Patch Tuesday – July 2020
100+ vulnerabilities patched during Patch Tuesdays the new norm

Another 123 CVEs are covered this month from Microsoft for the 2020-Jul Patch Tuesday. In addition to our usual suspects like Windows, Internet Explorer/Microsoft Edge, and Microsoft Office this Patch Tuesday addresses several developer-type tools such as .NET Framework, Visual Studio Code ESLint extension along with various Open Source Software like TypeScript, Bond 9.0.1, and Azure Storage Explorer. The latter bunch don’t go through typical patching patterns but at the same time, likely have a smaller footprint than the typical Windows OS vulnerabilities.
Microsoft CVE-2020-1350: Windows DNS Server Remote Code Execution (AttackerKB Analysis)
The star of this Patch Tuesday is CVE-2020-1350, a wormable vulnerability on Windows Servers running the Windows DNS Server service. This vulnerability includes ESU servers like Windows Server 2008 and Windows Server 2008 R2, but extends throughout all supported versions of Windows Server that can run the Windows DNS Server service.
With caveats, Microsoft provided a Windows Registry setting workaround that effectively drops TCP-based DNS response packets exceeding 65280 bytes without reporting an error. It’s recommended that if patching cycles are slow, that the workaround be applied ahead of the cycle. The workaround does not need to be removed prior to patching, although it would be worthwhile to undo the workaround after patching.
For a deeper dive on this vulnerability, head on over to our blog post: Windows DNS Server Remote Code Execution Vulnerability (CVE-2020-1350): What You Need to Know
Microsoft CVE-2020-1374: Remote Desktop Client Remote Code Execution Vulnerability
Another vulnerability to note is CVE-2020-1374. A vulnerable version of the Remote Desktop Client on OS version from Windows 7 (and possibly earlier!) to the latest version of Windows 10 (2004) could be used to execute arbitrary code with full user rights when connected to a malicious server. This vulnerability, however, is a client-side vulnerability unlike the recent higher-profile vulnerabilities like BlueKeep and DejaBlue. A pinch of social engineering or other means such as using a Man-in-the-Middle attack would be needed to take advantage of this vulnerability.
Hyper-V RemoteFX vGPU Vulnerabilities
On the stranger side of things, several vulnerabilities surrounding the deprecated RemoteFX vGPU for Hyper-V hosts got “patched up” this month. For CVE-2020-1032, CVE-2020-1036, CVE-2020-1040, CVE-2020-1041, CVE-2020-1042, and CVE-2020-1043 the worst would allow an attacker to execute arbitrary code on the host system. Given that RemoteFX vGPU is no longer under active development, Microsoft has provided additional details on assisting in migrating off that feature for environments that continue to depend on RemoteFX vGPU.
Microsoft CVE-2020-1346: Windows Modules Installer Elevation of Privilege Vulnerability
The last operational aspect to this Patch Tuesday that deviates from the norm is CVE-2020-1346, an elevation of privilege vulnerability in the Windows Modules Installer component for all Windows OS (ESU-eligible and up). In this particular case, the Servicing Stack Updates released this month should been installed prior to installing the cumulative update/monthly rollup or security update patch. While it was not explicitly outlined, following these directions from Microsoft for CVE-2020-1346 may have a direct impact on the order of operations when resolving other issues such as CVE-2020-1350.
Additional Statistics
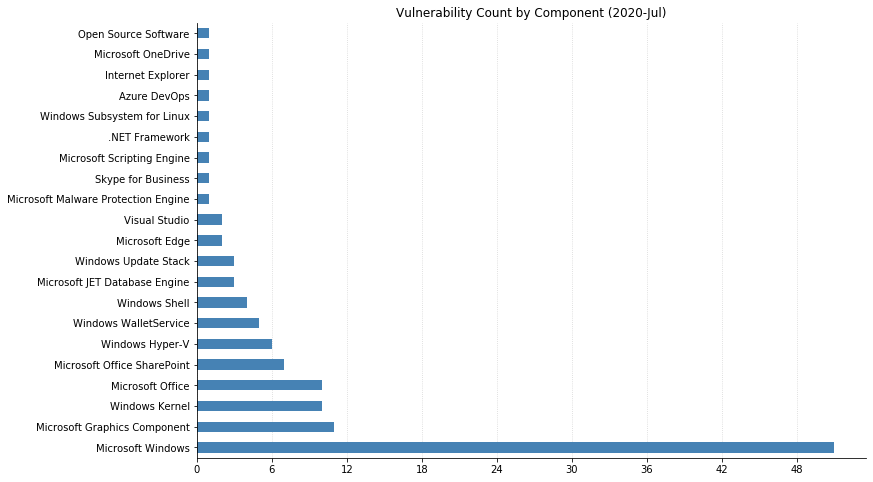
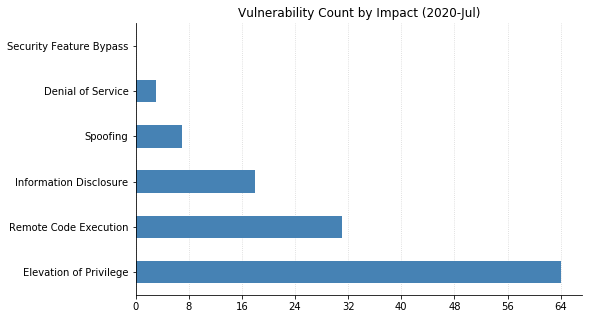
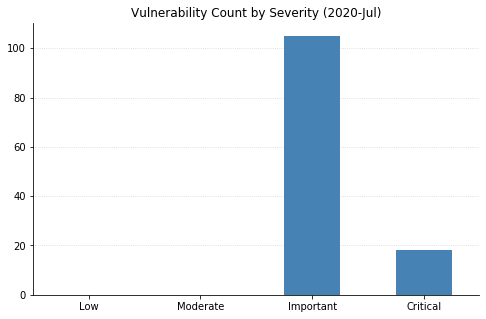
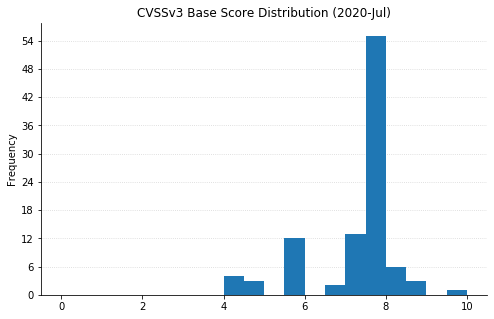
Note: Graph data is reflective of data presented by Microsoft’s CVRF at the time of writing.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[INCRANSOM] - Ransomware Victim: CF Construction Ltd 7 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

