Russian hackers switch to LOTL technique to cause power outage

Russian state hackers have evolved their methods for breaching industrial control systems by adopting living-off-the-land techniques that enable reaching the final stage of the attack quicker and with less resources.
Security researchers highlight that the change opens the door to attacks that are more difficult to detect and don’t necessarily require sophisticated malware for industrial control systems (ICS).
Native binary to send commands
Last year, the Sandworm threat group breached a Ukrainian critical infrastructure organization in an attack that required less than four months to reach the final phase, a power outage that was doubled by missile strikes on critical facilities across the country.
Sandworm is a hacker group active since at least 2009 and linked to Russia’s General Staff Main Intelligence Directorate (GRU). It is focused on targeting industrial control systems (ICS) and engages in espionage and destructive cyberattacks.
In late 2022, incident responders at Google-owned Mandiant responded to a disruptive cyberattack in Ukraine, which they attributed to Sandworm, and analyzed the tactics, techniques, and procedures.
The researchers determined that Sandworm had started the intrusion since at least June 2022 and obtained access to the operational technology (OT) environment through a hypevisor hosting a MicroSCADA server, which enables centralized control and automates operation of the entire power distribution system.
“Based on evidence of lateral movement, the attacker potentially had access to the SCADA system for up to three months” – Mandiant
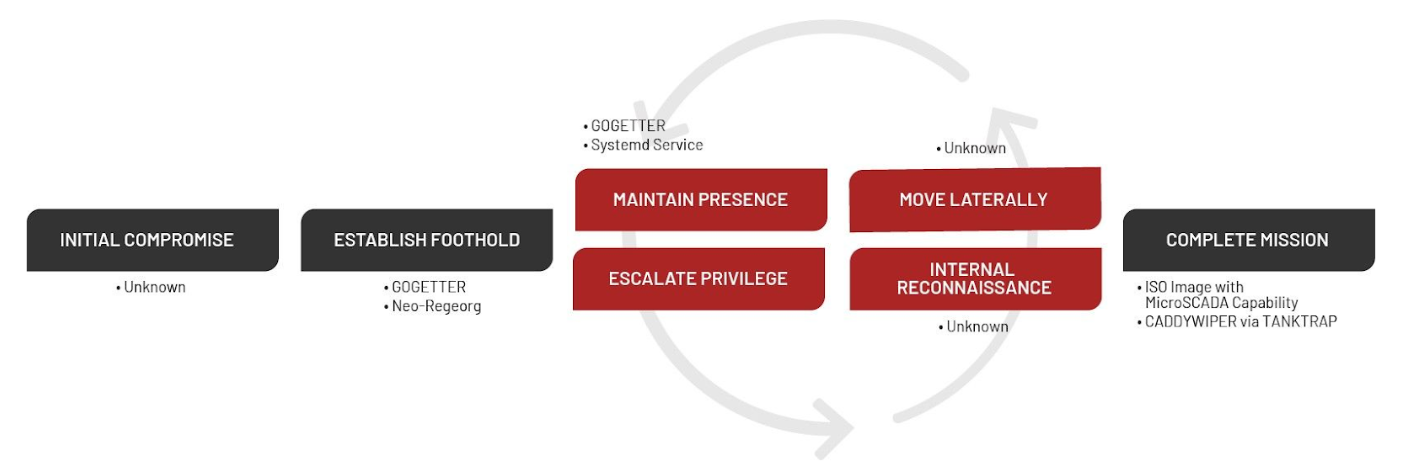
Although the initial attack vector remains unknown at this time, the researchers note that Sandworm activity was first observed in June 2022, with the deployment of the Neo-REGEORG webshell on a server exposed on the public internet.
After one month, the hackers executed the Golang-based GOGETTER tunneler to proxy encrypted communications for the command and control (C2) server using the Yamux open-source library.
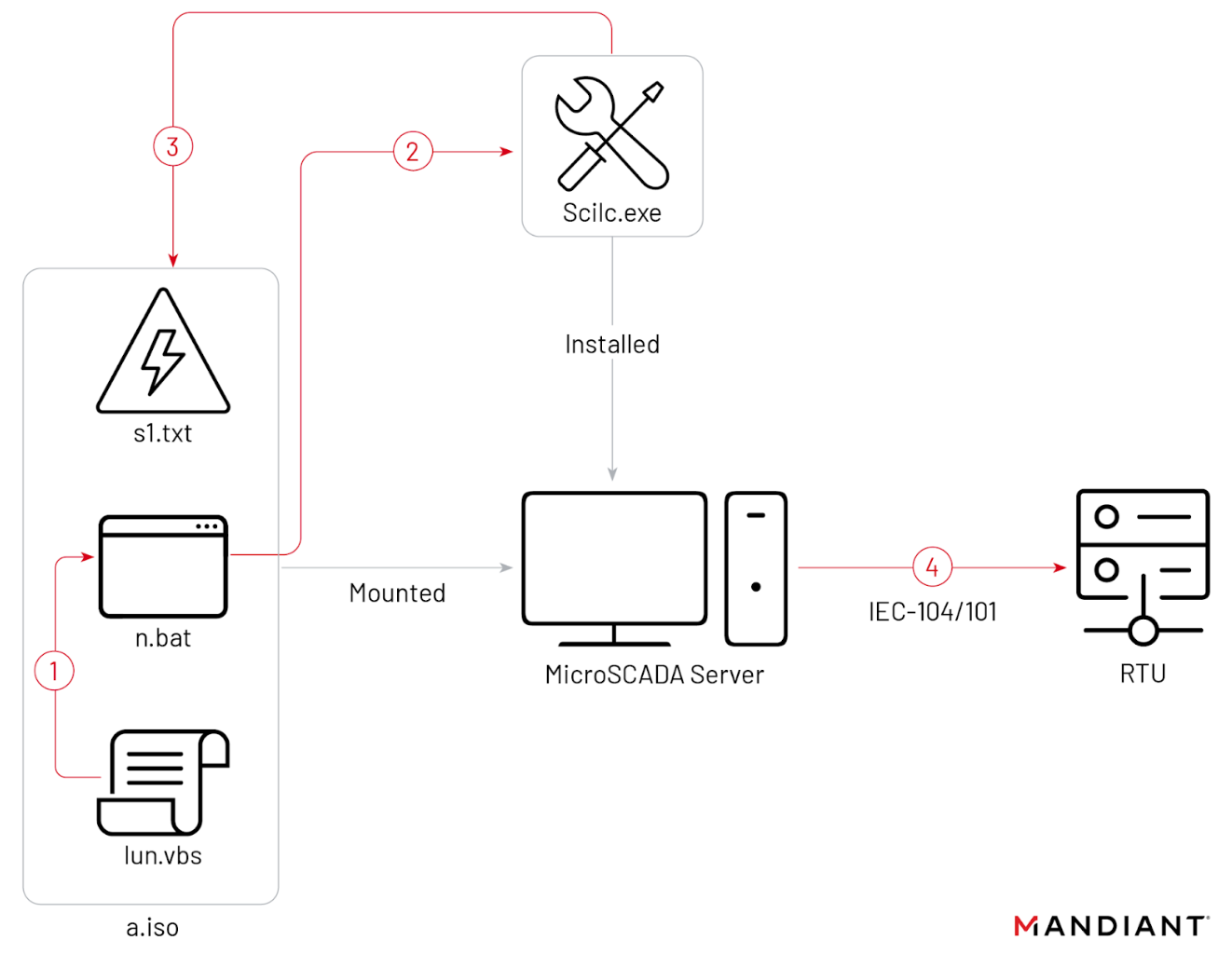
The attack culminated two disruptive events. One was a power outage on October 10, 2022, when Sandworm used an ISO CD-ROM image file to run the native MicroSCADA utility scilc.exe, likely to run malicious commands that would switch off the substations.
Loading the ISO image was possible because the virtual machine MicroSCADA was running on had the autorun feature enabled, allowing CD-ROMs, physical or virtual (e.g. an ISO file) to run automatically.
Source: Mandiant
The scilc.exe utility is part of the MicroSCADA software suite and Sandworm used it to run SCIL (a high-level programming language for MicroSCADA) commands that the server would relay to the remote terminal units (RTU – field devices) in the substation.
According to the researchers’ findings, the compromised MicroSCADA server was running an end-of-life software version that allowed default access to the SCIL-API.
Using a native binary (LoLBin) in the attack indicates the hackers’ shift to living-off-the-land (LoL/LOTL) techniques that rely on more lightweight and generic tools, which make threat activity more difficult to detect.
Inside the ISO file there were at least the following three files:
- “lun.vbs”, which runs n.bat
- “n.bat”, which likely runs the native scilc.exe utility
- “s1.txt”, which likely contains the unauthorized MicroSCADA commands
The researcher found that the lun.vbs script had a September 23 timestamp, which suggests that the hackers had about two months to develop their OT capability since the initial access stage.
source: Mandiant
The second disruptive event occurred on October 12, 2022, when Sandworm deployed a new version of the CADDYWIPER data-destroying malware, likely an effort to further disrupt the environment and remove traces of the attack.
“However, we note that the wiper deployment was limited to the victim’s IT environment and did not impact the hypervisor or the SCADA virtual machine” – Mandiant
The researchers note that this action was unusual because the the threat actor had already removed other forensic artifacts from the SCADA system. They believe this could point to “a lack of coordination across different individuals or operational subteams involved in the attack.”
Clues uncovered during the investigation of the attack indicate that the hackers were ready for the disruption of the systems at least three weeks before it happened.
There isn’t sufficient evidence to support this theory but the researchers believe that Sandworm may have waited for a specific moment to complete the mission.
“The eventual execution of the attack coincided with the start of a multi-day set of coordinated missile strikes on critical infrastructure across several Ukrainian cities, including the city in which the victim was located” – Mandiant
Sandworm doesn’t need custom malware
In the report published today, Mandiant highlights that the techniques used in the attack “suggest a growing maturity of Russia’s offensive OT arsenal” that translates into an increased ability to recognize new OT threat vectors, developing new capabilities, and leveraging different types of OT infrastructure for their attacks.
Combined with the switch to living-off-the-land techniques, the researchers believe that Sandworm is likely capable to carry out attacks against OT systems from different vendors.
Nathan Brubaker, Mandiant head of emerging threats and analytics, Google Cloud, told BleepingComputer that Sandworm’s threat activity outside Ukraine would not be limited by its capability but guided by the motivation to attack.
The researcher says that the novelty in this attack is its agile nature and this would allow Sandworm to attack “other environments more easily than with some sophisticated ICS malware.”
Brubaker underlines that Sandworm did not use custom malware for the OT part of the attack but resorted to a LoL binary, which requires OT expertise and understanding the targeted industrial processes, the technology used in the attack (MicroSCADA in this case) being less notable.
“There is no reason Sandworm could not replicate a similar type of attack in another environment with different technology,” Brubaker concluded.
Mandiant’s report includes indicators of compromise, YARA rules, guidance to harden SCADA management hosts, and recommendations that can help defenders detect Sandworm’s activity in ICS environments and mitigate the threat.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[QILIN] - Ransomware Victim: www[.]nuphoton[.]com 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)