Patch Tuesday – August 2020
120 Vulnerabilities Patched in Microsoft’s August 2020 Update Tuesday (2020-Aug Patch Tuesday)

August 2020 brings along patches for 120 vulnerabilities within the standard set of Microsoft products (Windows, Office, Browsers, and Developer Tools such as .NET Framework, ASP.NET, and Visual Studio). Among the crowd are two vulnerabilities: CVE-2020-1464, and CVE-2020-1380 that are noted as being exploited in the wild. The good news is that the remediation process behind those two vulnerabilities are fairly straight forward, which allows us to place a bit of focus on some additional vulnerabilities that stray from normal practice.
Microsoft CVE-2020-1472: Netlogon Elevation of Privilege Vulnerability (AttackerKB Analysis)
CVE-2020-1472 is an elevation of privilege vulnerability where a connection to a vulnerable domain controller using the Netlogon Remote Protocol could be used to obtain domain administrator access. The uniqueness behind this particular patch is that full remediation gets completed in two-phases. As a result, it forces the answer of “Am I remediated from CVE-2020-1472” from a binary “Yes/No” to a “It depends”.
By default, applying the applicable Windows Server patch will resolve the vulnerability for Windows devices without further action, but this implies that non-Windows devices could potentially trigger an exploit. It is by enforcing (something planned to become default in Q1 2021 according to Microsoft) the use of the secure Remote Procedure Call (RPC) with Netlogon secure channel via the DC enforcement mode that full remediation can be done. Microsoft acknowledges the potential organizational impact of this and has provided additional guidance on this front for those that may not be ready to enable DC Enforcement mode early.
Microsoft CVE-2020-1337: Windows Print Spooler Elevation of Privilege Vulnerability (AttackerKB Analysis)
CVE-2020-1337, while noted as “Exploitation Less Likely”, was originally disclosed during Blackhat back on August 6, 2020 and Proof-of-concept code is now available. This is an elevation of privilege vulnerability that targets the Windows Print Spooler service, allowing an attacker to run arbitrary code with elevated system privileges. Fortunately, standard operating system patching practices will remediate against this without atypical extra steps.
Proof-of-concepts and more detail now available which can be viewed from the AttackerKB analysis.
Microsoft CVE-2020-1380: Scripting Engine Memory Corruption Vulnerability (AttackerKB Analysis)
The first of the two vulnerabilities marked as exploited in the wild, CVE-2020-1380 reads like a “standard” Internet Explorer browser remote code execution attack. Through memory corruption, an attacked could execute arbitrary code in the context of the current user. While this is marked as a browser vulnerability, it’s worth noting that Microsoft Office documents hosting portions that use the IE rendering engine is another entryway.
As a gentle reminder, organizations following the Security-Only stream of patches should note that those patches do not include browser fixes unlike their Monthly Rollup counterparts.
Microsoft CVE-2020-1464: Windows Spoofing Vulnerability (AttackerKB Analysis)
CVE-2020-1464, the last of the two vulnerabilities noted as being exploited in the wild, is a Windows spoofing vulnerability. With this vulnerability, an attacker could bypass security features, exploiting a flaw validating file signatures, to load improperly signed files.
The patch for this vulnerability permeates the full set of supported Windows operating systems as well as the latest set of OS that have ESU support. This seems to imply that fully End-of-Life operating systems such as Windows Vista may potentially be vulnerable to this exploit without a patch available. Always take any and all opportunities to upgrade systems to supported versions.
Microsoft CVE-2020-1585: Microsoft Windows Codecs Library Remote Code Execution Vulnerability
Similar to CVE-2020-1425 and CVE-2020-1457 from 2020-Jun, this vulnerability sticks out as a continuation of a trend of noted Patch Tuesday vulnerabilities where remediation sits out of the traditional realm of “install patch here”, but adopts the app-store style of update where it will just happen. Luckily, the affected media codec AV1 Video Extension is an optional install via the Microsoft Store.
Microsoft CVE-2020-1571: Windows Setup Elevation of Privilege Vulnerability
Lastly, we arrive at CVE-2020-1571. This is an interesting vulnerability in that the attack surface is temporary. Only during an upgrade from a previous version of Windows 10 to a newer one is this elevation of privilege vulnerability exploitable.
There are no patches, as Microsoft has stated that all Feature Update bundles have been refreshed with the fix. However, this does mean any sort of WSUS/3rd party management tool would need to ensure they have the latest Setup DU Package.
Additional Statistics
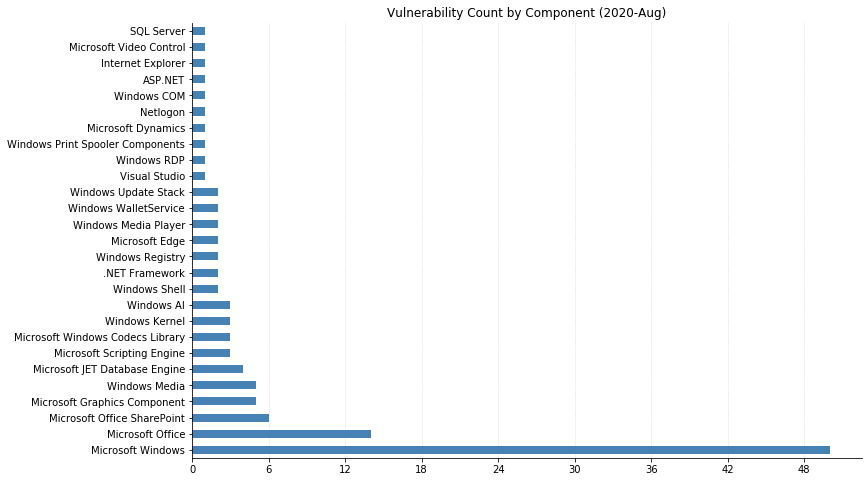
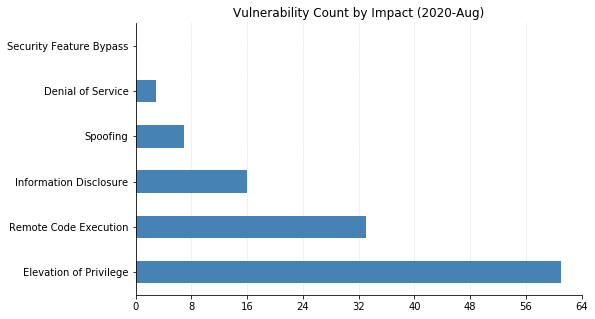
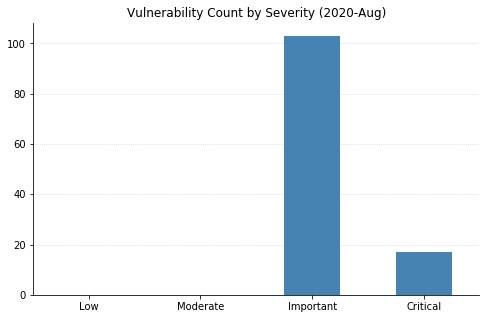
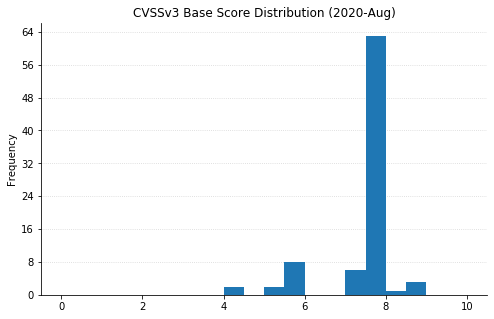
Note: Graph data is reflective of data presented by Microsoft’s CVRF at the time of writing.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



![[HANDALA] - Ransomware Victim: Hotam EC 8 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)