PSA: Ongoing Webex malvertising campaign drops BatLoader
A new malvertising campaign is targeting corporate users who are downloading the popular web conferencing software Webex. Threat actors have bought an advert that impersonates Cisco’s brand and is displayed first when performing a Google search.
We are releasing this blog to warn users about this threat as the malicious ad has been online for almost one week. The malware being used in this campaign is BatLoader, a type of loader that is very good at evading detection.
Note that Webex has not been compromised, this is a malicious campaign where threat actors are impersonating well-known brands to distribute malware.
Ad campaign details
For the past several days, we saw the same malicious ad whenever we searched for Webex. The advert is shown to users before the organic result and yet looks even more genuine as it is displaying the brand’s logo:
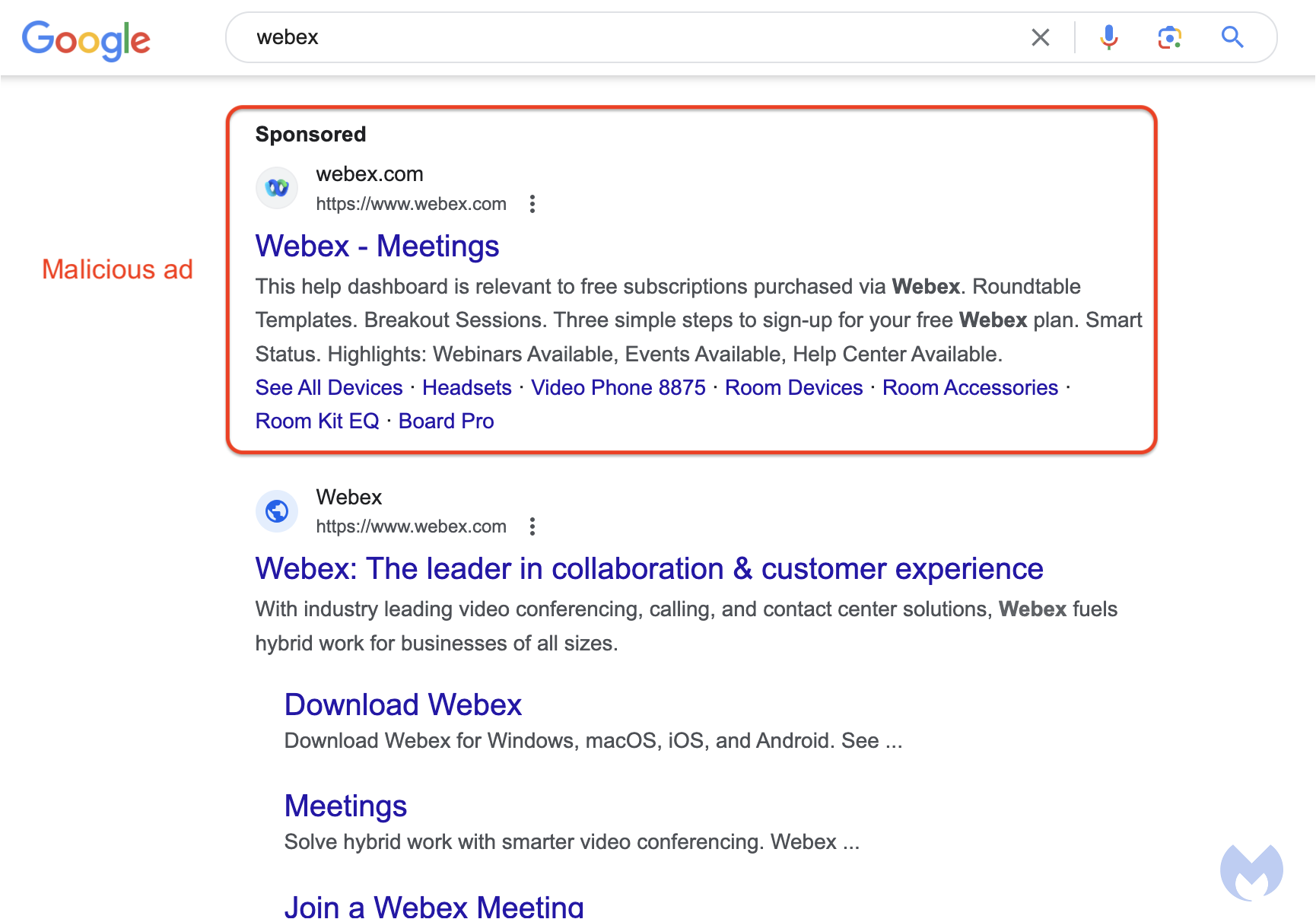
In fact, the ad looks entirely legitimate as it not only uses the Webex logo but also shows the official website. Yet, clicking on the menu to the right of the ad shows more details and reveals the advertiser as an individual from Mexico, quite unlikely to be related to Cisco:
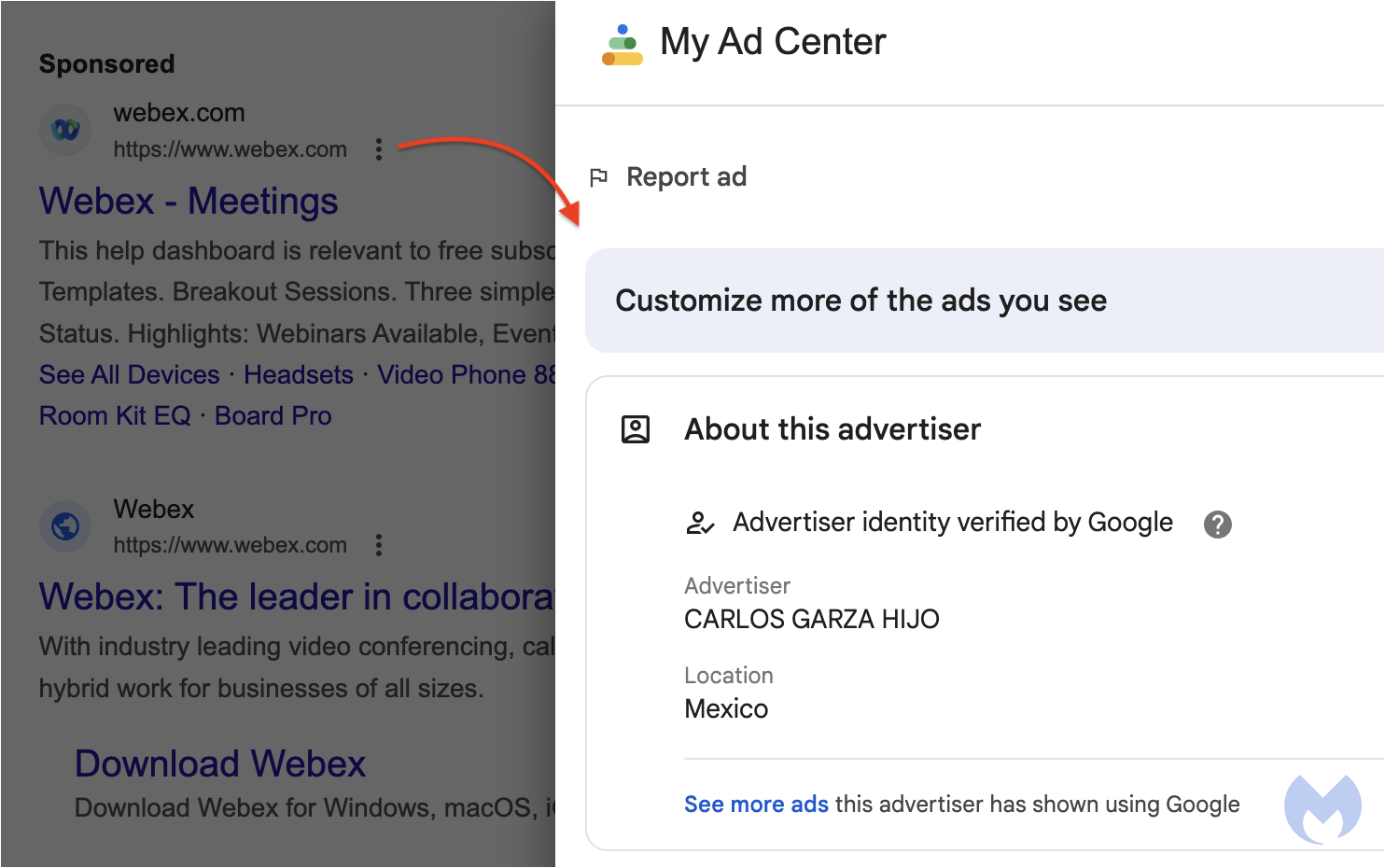
To understand how this is happening, we can look at the Google Ads policy for display URLs. In particular, Google states that:
Your ads’ URLs should give customers a clear idea of what page they’ll arrive at when they click an ad. For this reason, Google’s policy is that both display and landing page URLs should be within the same website. This means that the display URL in your ad needs to match the domain that visitors land on when they click on your ad.
This malicious ad actually complies with this rule in the strict sense of the term as its landing page URL, also known as final URL, is on the same domain.
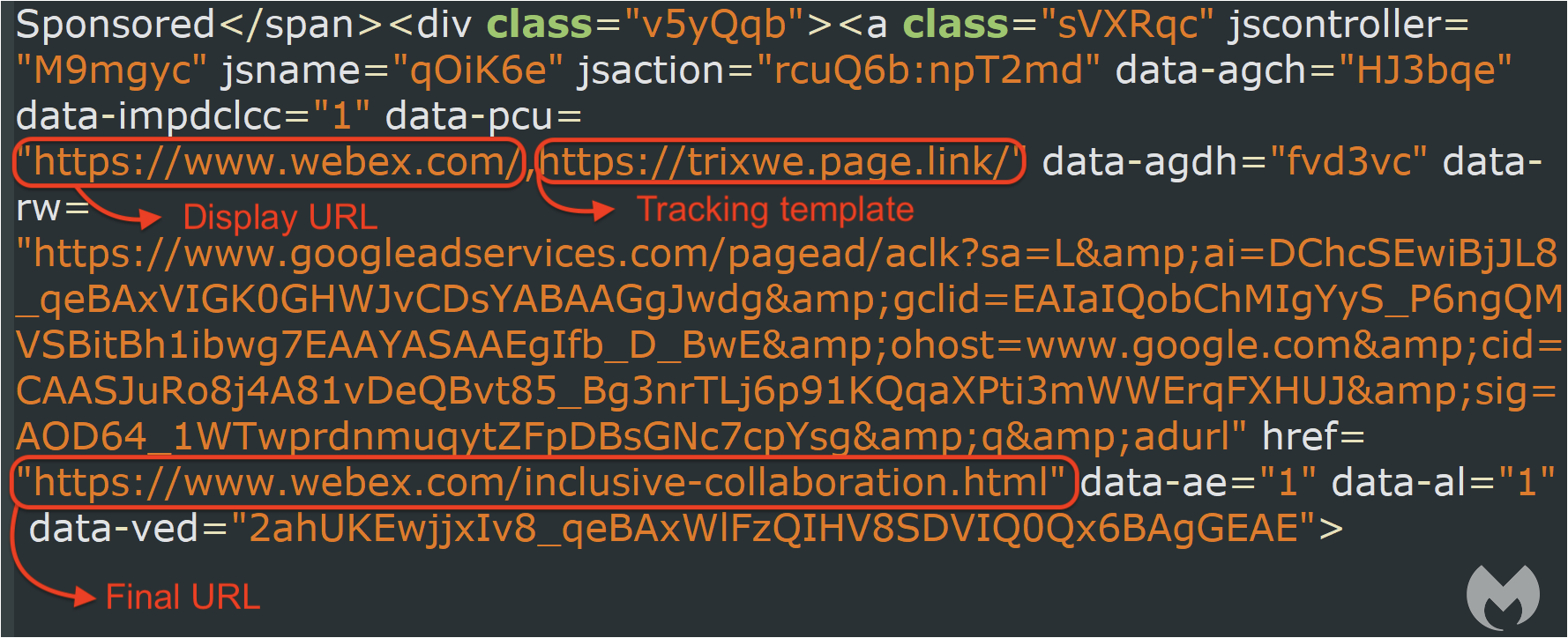
The threat actor is exploiting a loophole known as the tracking template. Google describes the tracking template as a place where you put URL tracking information. This is particularly helpful for advertisers as it gives them a number of metrics. However, it can also be abused in a way where the tracking template URL is used as a filtering and redirection mechanism.
For example, the threat actor has created a Firebase URL (trixwe.page.link) as their tracking template
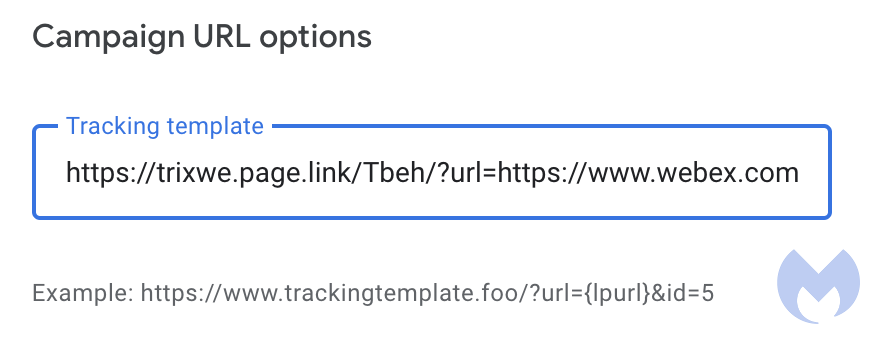 The tracking URL can perform a number of checks on the visitor and determine if they are a potential victim. Here’s what happens if the ad was clicked via a sandbox:
The tracking URL can perform a number of checks on the visitor and determine if they are a potential victim. Here’s what happens if the ad was clicked via a sandbox:
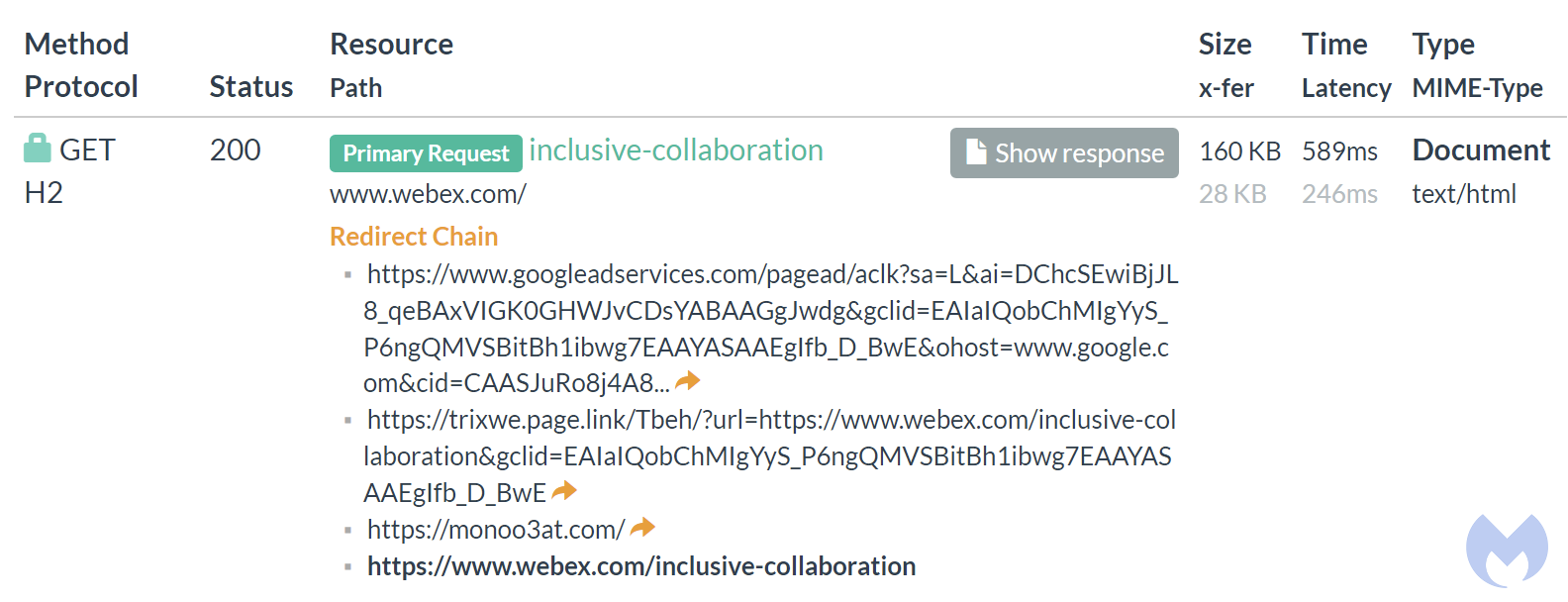
We can see the tracking page redirects to a custom attacker-controlled website at monoo3at[.]com. This step allows the threat actor to fingerprint the visitor and then determine which action to take. In this case, the visitor was detected as a sandbox and therefore is being redirected to Webex’s official website. This technique is important because it allows the malicious advertiser to keep their ad up and running for a long time.
However, when the ad is clicked by a real victim, the web traffic looks very different:
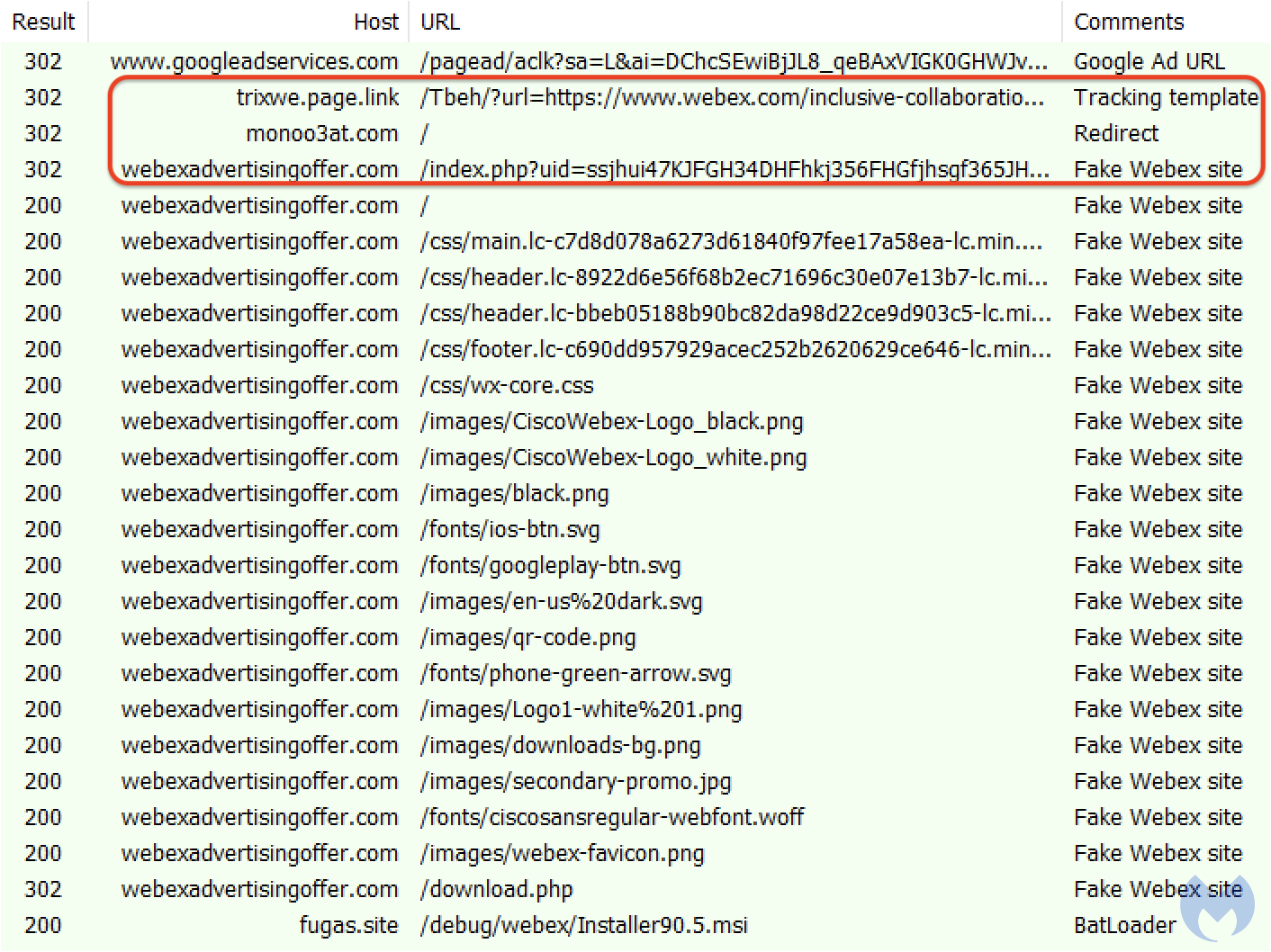
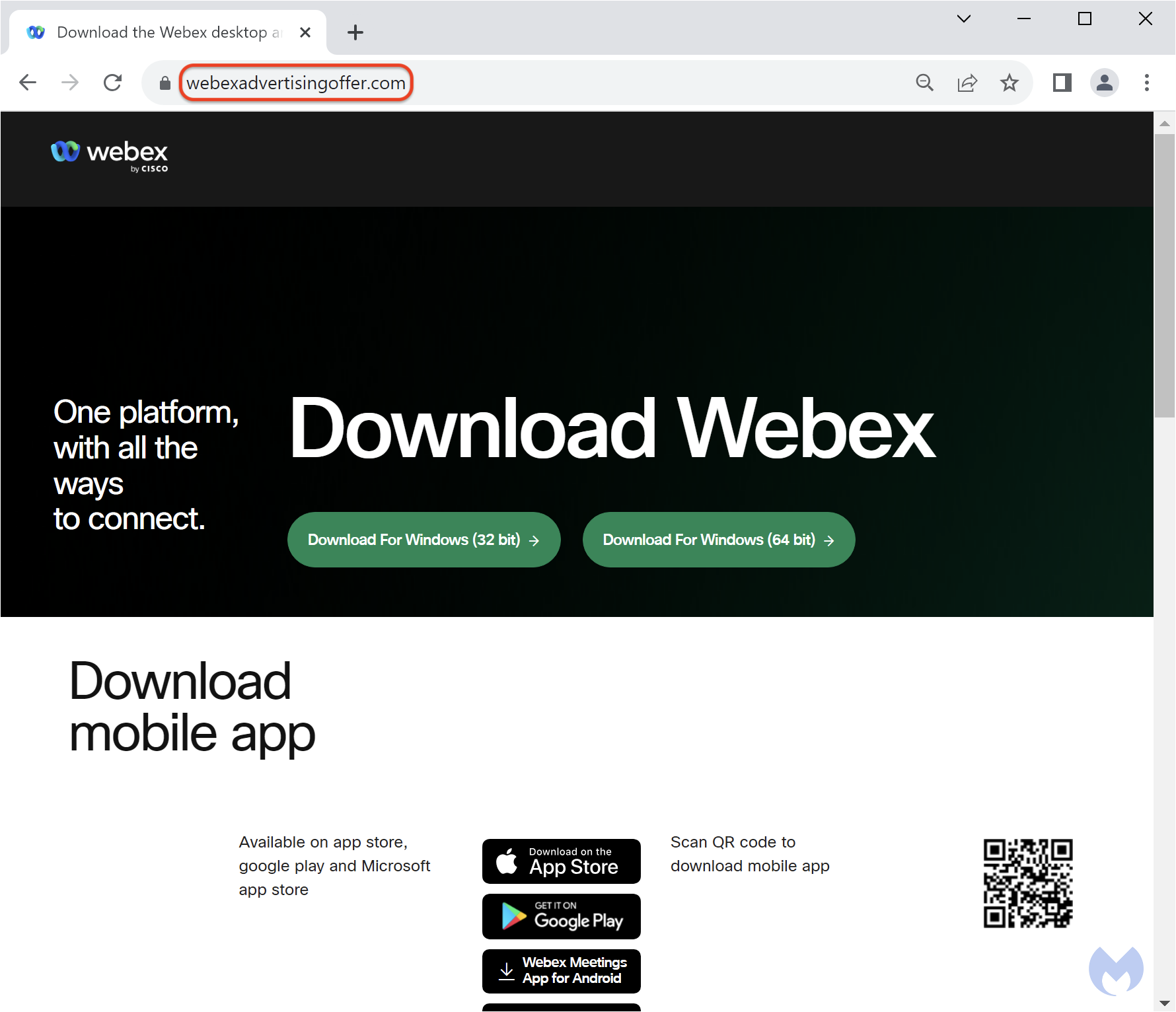
Instead, the user is redirected to a malicious website (webexadvertisingoffer[.]com) purporting to be Webex:
BatLoader: the stealthy malware loader
The downloaded file exceeds the size limit for many sandboxes and is designed to bypass detection from antivirus products. While VirusTotal is not meant to be a replacement for a security product, it typically provides useful information and is often used by people to check if a file is clean.
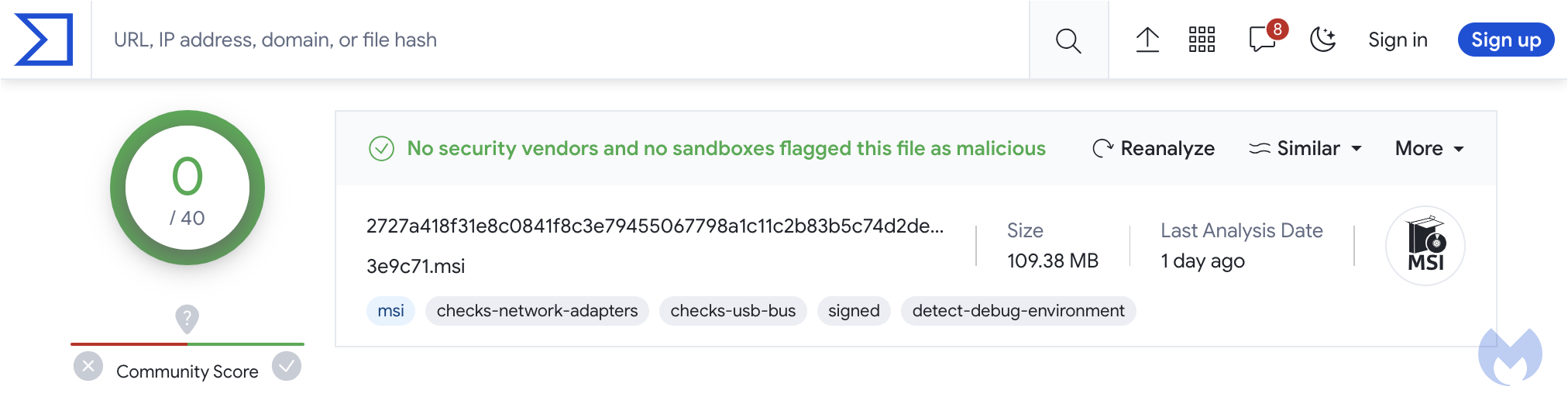
In this case, there were 0 detection for this MSI file, in part because the format was unsupported by several security products:
But there is more to it and the way the file is packaged is making detection much more difficult. If we extract the installer’s contents we see many different folders and hundreds of files and libraries:
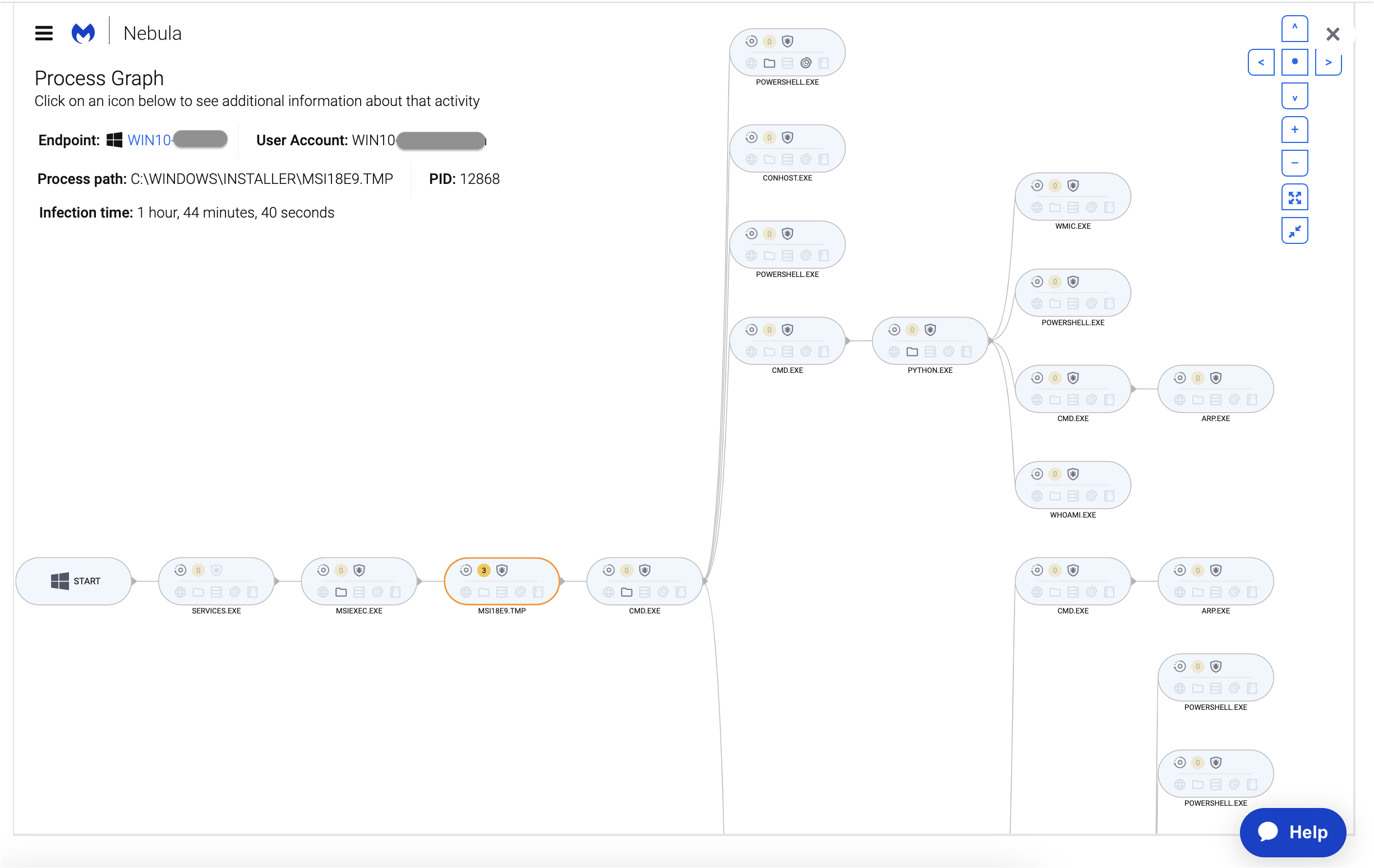
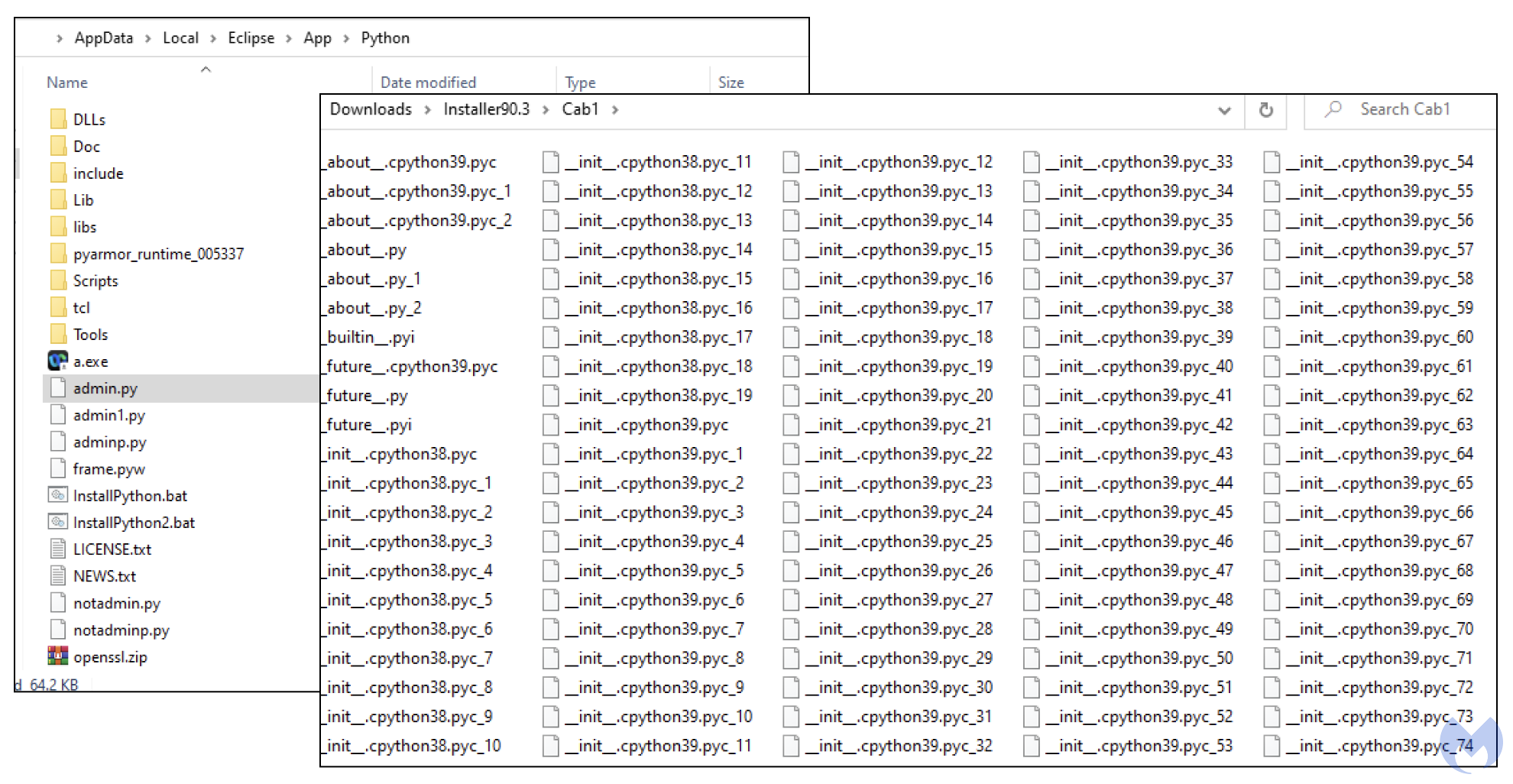 This is where a different type of security product, such as an EDR can actually show what is going on. The MSI installer contains anti-sandbox features and will only execute in certain environments. Using Malwarebytes’ Nebula, our cloud-hosted security platform for businesses, we can see the MSI spawns a number of processes including PowerShell and installs Python from a local resource.
This is where a different type of security product, such as an EDR can actually show what is going on. The MSI installer contains anti-sandbox features and will only execute in certain environments. Using Malwarebytes’ Nebula, our cloud-hosted security platform for businesses, we can see the MSI spawns a number of processes including PowerShell and installs Python from a local resource.
This is BatLoader and based on the environment it detects, it will retrieve a custom secondary payload.
That payload is downloaded from BatLoader’s command and control server in encrypted format:
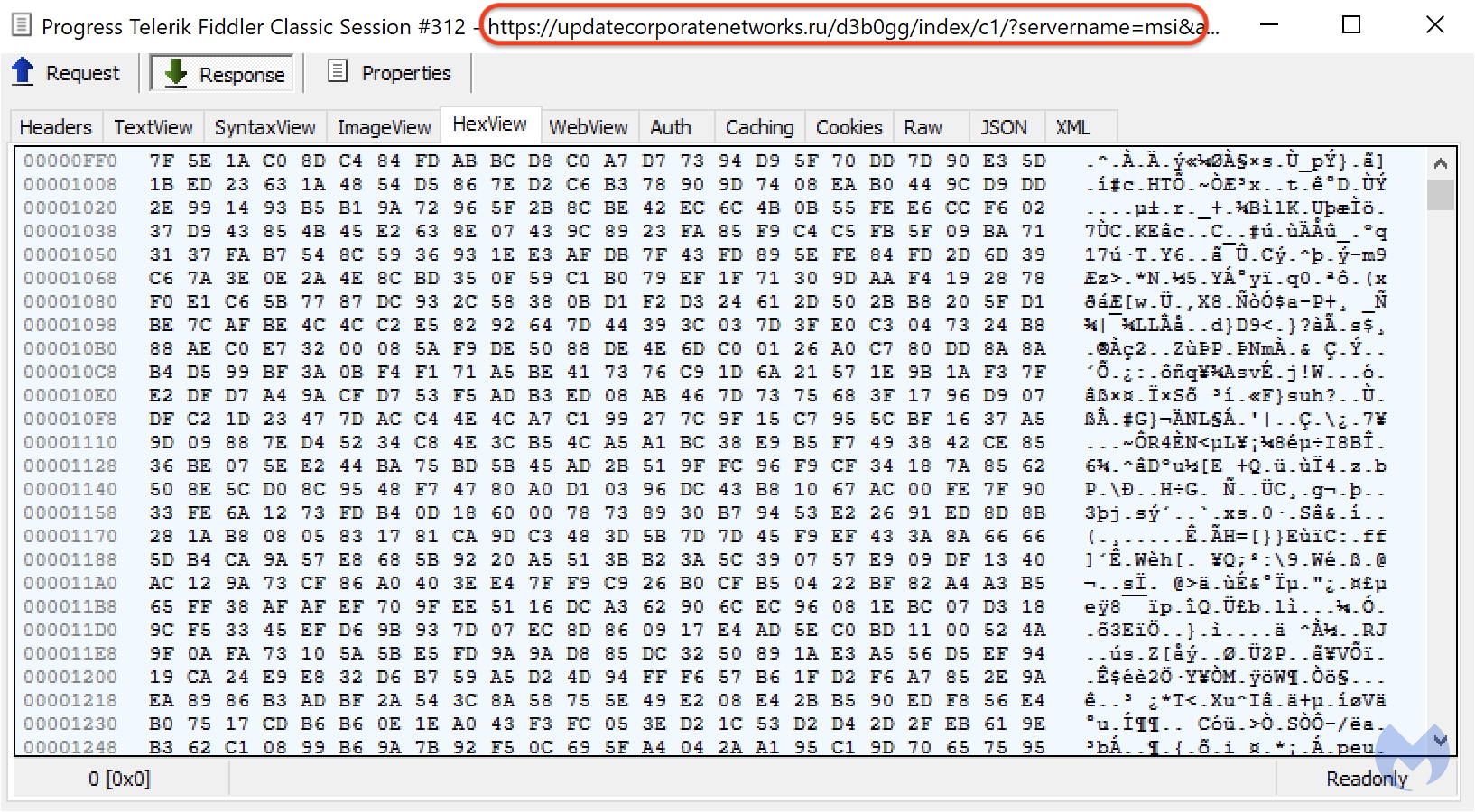
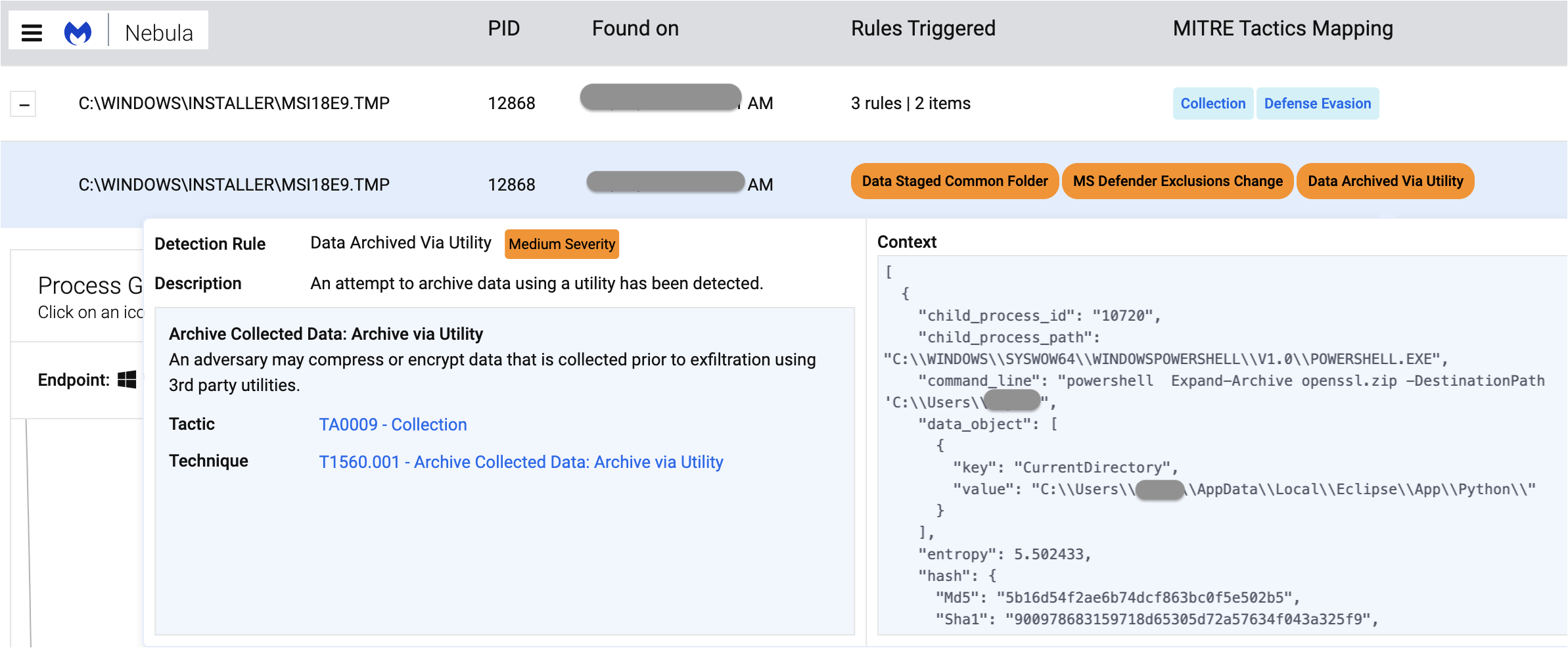
It is then then decrypted on disk using openssl, which we can see within our EDR environment:
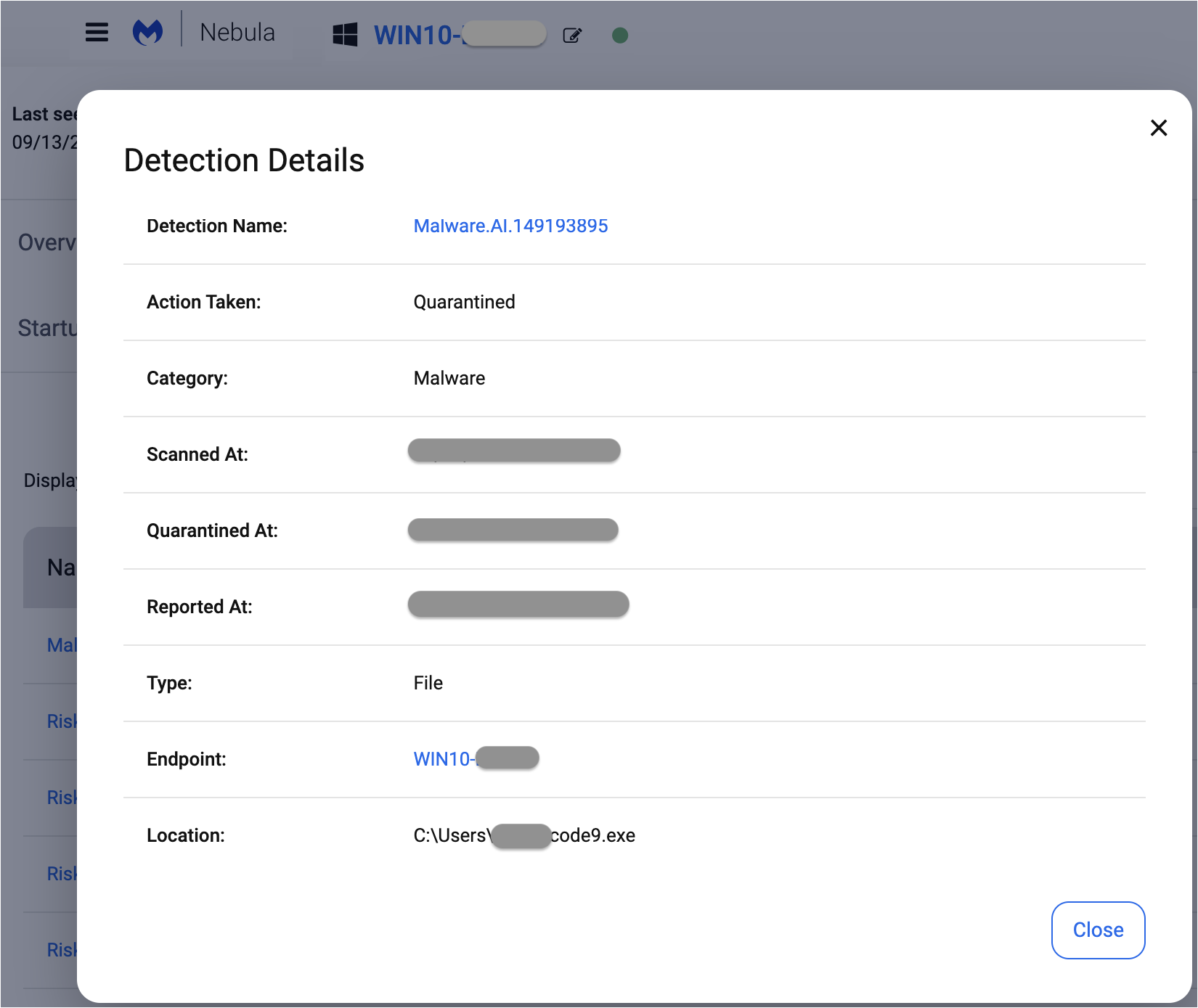
That dropped malware is DanaBot, which was already detected without signature via our EDR’s heuristic engine:
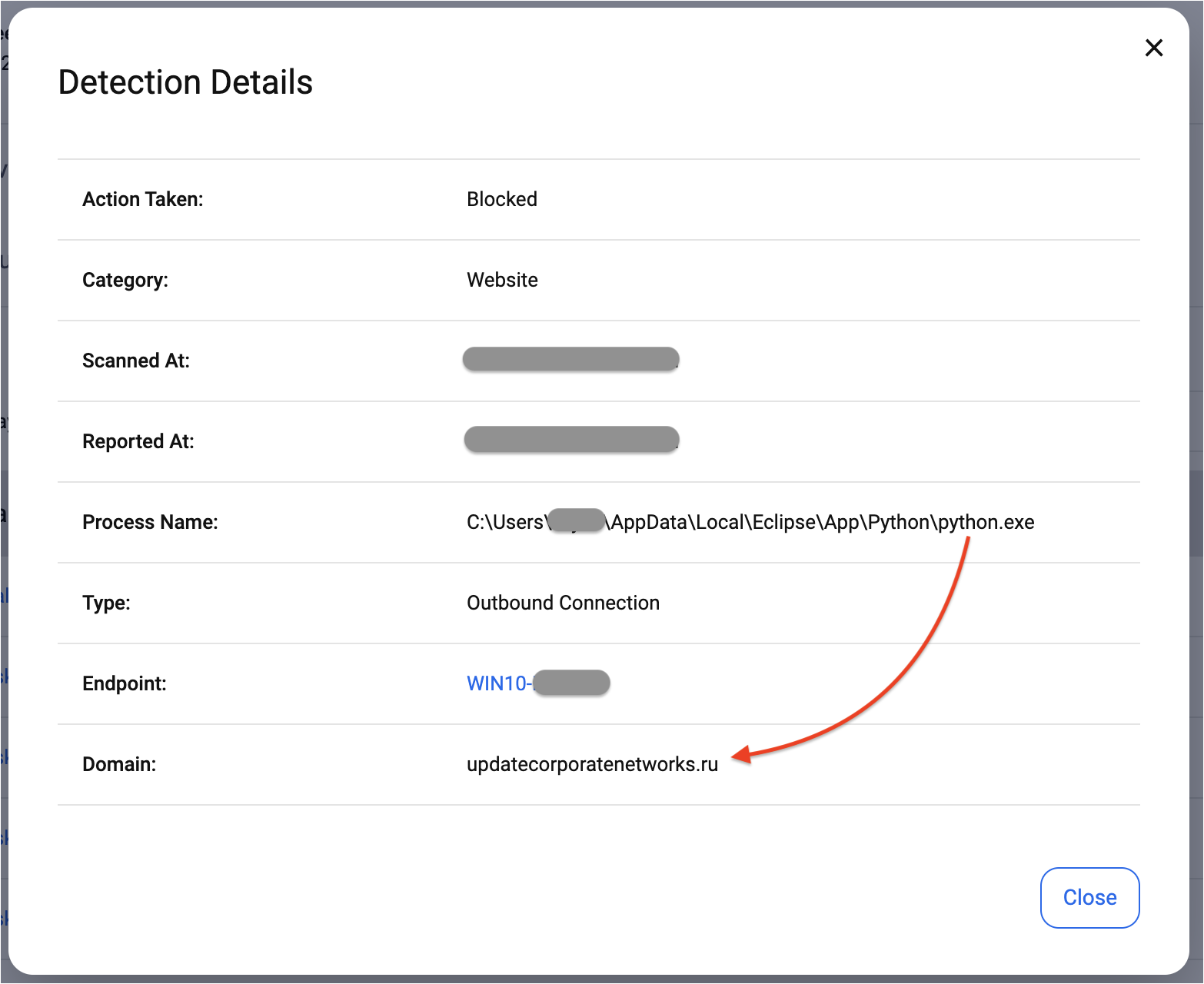
We have added detection for BatLoader’s C2:
Malvertising continues to provide initial access to threat actors
As we saw in this blog post, malvertising is a threat that continues to target corporate users, in particular by taking advantage of search engines such as Google that are commonly used to search for and download software.
Because the ads look so legitimate, there is little doubt people will click on them and visit unsafe sites. The type of software being used in those ads indicate that threat actors are interested in corporate victims that will provide them with credentials useful for further network “pentesting” and, in some cases, ransomware deployment.
Loaders such as BatLoader are stealthy and may not be detected by traditional antivirus. A more complete solution such as EDR coupled with an MDR service where human analysts review suspicious activities performed by the malware is a necessity.
We reported the malvertising incident to Google several days ago and will keep monitoring the ad landscape for any changes from these threat actors.
Indicators of Compromise
Cloaking infrastructure
monoo3at[.]com
206.71.149[.]46
Decoy site
webexadvertisingoffer[.]com
31.31.196[.]208
BatLoader
fugas[.]site/debug/Installer90.2.msi
2727a418f31e8c0841f8c3e79455067798a1c11c2b83b5c74d2de4fb3476b654
BatLoader C2
updatecorporatenetworks[.]ru
91.199.147[.]226
DanaBot
7a1245584c0a12186aa7228c75a319ca7f57e7b0db55c1bd9b8d7f9b397bfac8
Malwarebytes EDR and MDR removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[INCRANSOM] - Ransomware Victim: C B King Memorial School(branch) 15 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)



