Redirect auction

We’ve already looked at links under old YouTube videos or in Wikipedia articles which at some point turned bad and began pointing to partner program pages, phishing sites, or even malware. It was as if the attackers were purposely buying up domains, but such a scenario always seemed to us too complicated. Recently, while examining the behavior of one not-so-new program, we discovered how links get converted into malicious ones.
Razor Enhanced, a legitimate assistant tool for Ultima Online, caught our eye when it started trying to access a malicious URL.
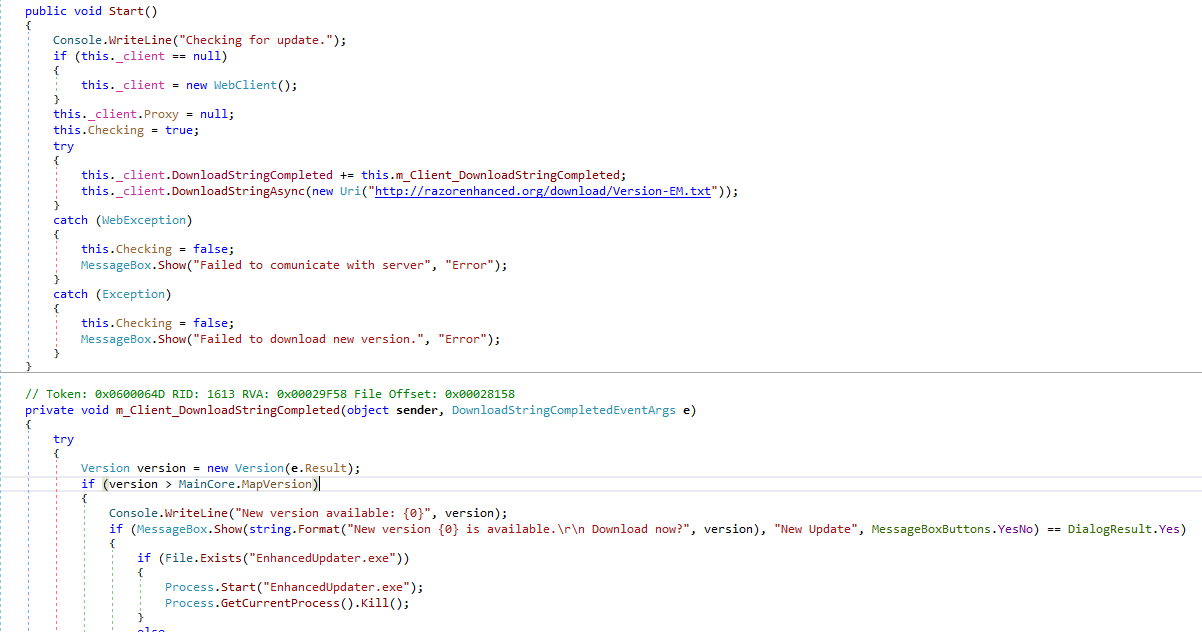
C# program code for installing an update
Since we didn’t find anything suspicious in the program code, it was clear that the problem was on the other side. Going to the site that the program had tried to access, we found a stub for a popular domain auction stating that the domain was up for sale. The WHOIS data told us that its owner had stopped paying for the domain name, and that it had been purchased using a service for tracking released domains, and then put up for sale on the auction site.
To sell a domain at auction, it must first be parked on the DNS servers of the trading platform, where it remains until being transferred to the new owner. Anyone who visits the site sees that stub.
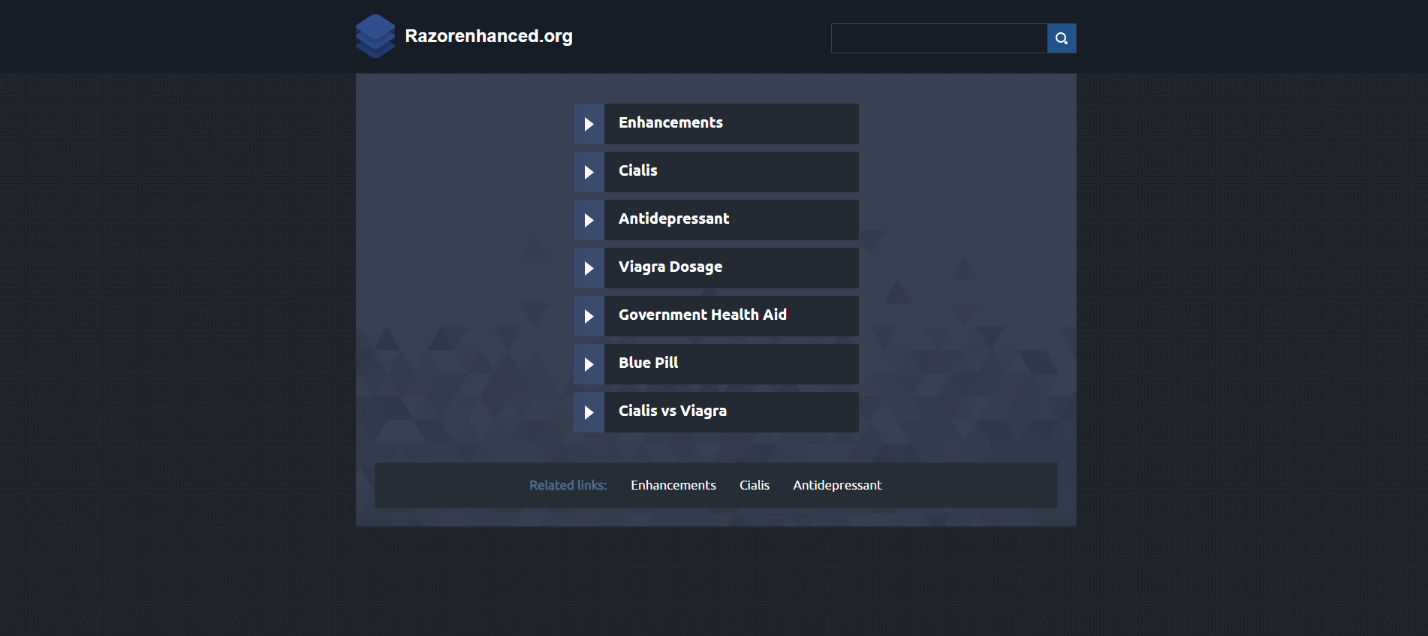
Stub on the domain up for sale
Having observed this page for a while, we noticed that from time to time visitors who initially went to the now inactive website of the app developer did not land on the auction stub, but on a malicious resource (which is basically what happened with Razor Enhanced when it decided to check for updates). Next, we learned that the stub site redirects visitors not to a specific resource, but to different websites, including ones on partner networks. What’s more, the type of redirect can vary depending on the country and user agent: when accessing from a macOS device, the victim might land on a page that downloads the Shlayer Trojan.
We checked the list of addresses from which Shlayer was downloaded, and found that the vast majority of domain names had been put up for auction on the same trading platform. Then we decided to check the requests to the resource that Razor Enhanced users got redirected to, and found that around 100 other stubs on this trading platform sent their visitors to the same address. During the study, we found about 1,000 of these pages in total, but the real figure is probably much higher.
According to data for March 2019–February 2020, 89% of the sites to which requests from stub pages got redirected were ad-related. The remaining 11% posed a far more serious threat: they prompt the user to install malware or download malicious MS Office or PDF documents with links to fake websites and the like.
We can assume that one source of income for the cybercriminals comes from generating traffic to partner program pages, both advertising and malicious (malvertising). For instance, one such resource in ten days receives (on average) around 600 redirect requests from programs which, like Razor Enhanced, were trying to access a developer site.
Who’s behind it?
There are various hypotheses. More likely: the malicious redirects are the work of a module that displays the content of a third-party ad network. Malicious traffic can appear due to the lack of ad filtering or because the attackers use vulnerabilities in the advertising module (or the trading platform itself) to change settings and substitute redirects.
It’s too early to draw any definite conclusions, but based on the data collected so far, it can be assumed that we are dealing with a well-organized (and presumably managed) network that can divert traffic flows to cybercriminal sites, using redirects from legitimate domain names and the resources of one of the largest and oldest domain auctions.
The main problem for visitors to legitimate resources is that without a security solution they will not be able to prevent getting redirected to a malicious site. Moreover, some visitors of such sites might go there by typing in the address from memory, clicking a link in the About window of an app they are using, or finding them in search engines.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[LYNX] - Ransomware Victim: Greta Group 5 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
