Sigurlx – A Web Application Attack Surface Mapping Tool
sigurlx a web application attack surface mapping tool, it does …:
- Categorize URLs URLs’ categories:
> endpoint
> js {js}
> style {css}
> data {json|xml|csv}
> archive {zip|tar|tar.gz}
> doc {pdf|xlsx|doc|docx|txt}
> media {jpg|jpeg|png|ico|svg|gif|webp|mp3|mp4|woff|woff2|ttf|eot|tif|tiff} - Next, probe HTTP requests to the URLs for
status_code,content_type, e.t.c - Next, for every URL of category
endpointwith a query:- Probe for commonly vulnerable parameters (inspired by Somdev Sangwan’s Parth).
- Probe for reflected parameters (inspired by Tom Hudson’s kxss).
Usage
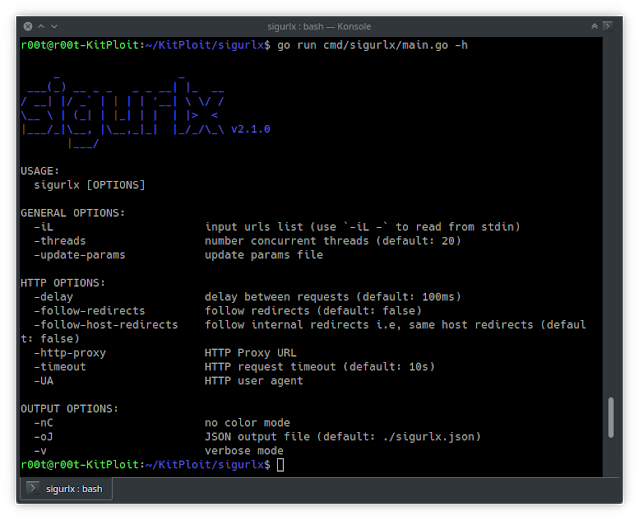
To display help message for sigurlx use the -h flag:
$ sigurlx -h
_ _
___(_) __ _ _ _ _ __| |_ __
/ __| |/ _` | | | | '__| / /
__ | (_| | |_| | | | |> <
|___/_|__, |__,_|_| |_/_/_ v2.1.0
|___/
USAGE:
sigurlx [OPTIONS]
GENERAL OPTIONS:
-iL input urls list (use `-iL -` to read from stdin)
-threads number concurrent threads (default: 20)
-update-params update params file
HTTP OPTIONS:
-delay delay between requests (default: 100ms)
-follow-redirects follow redirects (default: false)
-follow-host-redirects follow internal redirects i.e, same host redirects (default: false)
-http-proxy HTTP Proxy URL
-timeout HTTP request timeout (default: 10s)
-UA HTTP user agent
OUTPUT OPTIONS:
-nC no color mode
-oJ JSON output file (default: ./sigurlx.json)
-v verbose mode
Installation
From Binary
You can download the pre-built binary for your platform from this repository’s releases page, extract, then move it to your $PATHand you’re ready to go.
From Source
sigurlx requires go1.14+ to install successfully. Run the following command to get the repo
▶ go get -u github.com/drsigned/sigurlx/cmd/sigurlxFrom Github
▶ git clone https://github.com/drsigned/sigurlx.git
▶ cd sigurlx/cmd/sigurlx/
▶ go build .
▶ mv sigurlx /usr/local/bin/
▶ sigurlx -h
Contribution
Issues and Pull Requests are welcome!
Download Sigurlx
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.




