Ransomware isn’t going away – the problem is only getting worse
As the world moves steadily to becoming more and more digital, organizations worldwide become increasingly dependent on IT systems to run their services. Threat actors know this fact very well.
A short time ago, cyberattacks were used to spread computer viruses to bring harm to target systems, such as making them unstable. However, as modern attack tools developed, a new devastating criminal model appeared that could both harm targeted systems, and extort money from victims by encrypting their files, and taking them hostage.
The new attack model is called ransomware, and it is gaining more momentum year after year.
According to a recent report by Malwarebytes, Global ransomware attacks have witnessed a boost in 2023. The report recorded 1,900 ransomware attacks against four countries—the US, Germany, France, and the UK—in one year.
Ransomware attacks become costly over time too, Cyber Security Ventures predicts by 2031, a ransomware attack will occur every two seconds, costing the world around $265 billion (USD) of losses annually.
Is ransomware exclusively focused on big organizations?
Most recorded ransomware attacks target big organizations; however, this is no longer the case. Ransomware operators are more frequently targeting small and medium-sized businesses as well as individuals. For instance, with back-to-school, ransomware has risen against schools.
According to the Recorded Future, at least 27 schools and districts were hit with ransomware this August (see Figure 1).
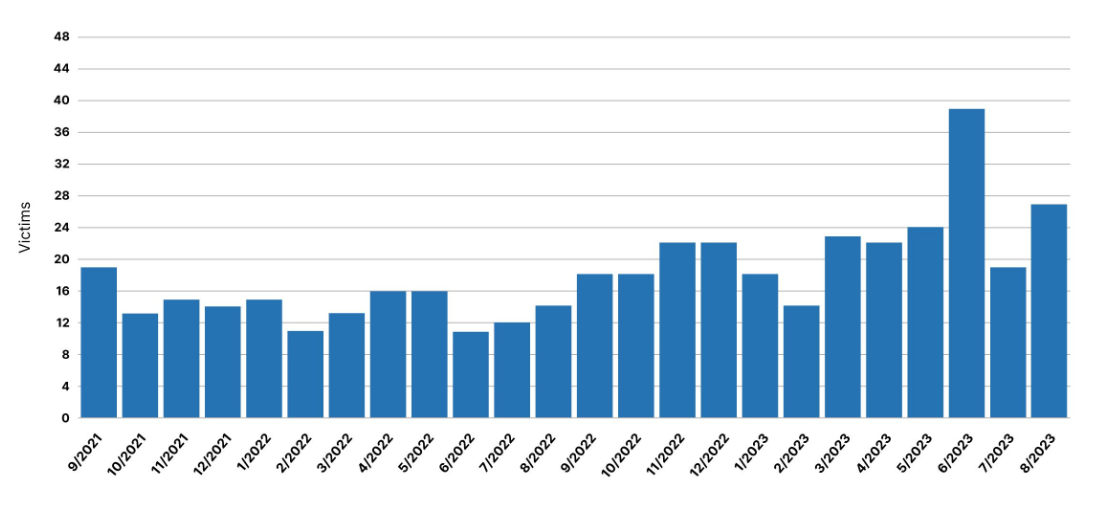
Source: https://therecord.media/ransomware-tracker-the-latest-figures
The ransomware as a Service (RaaS) business model enables cybercriminals lacking technical skills to launch ransomware attacks without developing them. RaaS operators provide the ransomware payload, infrastructure, and payment systems in exchange for an affiliate fee based on successful ransoms.
This allows novice attackers to launch devastating ransomware campaigns against various targets and help accelerate the spreading of ransomware attacks worldwide.
Recent ransomware attacks
Almost every day, we hear in the news about a major ransomware incident that hit a major organization; here are some recent ransomware incidents:
- The LockBit ransomware group launched a ransomware attack against Oakland city in April 2023, ceasing 311 public service
- The Royal ransomware hit the city of Dallas IT infrastructure, resulting in ceasing many public services and exposing the personal information of 26,212 residents of Texas
- The ransomware attack against Harvard Pilgrim Health Care in April 2023 resulted in accessing 2,550,922 of patients’ medical data
Ransomware gangs are using more advanced techniques to infect their targets
The huge profits gained from ransomware attacks have made it a lucrative method for cybercriminals to earn money. Ransomware groups often base their ransom demands on a percentage of the victim company’s annual revenue, usually around 3%.
Hackers invest parts of the ransom payments to develop more robust attack tools and to invent new attack methods. Here are some ransomware attack techniques:
- Outsourcing initial access to target IT environments to Access Brokers to gain access to target networks through phishing, exploit kits or stolen credentials so they can deploy their ransomware
- Exploiting zero-day vulnerabilities in target security controls and applications to gain access
- Using legitimate penetration testing tools, such as Cobalt Strike, to deliver the payloads
- Compromising websites and using them to distribute exploit kits to site visitors. Which allows attackers to exploit vulnerabilities in visitors’ web browsers and operating system
A common method for ransomware operators to access targets IT environments is password-related attacks. For instance, credentials stuffing, password spraying, password reset abuse, phishing attacks, password guessing and exploiting default passwords are common password-based attacks leveraged by ransomware groups.
The LockBit ransomware was the most deployed ransomware variant in 2022 and continues to be widespread in 2023.
The LockBit operators leverage sophisticated techniques to attack their targets, mainly via password-related attacks, such as:
- Executing customized phishing attacks (Spearphishing) against well-researched targets
- Execute brute-force attacks against enterprises internet facing applications, such as RDP and VPN
- Purchasing stolen access credentials from darknet marketplaces, such as TOR network
- Using security tools such as Mimikatz to gather credentials from target systems memory to gain unauthorized access and to escalate privilege
How do hackers monetize and exploit bad password behaviors?
There are numerous ways that hackers take advantage of poor password practice:
- Credential stuffing: Hackers use previously compromised username/password pairs to access other accounts where users use the same credentials. It is common for users to reuse the same password to secure multiple online accounts, which makes this attack achievable
- Brute-force attacks: Hackers guess users passwords using automated tools, such as John the Ripper and Cain and Abel
- Password spraying: Attackers prepare a list of usernames and then try a common password (e.g., default password) to try login into all these accounts
- Phishing attacks: Hackers create fake login webpages resembling legitimate webpages and trick users into entering their account credentials, which the hackers then gather
- How Specops Password Policy can help you mitigate ransomware attacks?
To halt ransomware attacks that take advantage of end-users weak password practices, it is advisable to use Specops Password Policy, which extends the functionality of Group Policy in Active Directory and provides advanced password policy features, including:
- Custom dictionary list to block the use of passwords that can be commonly used in your organization, like company name and location
- Settings to combat predictable composition patterns like reusing part of the old password, consecutive characters, and incremental characters
- Breached password protection with daily checks to block the use of over 4 billion unique compromised passwords found on known breached lists
- Passphrase support
Ransomware continues to evolve as a preferred cybercriminal business model.
To fight ransomware, organizations must boost their cyber defenses using a layered security model that involves enforcing strong password policies and deploying different security solutions.
For instance, most ransomware attacks begin with a compromised password, so blocking the use of over 4 billion unique compromised passwords helps prevent all cyberattacks that take advantage of this attack vector.
Sponsored and written by Specops Software.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


![[QILIN] - Ransomware Victim: Culver's Lawn & Landscape, Inc[.] 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

