Smart Mobility has a Blindspot When it Comes to API Security
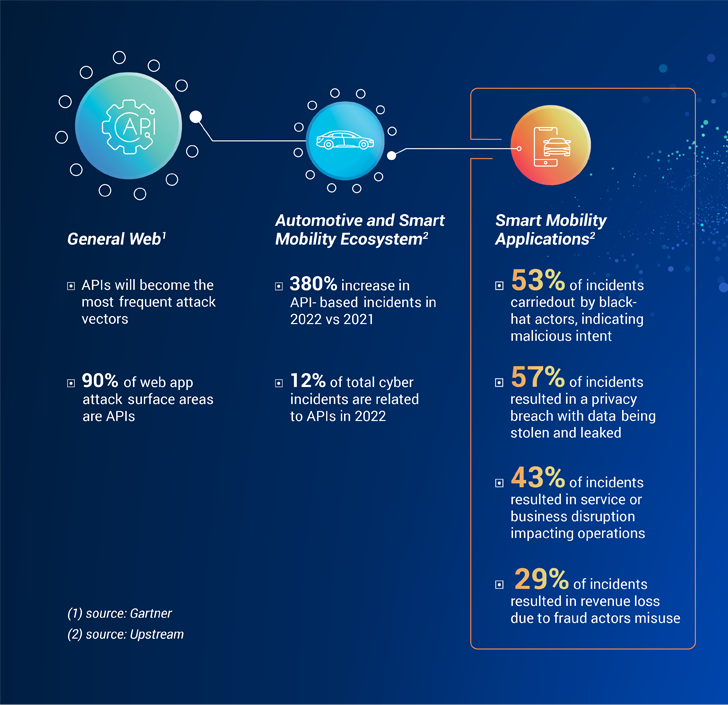
The emergence of smart mobility services and applications has led to a sharp increase in the use of APIs in the automotive industry. However, this increased reliance on APIs has also made them one of the most common attack vectors. According to Gartner, APIs account for 90% of the web application attack surface areas.
With no surprise, similar trends are emerging also in the smart mobility space. A recent Automotive and Smart Mobility Cybersecurity Report by Upstream Security indicates that the automotive and smart mobility ecosystem has seen a 380% increase in API-based incidents in 2022, compared to 2021. Additionally, APIs accounted for 12% of total cyber incidents in 2022, up from only 2% in 2021.
When examining smart mobility applications and services, Upstream’s threat intelligence team reported that black-hat actors were found to be behind 53% of incidents, indicating malicious intent as the driving force of the majority of API-related attacks. The impact of these incidents goes well beyond data and PII breaches, often causing service disruptions, fraudulent activities, trust concerns and potential revenue loss.
Data-driven mobility services reshape traditional automotive revenue models#
In recent years, vehicle connectivity has grown dramatically, introducing innovative data-driven revenue opportunities for traditional automotive stakeholders as well as new players. Mobility overall has become more connected, with ridesharing, car rental services, and even fleet management services all utilizing mobile applications to provide easy access and enhanced experience to consumers. Modern data use cases offer continuous monitoring and help stakeholders introduce new features and opportunities. According to research by McKinsey, 30% of automotive revenue will be attributed to data-driven and smart mobility services by 2030. But unlike IT-based applications, these innovative and data-driven applications heavily utilize APIs that have a direct impact on vehicles on the road.
Massive traffic jams caused by manipulated API transactions #
In 2022, we saw an increasingly sophisticated use of APIs in automotive and smart mobility cyberattacks. As an attack vector, APIs draw the attention of researchers and malicious actors as they require a relatively low threshold of know-how and automotive expertise. Essentially reducing the barrier of entry of threat actors to a minimum. A single vulnerability in an API can pose a direct impact on millions of vehicles, across various fleets. A strong example of the ease of attack and the significant impact can be found in a recent incident in Europe: back in mid-2022 central Moscow was gridlocked when a ride-hailing service was maliciously manipulated to send all available taxis to a single location, causing hours-long traffic jams, impeding people’s freedom of movement, and putting public infrastructure and safety at risk. In this case, attackers didn’t need any understanding of how vehicles operate or function, all they needed to do was to identify API vulnerabilities and exploit them.
WAF is not (always) enough: developing a contextual framework for smart mobility API security#
Smart mobility services have always been monitoring and securing API transactions to avoid revenue loss due to fraud, service downtime, and compromising organizational or users private data. But, traditional API security solutions have a significant “blindspot” when it comes to smart mobility. They often fail to detect sophisticated attacks that impact mobility applications, assets, and consumers due to the lack of contextual analysis of the impact of API transactions on moving vehicles.
Ensuring a strong cybersecurity posture in the smart mobility ecosystem requires expanding the scope to include a contextual analysis of the real-life impact of APIs on mobility assets, including vehicles on the road. API security is gradually evolving to also integrate OT (Operational Technology) aspects that correlate between API traffic, transactions, and the contextual state of mobility assets to provide a strong cybersecurity posture. The goal is to layer API discovery, profiling and monitoring with deep analysis of the behavior of mobility assets and the impact of the specific API transaction on safety. When you take into account how OT assets behave differently to IT assets, be it their ignition status, location, or speed, you can begin to approach securing them in a contextual manner.
Smart mobility players are adopting a new approach to securing smart mobility API transactions, which includes four key steps:
- Map the potential attack surface
- Continuously monitor API traffic
- Apply contextual anomaly detection
- Mitigate and respond to cyber threats
The first step is to understand the potential attack surface as it relates to APIs. This requires inventorying APIs used by services, applications, and third parties, from documentation sources like Swagger as well as the analysis of live, real-time API traffic and transactions. This analysis includes both documented, undocumented or even the depreciated-but-live APIs that might be a “perfect” access point for threat actors.
Once the attack surface is understood, monitoring API traffic helps increase the cybersecurity posture by ensuring that any changes are documented and detected, as well as any misuse of misconfigurations. When monitoring mobility API traffic in real-time, it’s important to consider the ability to handle the scale and complexity of these transactions and recognize any deviations from the normal state of the asset. When a single API call can start the engine of a vehicle or report back the location of a driver – cybersecurity becomes extremely important.
Since smart mobility assets are OT in nature, the context that they are in – their state at a given moment in time – can be used in securing them. Any major deviations or anomalies in their behavior can indicate potential misuse or attack. By correlating the assets state with the API traffic, cyber teams can understand the contextual implications and the impact on applications or users. Seemingly valid requests can sometimes be an indicator of malicious intent. For example, a single IP, though not suspicious initially, that sends requests to multiple vehicles or mobility applications should trigger immediate suspicion and investigation.
Upstream Security has recently taken a step further in the contextual analysis of API transactions. It relies on a robust digital twin, which is a live digital representation of the asset’s state, built on data streams from applications, backend servers, telematics services, and more. As a result, it offers a comprehensive view of all mobility assets and users impacted. Once the attack or misconfiguration has been detected using the unique context provided by understanding the state of the asset, cyber teams can effectively and quickly respond and mitigate potential risks.
This unique mobility–driven approach opens a new scope of API security activities in the smart mobility ecosystem. As innovation in this space is moving so fast, introducing new transportation models, autonomous services and ride-sharing options, eliminating “blindspots” will continue to be a top priority challenge.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below


To keep up to date follow us on the below channels.