Patch Tuesday – January 2020

The first Patch Tuesday of 2020 has been hotly anticipated due to a rumour that Microsoft would be fixing a severe vulnerability in a fundamental cryptographic library. It turns out that the issue in question is indeed serious, and was reported to Microsoft by the NSA: CVE-2020-0601 is a flaw in the way Windows validates Elliptic Curve Cryptography (ECC) certificates. It allows attackers to spoof a code-signing certificate that could be used to sign a malicious executable, which would look totally legitimate to the end user. It also enables attackers to conduct man-in-the-middle attacks and decrypt confidential information on user connections to affected systems. This vulnerability exists in Windows 10, Server 2016, and Server 2019. These systems need to be patched immediately, as correct certificate validation is vital for determining trust.
According to Microsoft, on patched systems it is possible to detect attempts to use such forged certificates by looking at the Event Viewer under Windows Logs/Application for events with Event ID 1 that indicate “an attempt to exploit a known vulnerability ([CVE-2020-0601] cert validation)”.
Of course, the fun this month doesn’t stop there: Microsoft also published 48 other CVEs. Continuing a well-established theme from last year, three new Critical Remote Code Execution (RCE) vulnerabilities related to the Remote Desktop Protocol (RDP) have been addressed. Two of these, CVE-2020-0609 and CVE-2020-0610, are pre-authentication and affect Remote Desktop Gateway running on all supported versions of Windows Server. Remote Desktop Gateway is used to allow clients to connect to RDP servers behind it, typically on a private corporate network. If RD Gateway is present in your environment, patching these servers should be a high priority. The third RCE, CVE-2020-0611, affects RDP clients on all currently supported versions of Windows. Similar to the four RDP vulnerabilities published last September, an attacker would need to convince a user to connect to a malicious RDP server via social engineering or other means, at which point they could then execute arbitrary code on the computer of the connecting client.
Other notable issues this month are the twelve separate privilege escalation vulnerabilities fixed in Windows Search Indexer, a privilege escalation in Windows Subsystem for Linux (CVE-2020-0636), three RCEs in Microsoft Excel (CVE-2020-0650, CVE-2020-0651, and CVE-2020-0653), and a Critical RCE in Internet Explorer (CVE-2020-0640). There are also three Critical RCEs in .NET Framework (CVE-2020-0605, CVE-2020-0606, CVE-2020-0646), which hasn’t seen a security patch in several months.
Also, an important reminder: this is the last month that Windows 7, Server 2008, and Server 2008 R2 will receive security updates. These operating systems are all considered end of life now, and should be upgraded to a supported version as soon as possible. It’s certain that many future vulnerabilities announced by Microsoft will affect these systems, but will not be explicitly called out. Obsolete OS software is like candy to attackers, especially when support has just recently been dropped and the legacy systems are still prevalent.
Rapid7’s Project Sonar indicates that over 72000 such systems are accessible on the public Internet as of January 12, 2020. Judging by how many Server 2003 instances are still being seen, we can expect many of these to still be connected for years to come.
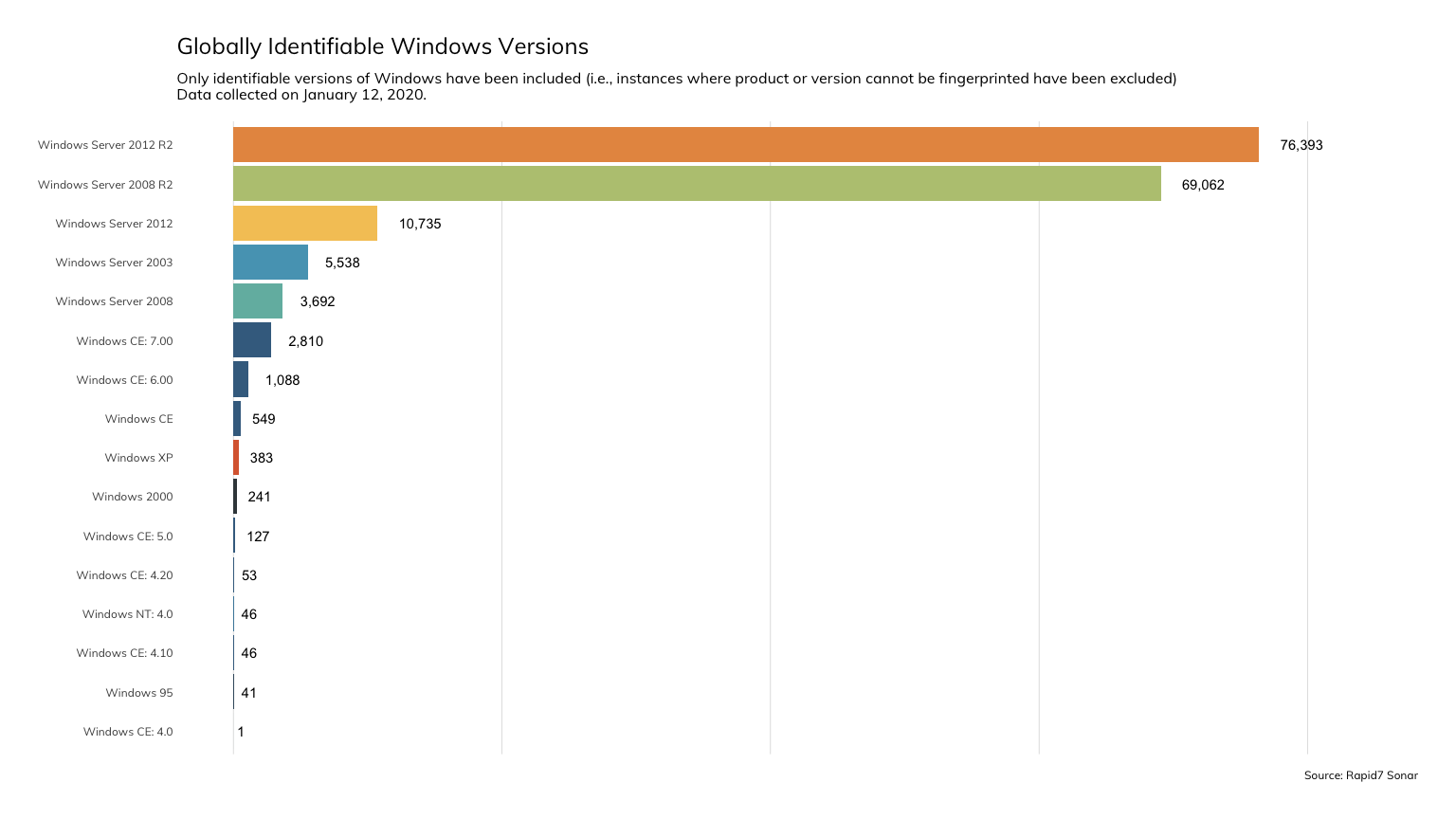
(A minor caveat with the above chart: it’s probable that a small percentage of the systems in each category are actually honeypots, intentionally advertising an older version to attract attackers.)
Finally: it’s worth pointing out that today is also Oracle’s quarterly CPU, where they’ve published over 300 different CVEs across their rather extensive product line, including Database, Java, MySQL, WebLogic, and many others.
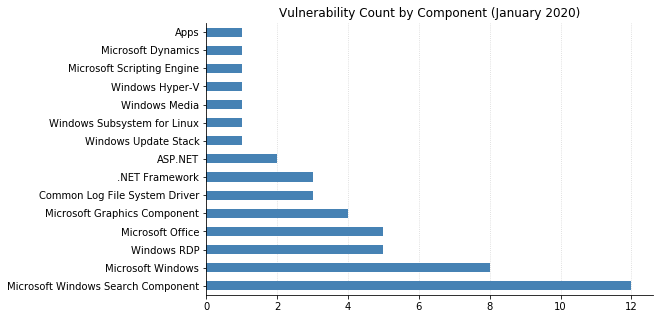
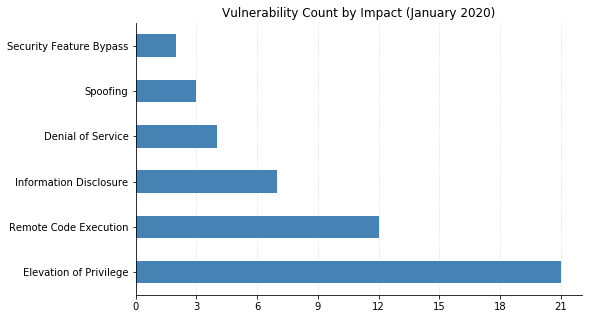
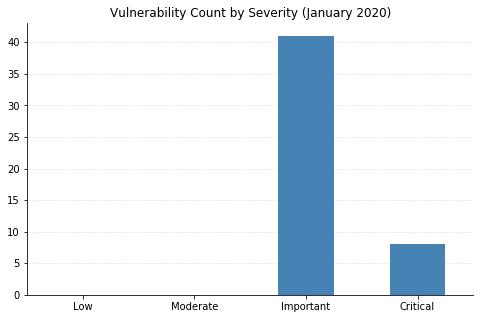
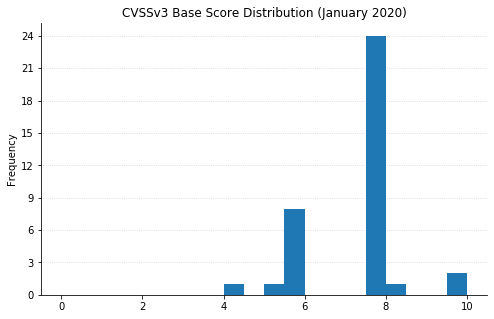
Note: not all CVEs had CVSSv3 data available at the time of writing

![[INCRANSOM] - Ransomware Victim: C B King Memorial School(branch) 7 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)



