SearchDimension search hijackers: An overview of developments
Background information on SearchDimension
SearchDimension is the name of a family of browser hijackers that makes money from ad clicks and search engine revenues. The family was named after the domain searchdimension.com that popped up in 2017, and they still sometimes use the letter combo SD in the names of their browser extensions.
Recent developments in the SearchDimension family
Over the last year we have seen this family evolve and expand into the world of PUPs and adware. Below are some of the latest additions to their arsenal.
- Web push notifications: together with Adware.Adposhel, SearchDimension was among the first families to make full use of the potential provided by web push notifications for advertising.
- Your browser is managed: the SearchDimension developers created an installer that not only installed their search hijacking extension but also made the “Remove” button disappear on the extension listing, telling frustrated users their browser was not their own to manage
- One of their most recent additions is a Chromium-based browser that replaces your default browser when you install it. This new default browser then behaves the same as a normal Chrome browser with one of the search hijacker extensions installed.
- Another new trick comes with extensions that read your browser history to grab the search term the user looked for. The extension then closes the original search tab and opens a new tab with their own search engine looking for that search term. Basically this comes down to lying about the permissions so users will not notice the extension as a search hijacker.
How can you recognize SearchDimension hijackers?
There are many subfamilies and different versions within those families, but there are some tell-tale signs of the SearchDimension family. First and foremost, they use a few website templates that are very typical. These are the six most common ones.
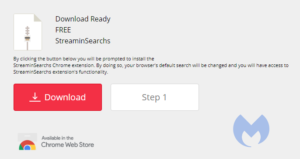
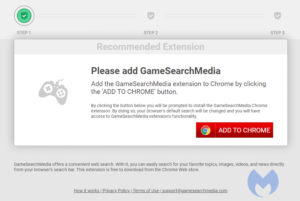
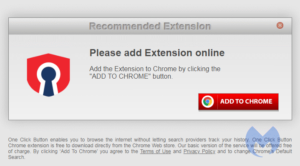
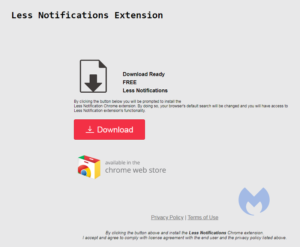
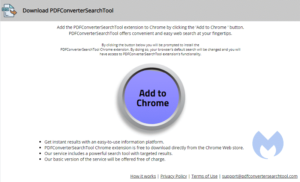
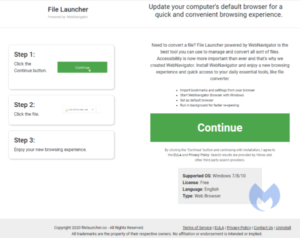
Depending on the referring websites, you may be asked to accept notifications from the search hijacker’s domain. Every domain I have seen from them recently has this option but the referring URL does not always trigger this behavior. So, anyone directly visiting such a domain will not see the notifications prompt.
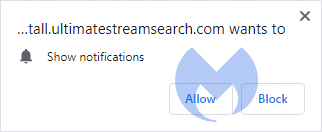
Then there is one page that comes up very often after you have installed one of the extensions. It looks like this:

The name of the extension and the “sponsors” will vary but the blue and white fields with the circular logo are very typical for the “Thank you for installing … “ page.
The wording in the entry in the list of installed Chrome extensions also comes from a rather limited set, and will usually have one of these formats:
- Search by {extension name}. The best way to search. This one is by far the most common.
- This extension configures your Default Search in Chrome browser to provide these features. Which features remain unsaid.
- {extension name} is an extension that replaces your default search to Yahoo to provide more features. This one seems very specific for the PUP.Optional.SearchDimension subfamily.
Another weak spot in the development process for new variants seems to be the icon. Although they have come up with a lot of them, there is one that is repeated a lot.
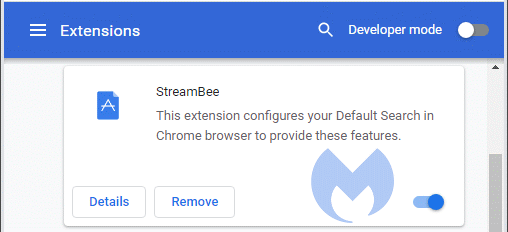
The “A” in a blue field is often used for variants that have a short life span. These variants are often only around for a few days before they get removed from the Webstore.
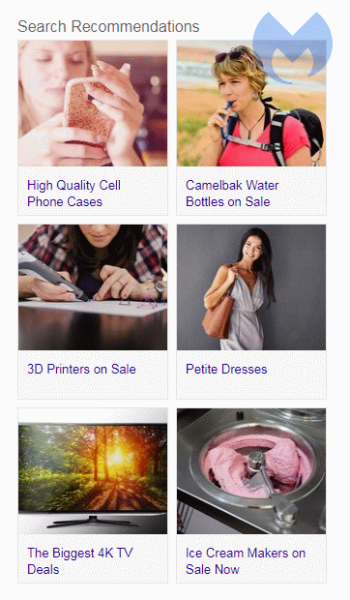
Some variants, including the WebNavigator browsers, add a table of graphics representing Search Recommendations to the search results. This will look like this:
Different subfamilies of SearchDimension
One could divide this family up into subfamilies, based on their behavior, and at Malwarebytes we detect these subfamilies under different names. Below you will find a short description of the methods these subfamilies use and whether there is a Malwarebytes’ detection name for that subfamily.
- The web push notifications are a part of all the subfamilies. If the user has accepted web push notifications, Malwarebytes will detect them as PUP.Optional.PushNotifications.Generic.
- The subfamily that only uses the trick to close and open a new search tab will be detected by Malwarebytes as PUP.Optional.SearchEngineHijack.Generic.
- The variants that change the default search engine and the ones that show “Search Recommendations” will be detected by Malwarebytes as Adware.SearchEngineHijack.Generic.
- The subfamily that consists of Chromium-based browsers that replace your default browser is detected by Malwarebytes as PUP.Optional.WebNavigator.
Unfortunately, as some of these subfamilies use more than one method of browser hijacking, it is hard to be consistent. So sometimes detection names do not always completely follow this pattern as it depends on which behavior(s) our engine detects. The big advantage of the generic detections by our engine, however, is that it picks up new variants on their first appearance.
Advice on search hijackers and other adware
Changing your default search provider or installing adware should be done with user consent. Which is something these search hijackers often forget. They try to get installed by making promises they do not intend to keep and “forget to mention” what they actually are up to. We have seen search hijackers promising to be ad blockers, privacy protectors, and even ones that promise to provide antivirus protection. At best, they replaced existing advertisements with their own.
Installing a browser extension just to change your default search provider is something I would advise against. It’s easy enough to change the default search engine in the browser settings, and if the one of your choice is not listed there, I would recommend you only install an extension with a proven track record and one that really adds some value.
It’s an error to think that these search hijackers only bother Windows users. Most of the prevalent search hijackers aim at Chrome/Chromium browsers and sometimes Firefox. As a consequence, most of them can also be installed on macOS systems.
Recommended reading
For those interested in this subject, I have gathered some related links.
Removal methods:
How to remove adware from your PC
Browser push notifications: a feature asking to be abused
Adware the series, part 1
Awareness:
Mac adware is more sophisticated and dangerous than traditional Mac malware
Three million users installed 28 malicious Chrome or Edge extensions
Stay safe, everyone!
The post SearchDimension search hijackers: An overview of developments appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



![[HANDALA] - Ransomware Victim: Hotam EC 13 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)