Segway store compromised with Magecart skimmer
In the early 2000’s, the Segway company released a personal transporter that would become iconic. The Segway Human Transporter was quickly sold on Amazon and featured in a number of movies.
Since 2015, Segway has been a subsidiary of Chinese-based company Ninebot and sells electric scooters under the Ninebot brand. By 2020, a number of changes in personal transportation forced the company to halt production of its famous Segway PT.
Our web protection team recently identified a web skimmer on Segway’s online store. In this blog we will review the attack and tie it back to a previous campaign that is attribute to Magecart Group 12. We already have informed Segway so that they can fix their site, but are publishing this blog now in order to raise awareness.
Magecart-style attack
Stefan Dasic, from our web protection team, identified a connection to a known skimmer domain (booctstrap[.]com) loaded by the Segway store. This domain has been active since November and is connected to a previously documented campaign sometimes referred as “ant and cockcroach”.
The hostname at store.segway[.]com is running Magento, the popular Content Management System (CMS) used by many e-commerce sites and also a a favorite among Magecart threat actors. While we do not know how Segway’s site was compromised, an attacker will usually target a vulnerability in the CMS itself or one of its plugins.
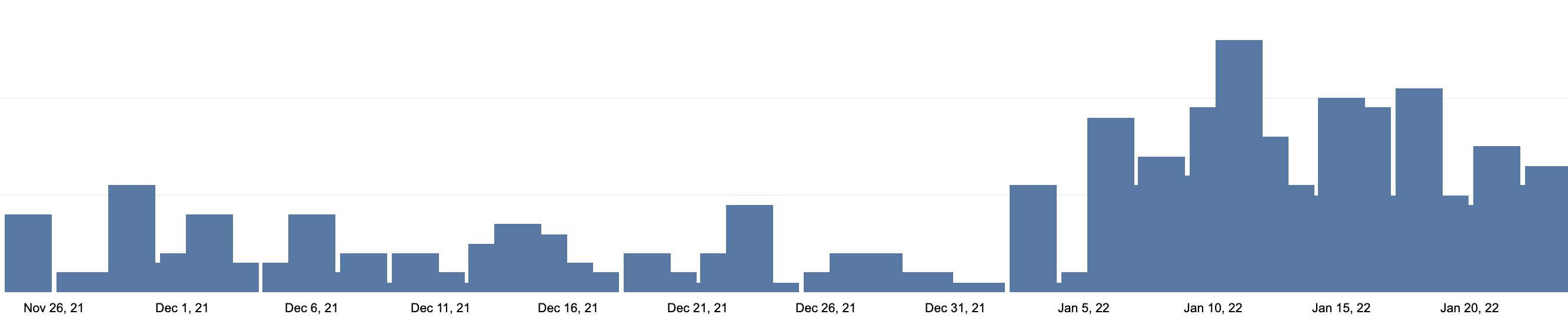
Based on urlscanio data, the website was compromised at least since January 6th. Malwarebytes was already blocking the booctstrap[.]com domain and its hosting server at 185.130.104[.]143 since November. Looking at our telemetry, we can see that the number of blocks (attacks prevented on our customers’ machines) also goes up around the January 6th mark.
The top 5 countries exposed to this skimmer, based on our telemetry data, are:
- United States (55%)
- Australia (39%)
- Canada (3%)
- UK (2%)
- Germany (1%)
Favicon campaign
A fairly long but innocuous piece of JavaScript disguised as ‘Copyright’ is responsible for dynamically loading the skimmer such that it will not be visible by looking at the HTML source code.
Instead, if we check the code via the browser’s debugger we can see how the URL is constructed:
The threat actors are embedding the skimmer inside a favicon.ico file. If you were to look at it, you’d not notice anything because the image is meant to be preserved. However, when you analyze the file with a hex editor, you will notice that it contains JavaScript starting with an eval function.
There is a lot that has been written about this skimmer and the threat group behind it. Sucuri’s Denis Sinegubko covered it and Jordan Herman from RiskIQ also wrote about the numerous ties it shares with a number of incidents that can attributed to Magecart Group 12.
The compromise of the Segway store is a reminder that even well-known and trusted brands can be affected by Magecart attacks. While it usually is more difficult for threat actors to breach a large website, the payoff is well worth it.
Malwarebytes customers were already protected thanks to our website shield available in Malwarebytes for Desktop as well as our Browser Guard extension.
The post Segway store compromised with Magecart skimmer appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[FLOCKER] - Ransomware Victim: G*********************y[.]org 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

