Police takes down BulletProftLink large-scale phishing provider

The notorious BulletProftLink phishing-as-a-service (PhaaS) platform that provided more than 300 phishing templates has been seized, the Royal Malaysian Police announced.
The operation started in 2015 but came to researchers’ radar later and became more active since 2018 and had thousands of subscribers, some of them paying for access to batches of credential logs.
PhaaS platforms provide cybercriminals with tools and resources to carry out phishing attacks through “ready-to-use” kits and templates, page hosting, customization options, credential harvesting, and reverse proxying tools.
The BulletProftLink operation has been documented before. In 2020, a cybersecurity expert Gabor Szathmari detailed in a three-part series of open-source intelligence research [1, 2, 3] how he linked with high confidence the operator of the service to a Malaysian national living a life of luxury.
A Microsoft report in September 2021 warned about the high volume of phishing attacks it could facilitate and the large number of templates available to buyers. The service also collected all credentials its subscribers (1,618 at the time) stole in phishing attacks.
BulletProftLink busted
Aided by the Australian Federal Police and the FBI the Malaysian police managed to dismantle the operation and take down multiple domains it used by the illegal shop.
The police arrested eight individuals on November 6, one of them a self-taught man believed to be the leader of the operation. Authorities also seized cryptocurrency wallets holding about $213,000, servers, computers, jewelry, vehicles, and payment cards.
With servers confiscated, law enforcement can examine them to identify users of the platform, some of them paying a $2,000/month subscription fee to access regular batches of credentials logs.
Cybercrime intelligence company Intel471says that as of April 2023, BulletProftLink had 8,138 active subscribers with access to 327 phishing page templates.
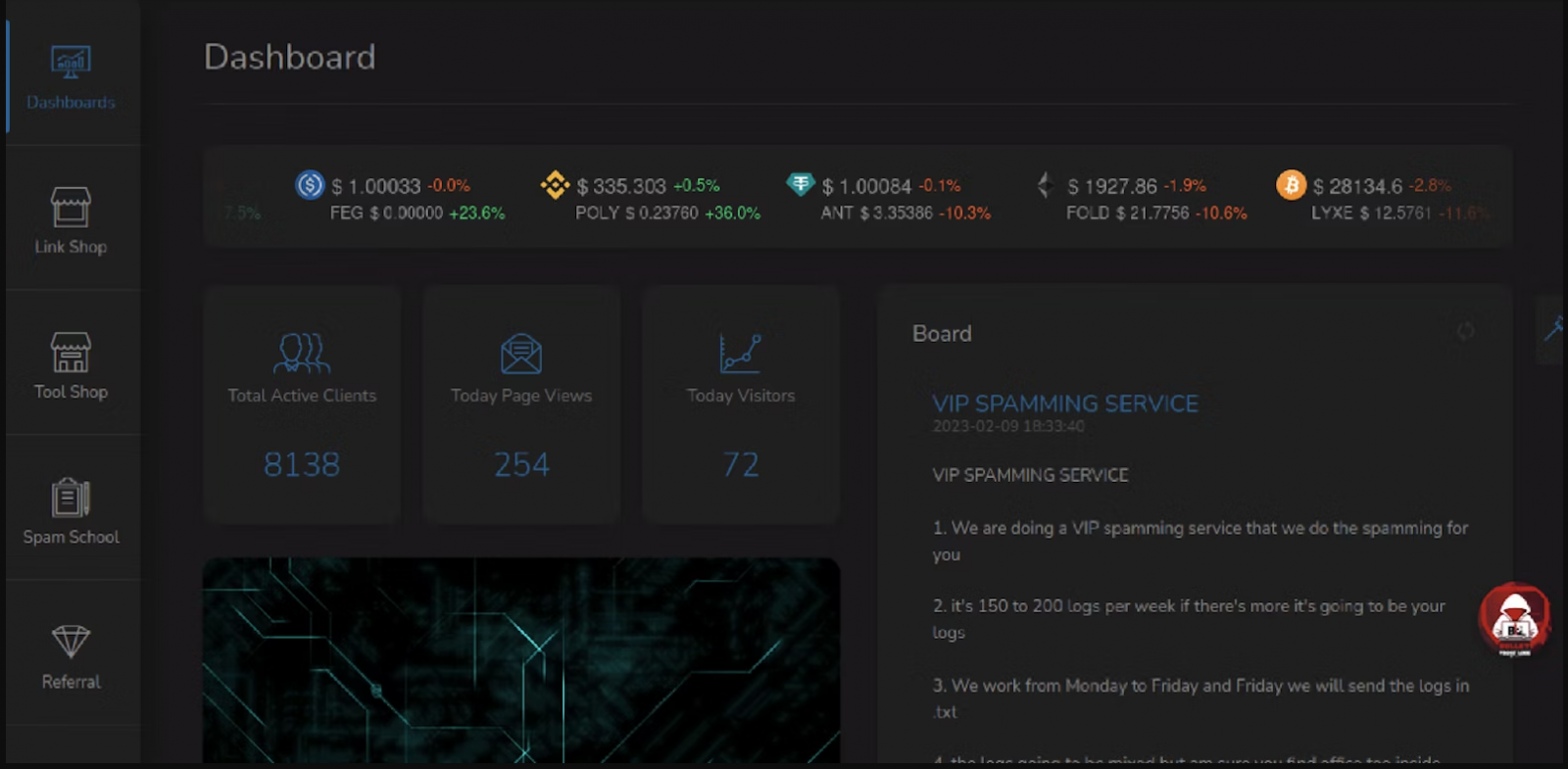
This is a 403% rise in customers since Microsoft’s report in 2021, reflecting the platform’s massive popularity in the cybercrime community.
Intel 471 says that phishing resources BulletProftLink offered before it was taken down “included login pages for Microsoft Office, DHL, the South Korea-based online platform Naver and financial institutions including American Express, Bank of America, Consumer Credit Union and Royal Bank of Canada.”
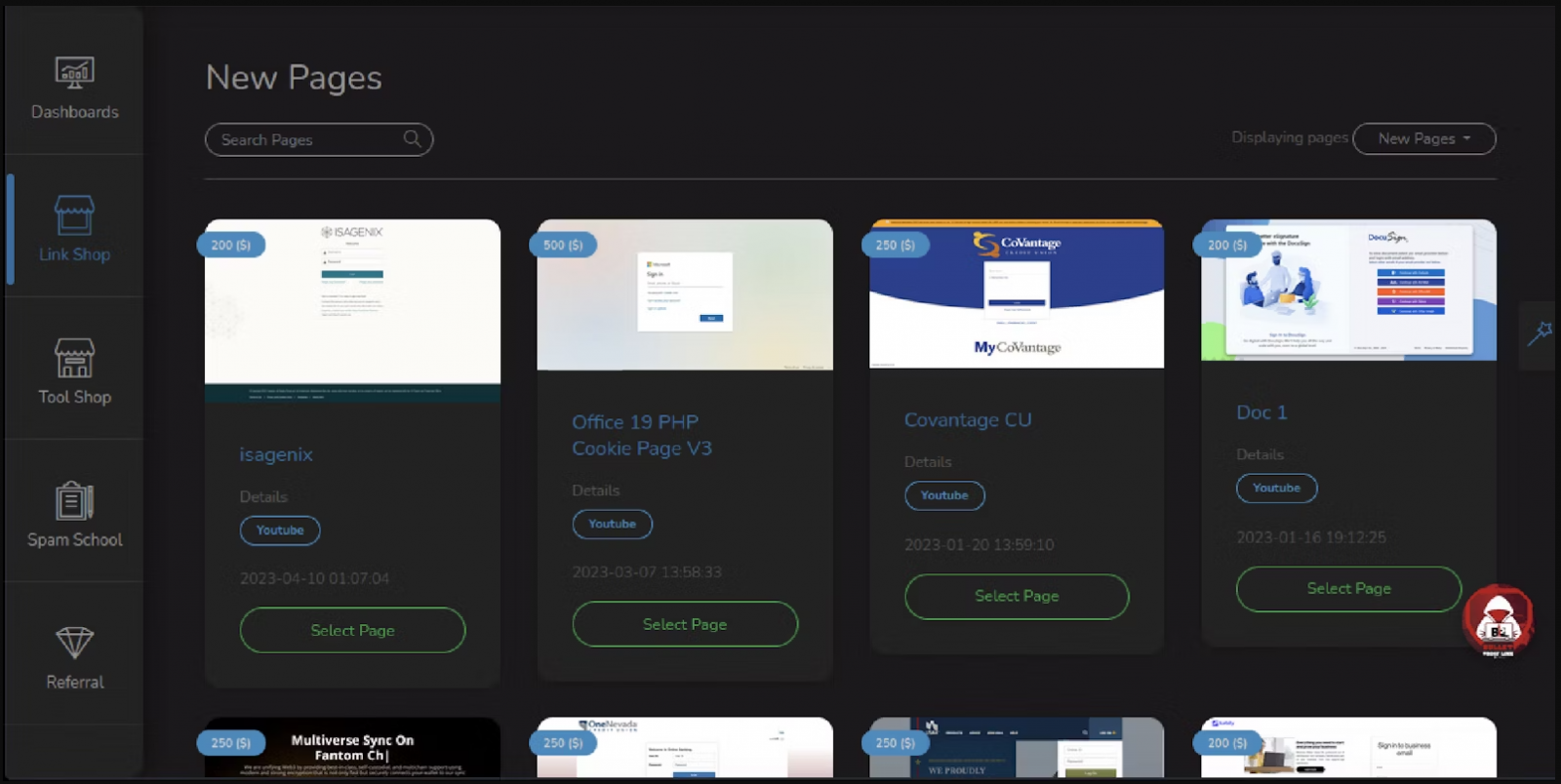
Some of these phishing pages were hosted on legitimate cloud services like Google Cloud and Microsoft Azure to evade email security tools.
BulletProftLink’s inventory also also offered the Evilginx2 reverse-proxying tool that enables adversary-in-the-middle (AITM) phishing attacks, which can bypass multi-factor authentication protections.
The operation was an important source of credentials for professional cybercriminals to gain initial access to corporate systems. With a foothold in the company network, attackers can start the reconnaissance stage and moving laterally to valuable hosts.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[GLOBAL] - Ransomware Victim: loraincountyauditor[.]gov 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

