Vhosts-Sieve – Searching For Virtual Hosts Among Non-Resolvable Domains
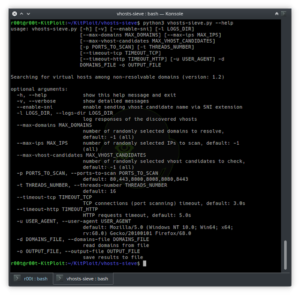
Searching for virtual hosts among non-resolvable domains.Installationgit clone https://github.com/dariusztytko/vhosts-sieve.gitpip3 install -r vhosts-sieve/requirements.txtUsageGet a list of subdomains (e.g. using Amass)$ amass...