Remote Code Execution Risks in Secomea, Moxa, and HMS eWon ICS VPN Vulnerabilities: What You Need to Know
On Wednesday, July 28, 2020, researchers at Claroty released information on a number of critical remote code execution vulnerabilities across products of three industrial control system (ICS) vendors’remote access technologies: HMS, Secomea, and Moxa. Rapid7 has aggregated these vulnerabilities into a single AttackerKB meta-topic reference to help defenders keep up-to-date with the latest developments.
The following CVEs have been assigned to these weaknesses:
- Secomea GateManager:
- CVE-2020-14500
- CVE-2020-14508
- CVE-2020-14510
- CVE-2020-14512
- Moxa EDR-G902/3 industrial VPN servers:
- CVE-2020-14511
- HMS Networks eCatcher VPN clients:
- CVE-2020-14498
And, the following vendor patches are available:
- HMS eWon Patches: https://ewon.biz/technical-support/pages/all-downloads
- Secomea: https://kb.secomea.com/helpdesk/KB/Category/402879-software–firmware
- Moxa: https://www.moxa.com/en/support/product-support/software-and-documentation
Rapid7 strongly recommends that organizations using these technologies immediately assess their internet-facing ICS remote configurations to ensure only protocols and services that need to be exposed to the internet are configured and that these specific devices and services are patched as soon as possible. A number of these patches have been available since early June and early July.
The U.S. ICS CERT/CISA have issued advisories for these vulnerabilities, noting that many of them are trivial to exploit.
Extended/Exposure Analysis
In this post, we’re focusing mainly on the remote code execution risks, though in this age of rampant phishing attacks, the user-interaction-required weaknesses in HMS eWon VPNs should not be taken lightly by organizations using that technology.
Secomea GateManager is used widely in ICS deployments and the weakness in HTTP request header handling can lead to unauthenticated remote code execution, providing an attacker full access to secured networks and complete visibility into all VPN traffic.
Moxa EDR-G902/3 industrial VPN servers have an HTTP request processing weakness that can be exploited to trigger an unauthenticated stack-based overflow on the web server with the potential for remote code execution.
Rapid7 Labs is working on extending our fingerprinting capabilities of these technologies, but have discovered nearly 900 Secomea GateManager and Moxa HTTP endpoints (combined view below) and a myriad of Secomea versions, which the gateways provide directly in the HTML login page:
| Secomea Version | Count |
|---|---|
| 9.2.620276048 | 73 |
| 8.4.18513 | 70 |
| 8.3.18404 | 45 |
| 9.2.620087463 | 38 |
| 9.1.620042008 | 31 |
| 9.0.19405 | 27 |
| 9.2.620236042 | 27 |
| 8.2.18335 | 20 |
| 8.0.18185 | 15 |
| 9.0.20042 | 14 |
| 9.0.20262 | 14 |
| 8.1.18253 | 13 |
| 9.0.19361 | 13 |
| 9.0.19285 | 10 |
| 9.1.620021003 | 8 |
| 9.0.20276 | 7 |
| 8.3.19081 | 6 |
| 9.0.19476 | 4 |
| 9.1.619473004 | 4 |
| 9.3.320254470 | 4 |
| 9.3.320293549 | 4 |
| 9.2.620172023 | 3 |
| 9.2.320091465 | 2 |
| 9.3.120285539 | 2 |
| 9.3.320116615 | 2 |
| 9.1.620085009 | 1 |
| 9.2.319521179 | 1 |
| 9.3.320153146 | 1 |
| 9.3.320285540 | 1 |
| 9.3.320295000 | 1 |
| 9.3.320311565 | 1 |
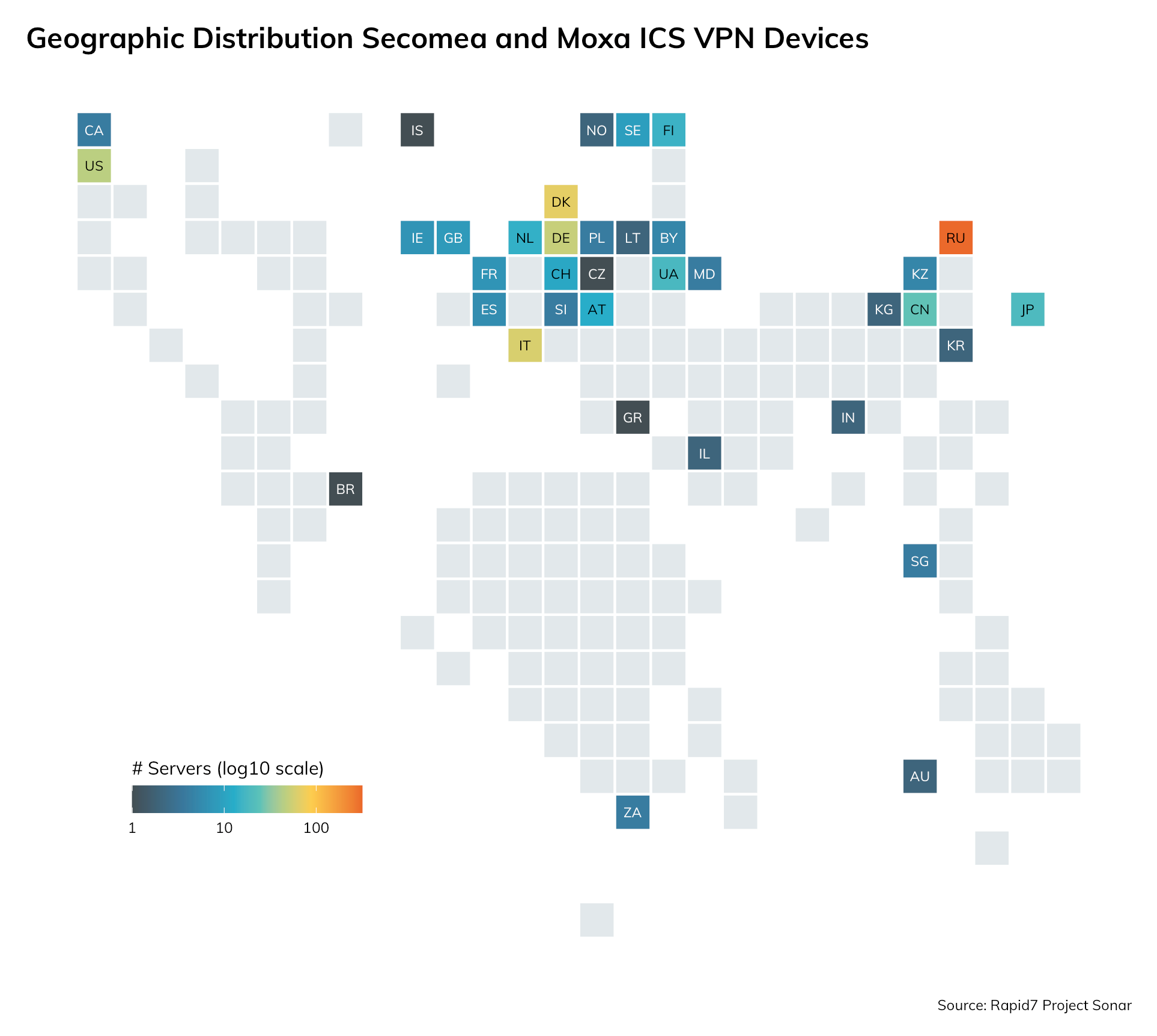
While this number pales in comparison to exposure counts of many other, recent remote code execution disclosures, these devices protect industrial control systems and networks, meaning successful attackers may be able to do real, physical-world harm once they’ve successfully compromised one or more of these VPN systems.
We call out HTTP specifically since the vulnerabilities discovered by Claroty are within that component. However, significant attention has been drawn to these ICS systems which may lead to other avenues of exploitation. For example, there are nearly 1,900 Moxa VPN gateways exposing their Telnet administration port to the internet, ¾ of which provide version, MAC address and other configuration information, with 1% not requiring passwords to completely access or reconfigure the systems. Upon examining some of the Moxa HTTP web responses, many do not seem to require authentication to change critical configuration settings. Furthermore, there are thousands more Moxa systems providing detailed configuration over a custom UDP protocol.
Given the media and technologist attention being paid to these disclosures, both attacker and “researcher” attention will be focused on these new and existing weaknesses and organizations should be prepared for critical attacks if these systems are not secured.
Given the “cloud” nature of the Secomea systems, Rapid7 Labs is keeping an eye on Project Heisenberg for any unusual HTTP activity on known, popular access and administrative ports for these systems.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[SARCOMA] - Ransomware Victim: CARSTAR Business Group 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)


