PYSA, the ransomware attacking schools
The education sector’s cybersecurity problem has compounded in the last few months. A recent warning from the FBI, in mid-March, put schools in the US and UK on notice of increased attacks from the threat actors behind the PYSA ransomware.
If this is the first time you’ve heard of this family, read on.
What is PYSA ransomware?

The PYSA ransomware is a variant of the Mespinoza ransomware.
PYSA, which stands for “Protect Your System Amigo”, was first named in open source documents in December 2019, two months after Mespinoza was spotted in the wild. Mespinoza originally used the .locked extension on encrypted files, and then shifted to using .pysa. Because of this, many use the names PYSA and Mespinoza interchangeably.
PYSA, like many known ransomware families out there, is categorized as a ransomware-as-a-service (RaaS) tool. This means that its developers have rented out this ready-made ransomware to criminal organizations, who may not be technically savvy enough to produce their own. PYSA customers can customize it based on options provided by the RaaS groups, and deploy it to their liking. PYSA is capable of exfiltrating data from its victims before encrypting the files to be ransomed.
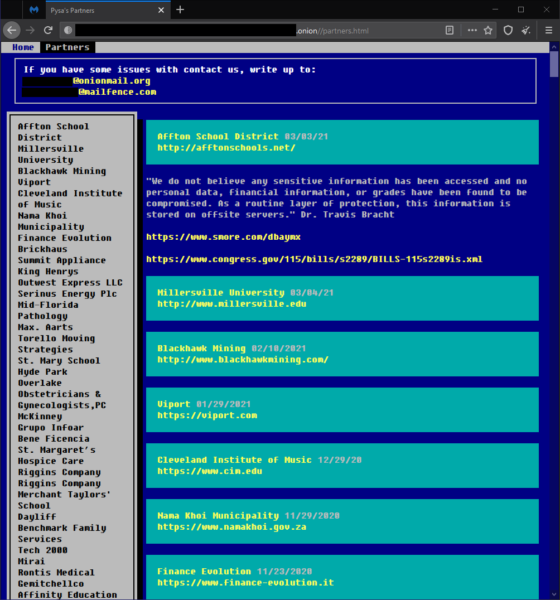
According to Intel 471, a threat intelligence company, PYSA/Mespinoza is a tier 2 RaaS operator as it has been gaining reputation in the underground. Operators or crews who do this have a page—called a “leak list”—where they name and shame victims who decide not to pay the ransom. Victims are listed with an accompanying attachment containing files the threat actors exfiltrated from them.
PYSA ransomware has at least three known infection vectors: Brute-force attacks against management consoles and Active Directory (AD) accounts, phishing emails, and unauthorized Remote Desktop Protocol (RDP) connections to domain controllers. Once inside a network, the threat actors take their time scanning files using Advanced Port Scanner and Advanced IP Scanner, both are free software, and move laterally within the network using PsExec.
The threat actors then manually execute the ransomware within the network after exfiltrating all the data they need for leverage. Files are encrypted using AES implemented with RSA-encrypted keys.
Who has been attacked by PYSA?
PYSA is known to target large private organizations and those belonging in the healthcare industry. They have also hit government groups across multiple continents. Recently, PYSA has increasingly been used against educational institutions in the US and UK.
Below is a non-exhaustive list of incidents involving PYSA:
- In March 2020, CERT France issued a warning to French local governments of PYSA’s increased attacks.
- In May 2020, MyBudget, Australia’s money management firm, experienced an “outage” that lasted 13 days (from 9 May to 22 May). Leaks of exfiltrated data landed on PYSA’s blog. The company then later confirmed to iTWire on 29 May that the long outage was caused by a ransomware attack. The next month, however, sources noticed that MyBudget’s name and files were taken down from PYSA’s blog, leading some to speculate that it may have paid the ransom, despite assurances that it had “no intention of engaging with ransom demands.”
- In October 2020, a “serious cyberattack” affected London’s Hackney Council in the UK, leaving it unable to process housing benefit payments and causing house purchases to fall. Although they were tight-lipped about the entire incident at first, it has become known that the PYSA ransomware threat actors were behind the attack after leaking the data they exfiltrated from the company in January 2021.
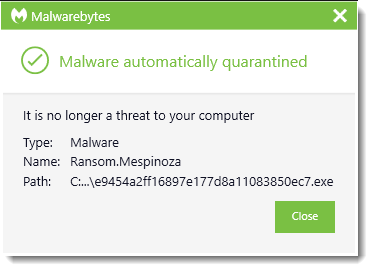
Does Malwarebytes detect PYSA ransomware?
We sure do. We detect is as Ransom.Mespinoza.
Indicators of compromise (IOCs)
SHA256 hashes:
- 7fd3000a3afbf077589c300f90b59864ec1fb716feba8e288ed87291c8fdf7c3
- e9662b468135f758a9487a1be50159ef57f3050b753de2915763b4ed78839ead
- a18c85399cd1ec3f1ec85cd66ff2e97a0dcf7ccb17ecf697a5376da8eda4d327
- 327934c4c11ba37f42a91e1b7b956d5a4511f918e63047a8c4aa081fd39de6d9
- e4287e9708a73ce6a9b7a3e7c72462b01f7cc3c595d972cf2984185ac1a3a4a8
- 327934c4c11ba37f42a91e1b7b956d5a4511f918e63047a8c4aa081fd39de6d9
- f0939ebfda6b30a330a00c57497038a54da359e316e0d6e6e71871fd50fec16a
- 48355bd2a57d92e017bdada911a4b31aa7225c0b12231c9cbda6717616abaea3
- 0f0014669bc10a7d87472cafc05301c66516857607b920ddeb3039f4cb8f0a50
- 61bb42fe06b3511d512af33ef59baa295b29bd62eb4d0bf28639c7910a65e4ae
- 425945a93beb160f101d51de36363d1e7ebc45279987c3eaf5e7f183ed0a3776
- a18c85399cd1ec3f1ec85cd66ff2e97a0dcf7ccb17ecf697a5376da8eda4d327
- 5510ae74b7e2a10fdafa577dc278612f7796b0252b7d1438615e26c49e1fc560
- 1a0ff707938a1399e23af000567806a87fff9b8789ae43badb4d28d4bef1fb81
- b1381635c936e8de92cfa26938c80a359904c1d709ef11ee286ba875cfb7b330
Ransom note file, Readme.README, containing the following content:
Hi Company,
Every byte on any types of your devices was encrypted.
Don’t try to use backups because it were encrypted too.To get all your data back contact us:
{2 @protonmail.com email addresses}————–
FAQ:
1.
Q: How can I make sure you don’t fooling me?
A: You can send us 2 files(max 2mb).
2.
Q: What to do to get all data back?
A: Don’t restart the computer, don’t move files and write us.
3.
Q: What to tell my boss?
A: Protect Your System Amigo.
The post PYSA, the ransomware attacking schools appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



