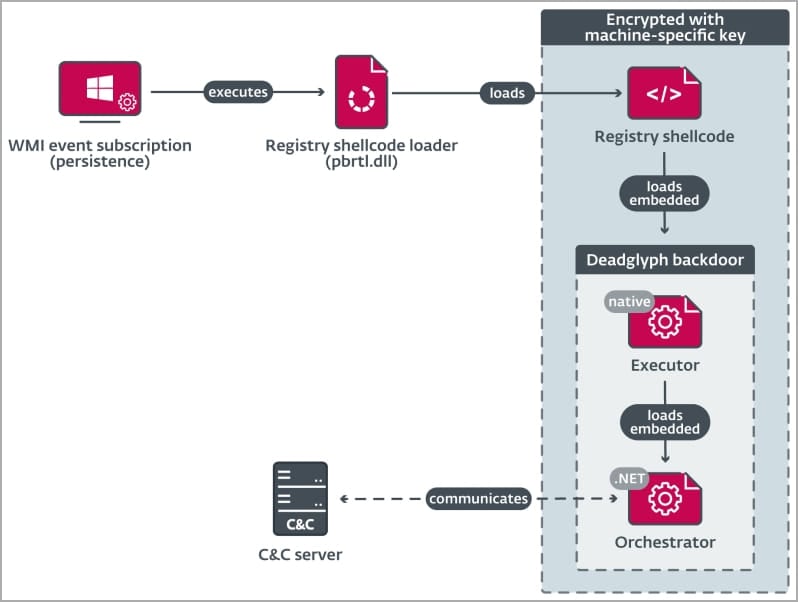
Deadglyph’s loading chain begins with a registry shellcode loader (DLL) that extracts code from the Windows registry to load the Executor (x64) component, which in turn loads the Orchestrator (.NET) component.
Only the initial component exists on the compromised system’s disk as a DLL file, minimizing the likelihood of detection.
ESET says the loader will load the shellcode from the Windows Registry, which is encrypted to make analysis more challenging.
As the DLL component is stored on the filesystem, it is more likely to be detected. Due to this, the threat actors utilized a homoglyph attack in the VERSIONINFO resource using distinct Greek and Cyrillic Unicode characters to mimic Microsoft’s information and appear as legitimate Windows file.
“We spotted a homoglyph attack mimicking Microsoft Corporation in the VERSIONINFO resource of this and other PE components,” explains the ESET report.
“This method employs distinct Unicode characters that appear visually similar, but in this case not identical, to the original characters, specifically Greek Capital Letter San (U+03FA, Ϻ) and Cyrillic Small Letter O (U+043E, о) in Ϻicrоsоft Corpоratiоn.
The Executor component loads AES-encrypted configurations for the backdoor, initializes the .NET runtime on the system, loads the .NET part of the backdoor, and acts as its library.
Finally, the Orchestrator is responsible for command and control server (C2) communications, using two modules for the task, ‘Timer’ and ‘Network.’
If the backdoor fails to establish communications with the C2 server after a determined period, it triggers a self-removal mechanism to prevent its analysis by researchers and cybersecurity experts.
A modular malware
The Deadglyph malware is modular, meaning it will download new modules from the C2 that contain different shellcodes to be executed by the Executor component.
Using a modular approach allows the threat actors to create new modules as needed to tailor attacks, which can then be pushed down to victims to perform additional malicious functionality.
These modules have Windows and custom Executor APIs at their disposal, with the latter offering 39 functions that make it possible to perform file operations, load executables, access Token Impersonation, and perform encryption and hashing.
ESET believes there are nine to fourteen different modules but could only obtain three: a process creator, an info collector, and a file reader.
The information collector uses WMI queries to feed the Orchestrator with the following information about the compromised system:
- operating system
- network adapters
- installed software
- drives
- services
- drivers
- processes
- users
- environment variables
- security software
The process creator is a command execution tool that executes specified commands as a new process and gives the result to the Orchestrator.
The file reader module reads the content of files and passes it to the Orchestrator, while it also gives the operators the option to delete the file after reading.
Although ESET was only able to uncover only a fraction of the malware’s capabilities, it’s clear that Stealth Falcon’s Deadglyph is a formidable threat.
Without detailed information regarding the initial infection, offering specific defense strategies against the malware is impossible.
For now, defenders can rely on the existing IoCs released in the report.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[QILIN] - Ransomware Victim: www[.]nuphoton[.]com 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)