Patch Tuesday – February 2020

A relatively modest 99-vulnerability February Patch Tuesday has arrived with a fix for the Internet Explorer 0-day CVE-2020-0674 (originally ADV200001) announced back on January 17. Fortunately, that is the only vulnerability reported this month that has been seen actively exploited in the wild. Our usual set of suspected software takes center stage today (operating systems, Internet Explorer, and Office-related software), but with some supporting cast-members in Exchange Server, and SQL Server. We also see a second consecutive special guest appearance with Adobe Flash in the form of CVE-2020-3757, a remote code execution vulnerability. So with that in mind, let’s move forward with some notable entries this Patch Tuesday.
Let’s talk about CVE-2020-0674. This vulnerability took advantage of memory corruption to allow arbitrary code to run in the context of the current user. With a lapse of good security hygiene, a user could be convinced to view an affected website allowing an attacker to install programs, alter data, or create new accounts with full user rights. The original workaround for this remote code execution vulnerability in the Internet Explorer scripting engine entailed restricting access to jscript.dll (not to be confused with jscript9.dll). But in order to fully remediate via patching, this workaround would need to be undone prior. Don’t forget this step if you’ve applied the workaround on your systems!
Now, with this being the first month that Windows 7, Windows Server 2008 R2, and Windows Server 2008 will not actively receive patches outside of an Extended Security Update license, it would’ve been safe to say that the patching scenario would be relatively streamlined. Previously, Windows Server 2008 still operated under the old patching paradigm where each vulnerability is addressed by a separate patch, but now all operating system patches fall within three categories: Monthly Rollup, Security-Only, or the Cumulative Update (for Windows 10-based systems). The biggest exception this month comes on the heels of CVE-2020-0689 which is a security feature bypass vulnerability in secure boot, allowing an attacker to bypass secure boot and load untrusted software. The patch, which will block vulnerable third-party bootloaders, sits outside the typically offered OS patches and in addition, have firm Servicing Stack Update prerequisites. It is this change that makes this vulnerability something to note.
Windows Remote Desktop vulnerabilities have been getting some attention lately, and this Patch Tuesday is no different. This time around, CVE-2020-0734 depicts a scenario where an attacker would need to trick the user into connecting to a malicious server. In doing so, the attacker could then install new applications and/or act with full user rights. Even with the usual advice of having appropriate “clicking hygiene”, a compromised legitimate server hosting the malicious code can achieve the same goal. Close off this vulnerability in how the client handles connection requests by promptly installing those operating system patches.
The remaining publicly disclosed vulnerabilities, a set of elevation of privilege vulnerabilities within Windows Installer (CVE-2020-0683 and CVE-2020-0686) which allow the ability to add/remove files and CVE-2020-0706 which is an information disclosure vulnerability in IE have received a severity rating of Important with less likelihood for being exploited.
Speaking of Internet Explorer, Microsoft Edge based on Chromium is here to stay and just a few days prior, was updated fixing the latest set of security issues from the Chromium project which amounts to 37 vulnerabilities in total. Very edgy.
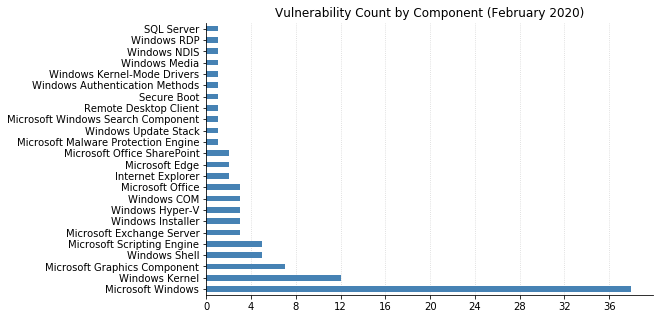
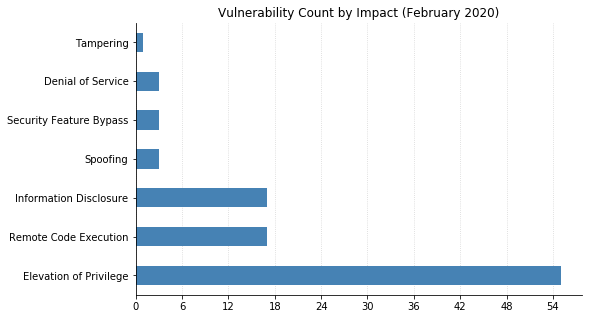
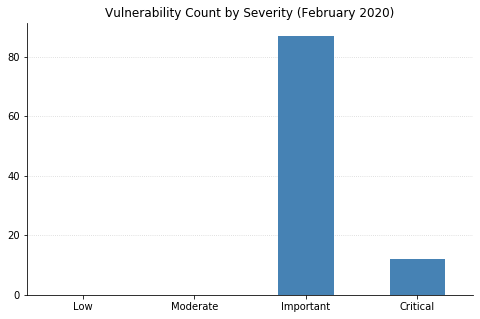
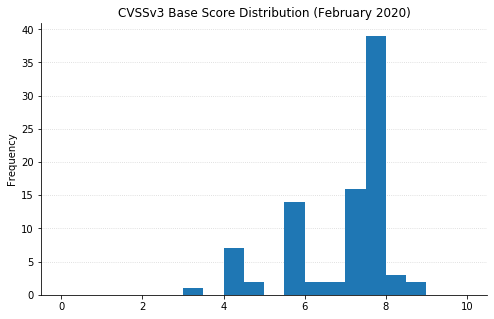
Note: Graph data is reflective of data presented by Microsoft’s CVRF at the time of writing



