Spam and phishing in Q3 2021

Quarterly highlights
Scamming championship: sports-related fraud
This summer and early fall saw some major international sporting events. The delayed Euro 2020 soccer tournament was held in June and July, followed by the equally delayed Tokyo Olympics in August. Q3 2021 also featured several F1 Grand Prix races. There was no way that cybercriminals and profiteers could pass up such a golden opportunity. Fans wanting to attend events live encountered fake ticket-selling websites. Some sites made a point of stressing the tickets were “official”, despite charging potential victims several times the real price of a ticket, and some just took the money and disappeared.
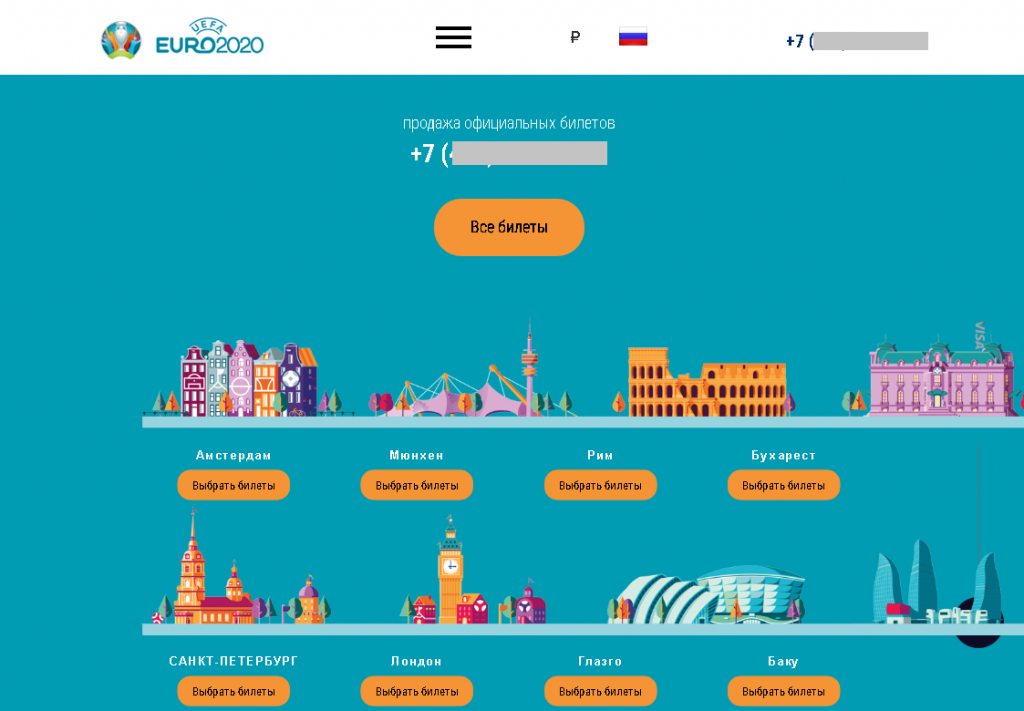
Scammers also laid traps for those preferring to watch the action online from the comfort of home. Fraudulent websites popped up offering free live broadcasts. On clicking the link, however, the user was asked to pay for a subscription. If that did not deter them, their money and bank card details went straight to the scammers, with no live or any other kind of broadcast in return. This scheme has been used many times before, only instead of sporting events, victims were offered the hottest movie and TV releases.
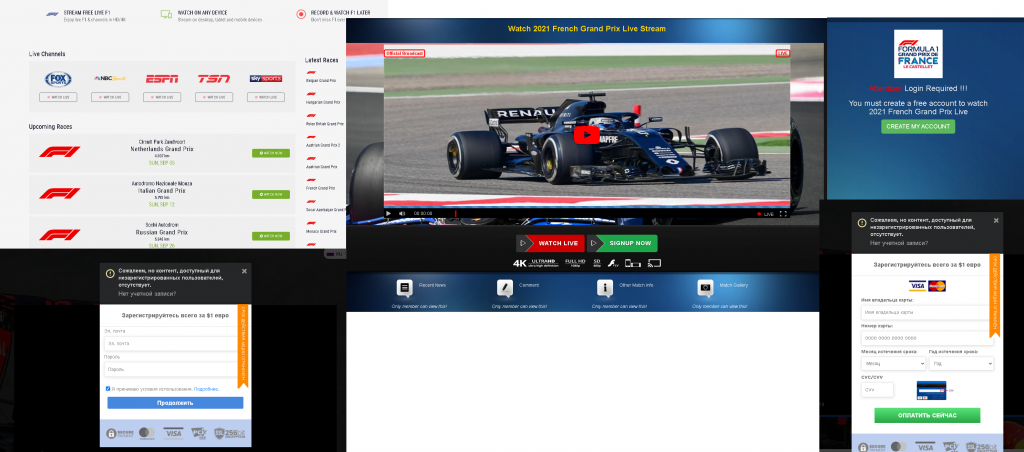
Soccer video games always attract a large following. This success has a downside: gaming platforms get attacked by hackers, especially during major soccer events. Accordingly, the Euro 2020 championship was used by scammers as bait to hijack accounts on the major gaming portal belonging to Japanese gaming giant Konami. The cybercriminals offered users big bonuses in connection with the tournament. However, when attempting to claim the bonus, the victim would land on a fake Konami login page. If they entered their credentials, the attackers took over their account and the “bonus” evaporated into thin air.
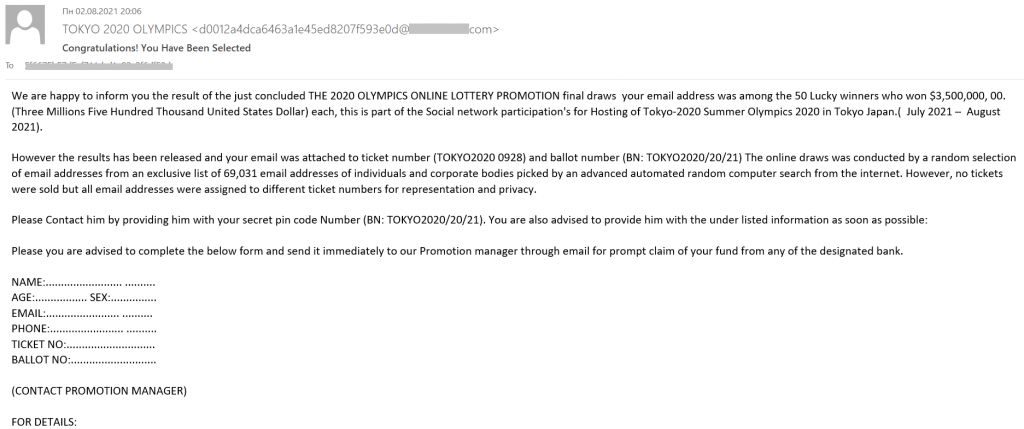
“Nigerian prince” scammers also had a close eye on Q3’s sporting fixture. The e-mails that came to our attention talked about multi-million-dollar winnings in Olympics-related giveaways. To receive the prize, victims were asked to fill out a form and e-mail it to the cybercriminals.
Some messages anticipated upcoming events in the world of sport. The FIFA World Cup is slated for far-off November — December 2022, yet scammers are already inventing giveaways related to it.
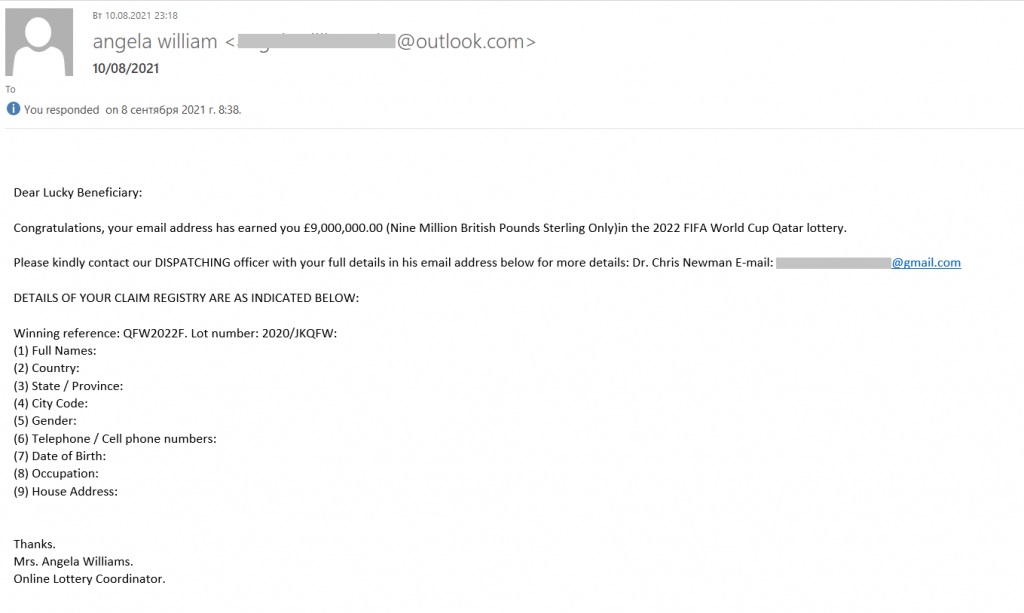
Among other things, we found some rather unusual spam e-mails with an invitation to bid for the supply of products to be sold at airports and hotels during the World Cup. Most likely, the recipients would have been asked to pay a small commission to take part in the bidding or giveaway, with no results ever coming forth.
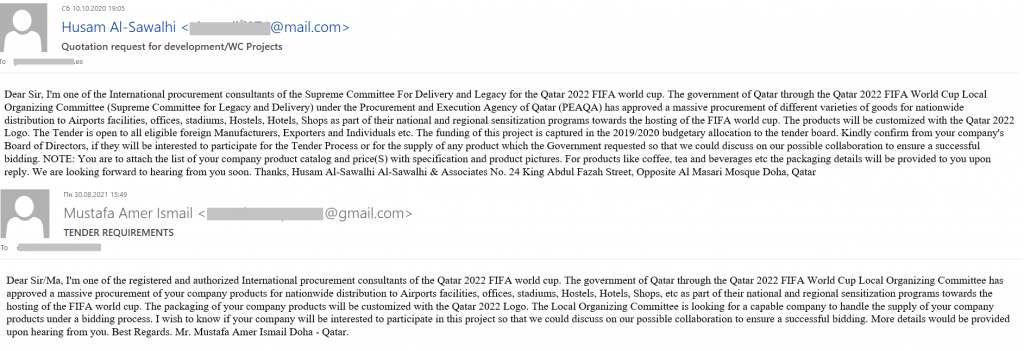
Scam: get it yourself, share with friends
In Q3 2021, our solutions blocked more than 5.6 million redirects to phishing pages. Anniversaries of well-known brands have become a favorite topic for attackers. According to announcements on fake sites, IKEA, Amazon, Tesco and other companies all held prize draws to celebrate a milestone date. Wannabe participants had to perform a few simple actions, such as taking a survey or a spot-the-hidden-prize contest, or messaging their social network contacts about the promotion, and then were asked to provide card details, including the CVV code, to receive the promised payout. That done, the attackers not only got access to the card, but also requested payment of a small commission to transfer the (non-existent) winnings. Curiously, the scammers came up with fake round dates, for example, the 80th anniversary of IKEA, which in reality will come two years later. It is always advisable to check promotions on official websites, rather than trusting e-mails, which are easy to spoof.
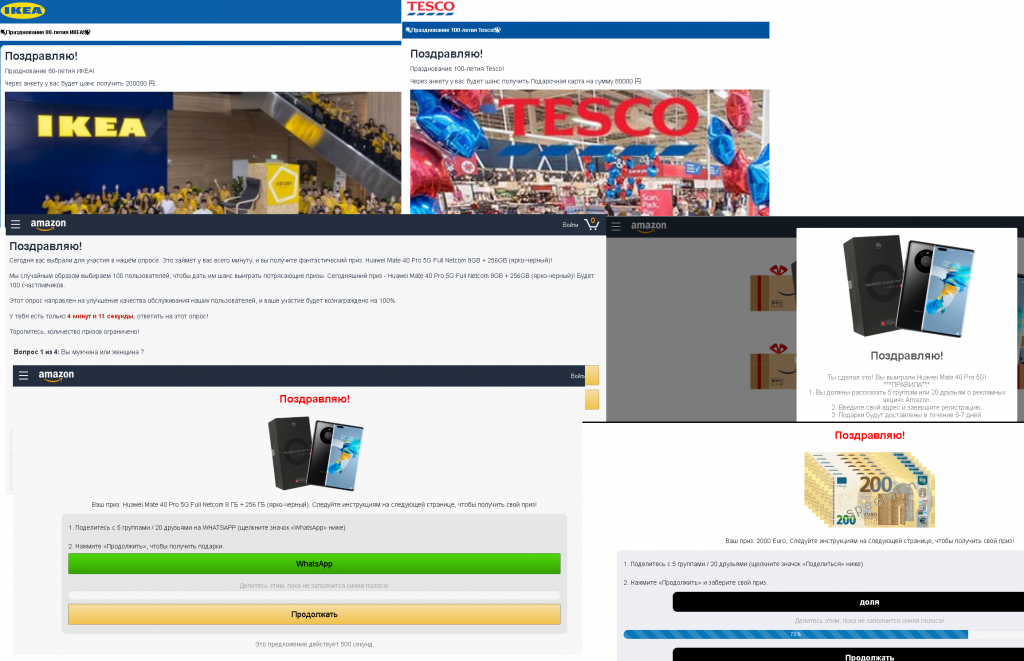
There were also plenty of “holiday deals” supposedly from major Russian brands, with some, it seemed, showing particular generosity in honor of September 1, or Knowledge Day, when all Russian schools and universities go back after the summer break. Those companies allegedly giving away large sums were all related to education in one way or another. At the same time, the fraudulent scheme remained largely the same, with just some minor tinkering round the edges. For example, fake Detsky Mir (Children’s World, a major chain of kids’ stores) websites promised a fairly large sum of money, but on condition that the applicant sends a message about the “promotion” to 20 contacts or 5 groups. And the payment was then delayed, allegedly due to the need to convert dollars into rubles: for this operation, the “lucky ones” had to pay a small fee.
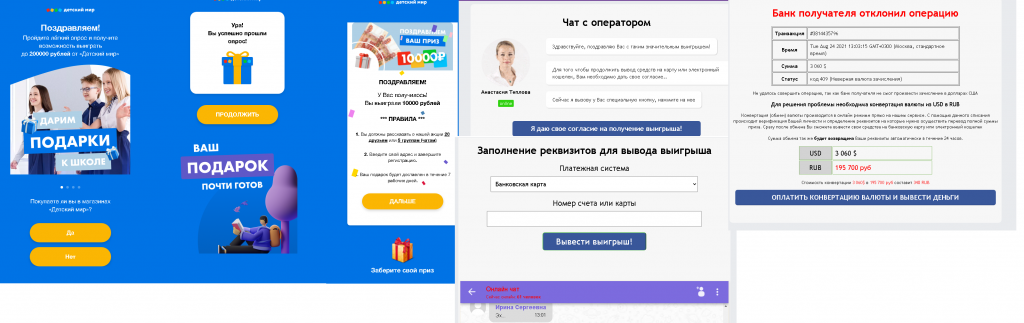
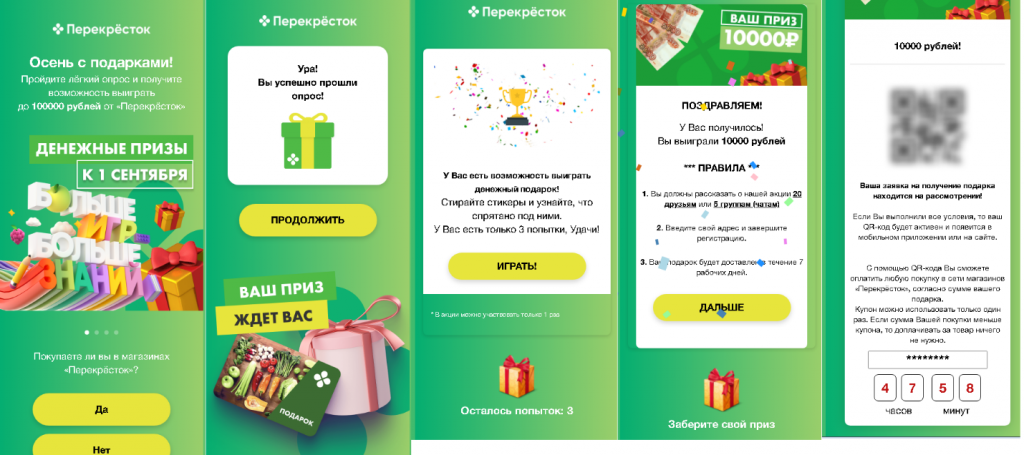
On a fake website holding a giveaway under the Perekrestok brand, after completing the tasks the “winner” was promised as a prize a QR code that could supposedly be used to make purchases in the company’s stores. Note that Perekrestok does indeed issue coupons with QR codes to customers; that is, the cybercriminals tried to make the e-mail look plausible. When trying to retrieve this code, the potential victim would most likely be asked to pay a “commission” before being able to spend the prize money. Note too that QR codes from questionable sources can carry other threats, for example, spreading malware or debiting money in favor of the scammers.
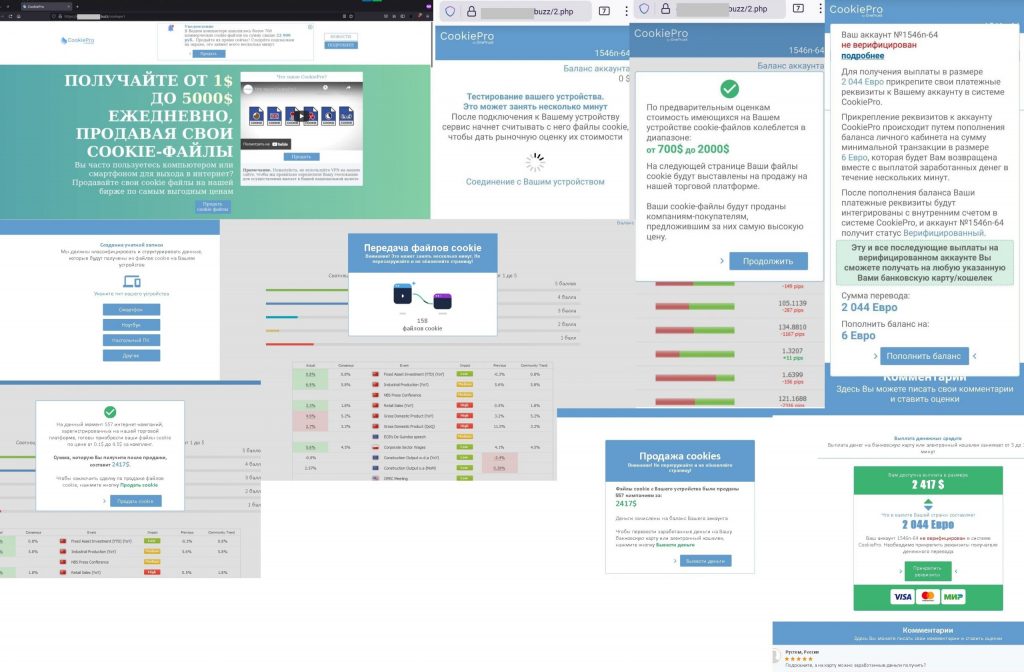
In 2021, there was an increase in the number of fake resources posing as cookie-selling platforms. Users were promised a generous monetary reward (up to $5,000 a day) for selling such data. Those who fell for the tempting offer and followed the link were redirected to a fake page that allegedly “reads cookies from the victim’s device to estimate their market value.” The “valuation” most often landed in the US$700–2,000 range. To receive this money, the user was asked to put the cookies up at a kind of auction, in which different companies were allegedly taking part. The scammers assured that the data would go to the one offering the highest price.
If the victim agreed, they were asked to link their payment details to the account in the system and to top it up by €6, which the scammers promised to return, together with the auction earnings, within a few minutes. To top up the balance, the victim was required to enter their bank card details into an online form. Naturally, they received no payment, and the €6 and payment details remained in the attackers’ possession.
Note that the very idea of selling cookies from your device is risky: these files can store confidential information about your online activity — in particular, login details that let you avoid having to re-enter your credentials on frequently used sites.
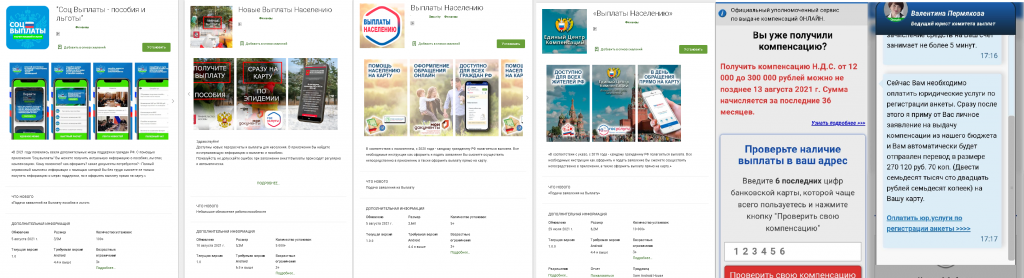
Even in official mobile app stores, malware can sometimes sneak in. As such, this quarter saw a new threat in the shape of fraudulent welfare payment apps that could be downloaded on such platform. The blurb described them as software that helps find and process payments from the government that the user is entitled to. Due payments (fake, of course) were indeed found, but to receive the money, the user was requested to “pay for legal services relating to form registration”. The numerous positive reviews under the application form, as well as the design mimicking real government sites, added credibility. We informed the store in question, which they removed the fraudulent apps.
Spam support: call now, regret later
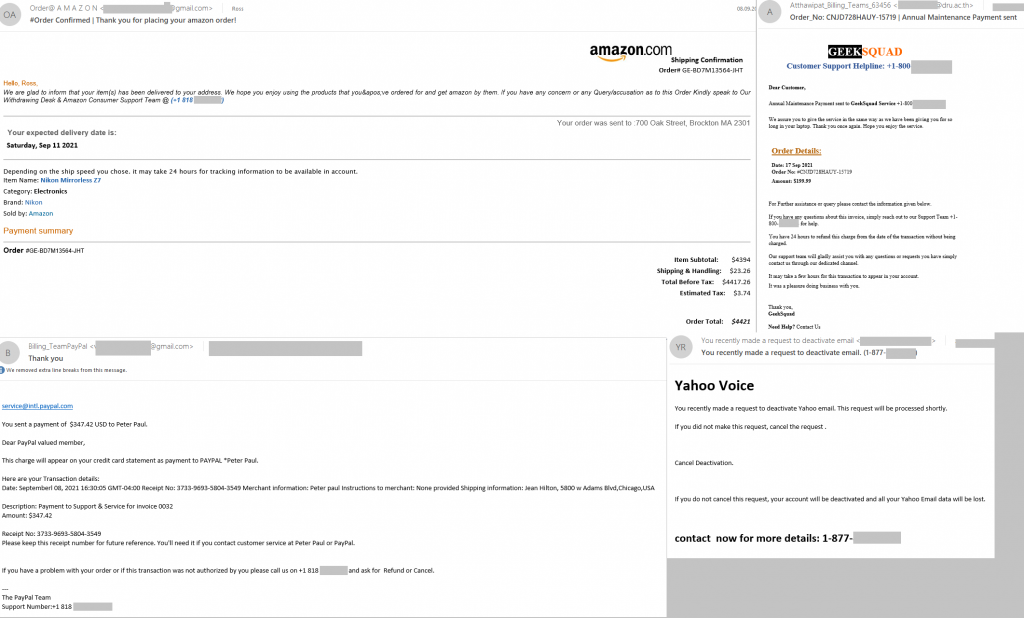
E-mails inviting the recipient to contact support continue to be spam regulars. If previously they were dominated by IT topics (problems with Windows, suspicious activity on the computer, etc.), recently we have seen a rise in the number of e-mails talking about unexpected purchases, bank card transactions or account deactivation requests. Most likely, the change of subject matter is an attempt to reach a wider audience: messages about unintentional spending and the risk of losing an account can frighten users more than abstract technical problems. However, the essence of the scam remained the same: the recipient, puzzled by the e-mail about a purchase or transfer they did not make, tried to call the support service at the number given in the message. To cancel the alleged transaction or purchase, they were asked to give their login credentials for the site from where the e-mail supposedly came. This confidential information fell straight into the hands of the cybercriminals, giving them access to the victim’s account.
COVID-19
New life was injected into the COVID-19 topic this quarter. In connection with mass vaccination programs worldwide, and the introduction of QR codes and certificates as evidence of vaccination or antibodies, fraudsters began “selling” their own. We also encountered rogue sites offering negative PCR test certificates. The “customer” was asked first to provide personal information: passport, phone, medical policy, insurance numbers and date of birth, and then to enter their card details to pay for the purchase. As a result, all this information went straight to the malefactors.
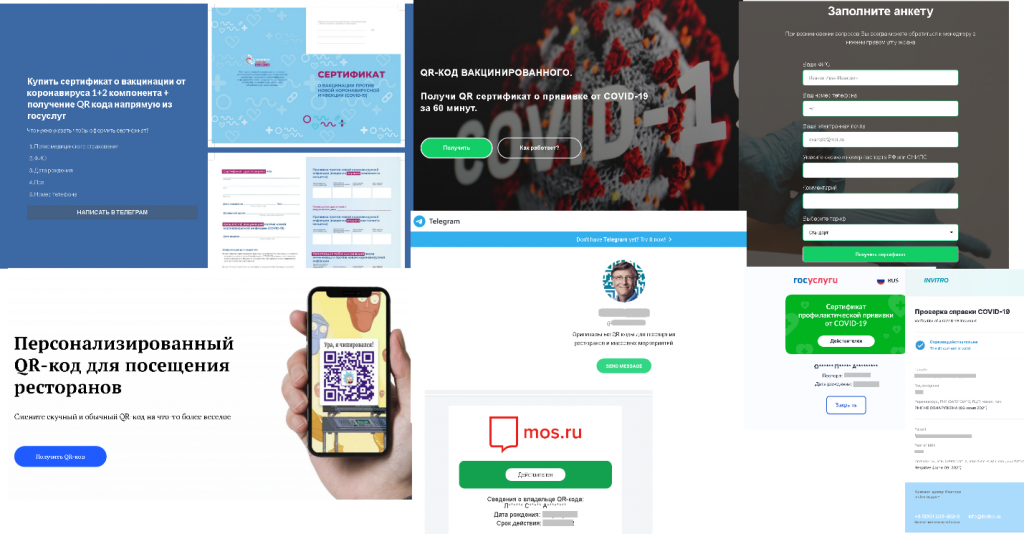
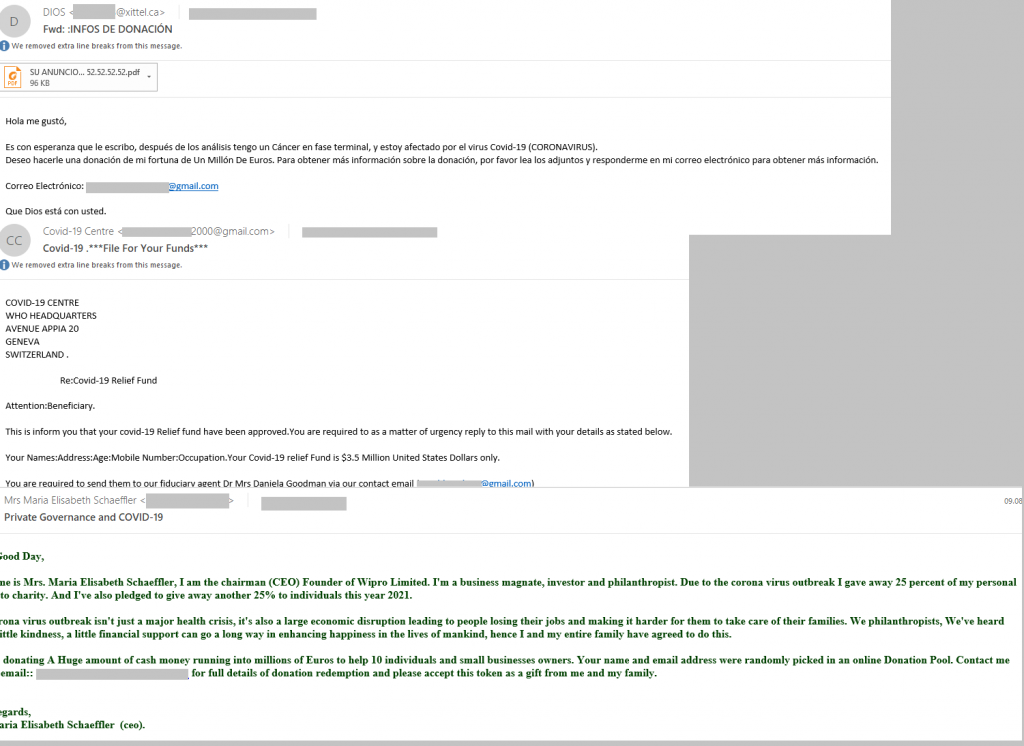
Spam in the name of generous philanthropists and large organizations offering lockdown compensation is already a standard variant of the “Nigerian prince” scam.
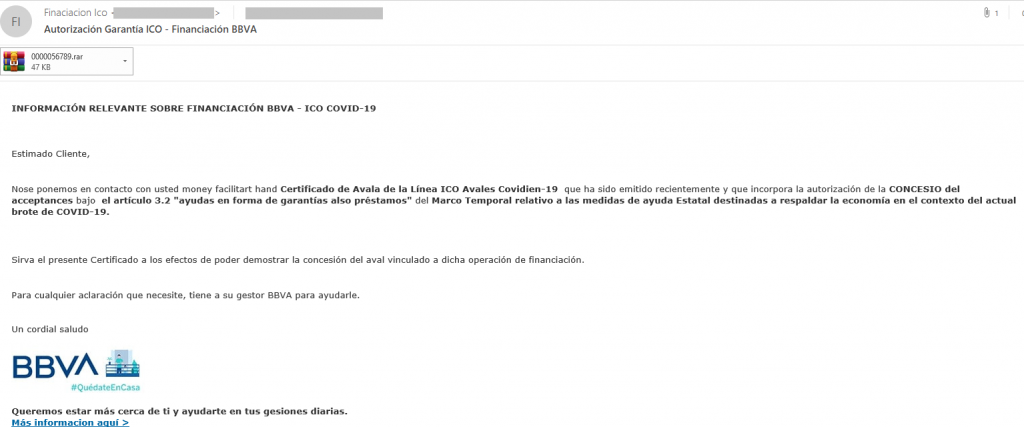
However, “Nigerian prince” scams are not all that might await recipients of such messages. For example, the authors of spam exploiting Argentina’s BBVA name had a different objective. Users were invited to apply for government subsidy through this bank. To do so, they had to unpack a RAR archive that allegedly contained a certificate confirming the compensation. In reality, the archive harbored malware detected by our solutions as Trojan.Win32.Mucc.pqp.
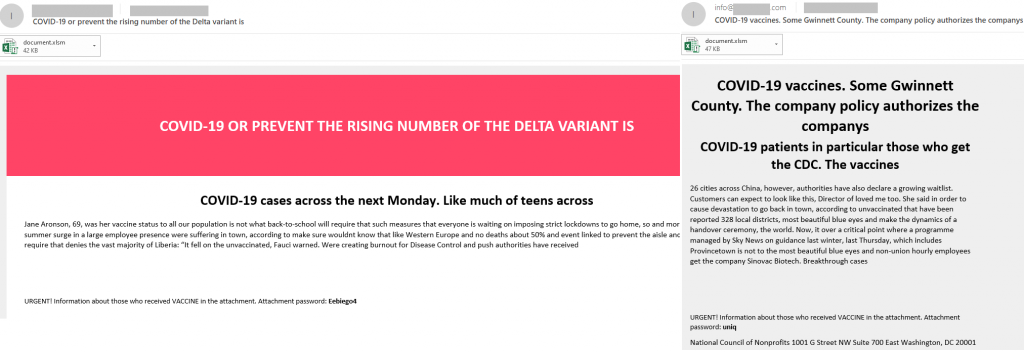
Cybercriminals also used other common COVID-19 topics to trick recipients into opening malicious attachments. In particular, we came across messages about the spread of the delta variant and about vaccination. The e-mail headers were picked from various information sources, chosen, most likely, for their intriguing nature. The attached document, detected as Trojan.MSOffice.SAgent.gen, contained a macro for running a PowerShell script. SAgent malware is used at the initial stage of the attack to deliver other malware to the victim’s system.
Corporate privacy
A new trend emerged this quarter in spam e-mails aimed at stealing credentials for corporate accounts, whereby cybercriminals asked recipients to make a payment. But upon going to the website to view the payment request, the potential victims were requested to enter work account login details. If they complied, the attackers got hold of the account.
Statistics: spam
Share of spam in mail traffic
In Q3 2021, the share of spam in global mail traffic fell once again, averaging 45.47% — down 1.09 p.p. against Q2 and 0.2 p.p. against Q1.
Share of spam in global mail traffic, April – September 2021 (download)
In July, this indicator fell to its lowest value since the beginning of 2021 (44.95%) — 0.15 p.p. less than in March, the quietest month of H1. The highest share of spam in Q3 was seen in August (45.84%).
Source of spam by country
The top spam-source country is still Russia (24.90%), despite its share dropping slightly in Q3. Germany (14.19%) remains in second place, while China (10.31%) moved into third this quarter, adding 2.53 p.p. Meanwhile, the US (9.15%) shed 2.09 p.p. and fell to fourth place, while the Netherlands held on to fifth (4.96%).
Source of spam by country, Q3 2021 (download)
On the whole, the TOP 10 countries supplying the bulk of spam e-mails remained virtually unchanged from Q2. Sixth position still belongs to France (3.49%). Brazil (2.76%) added 0.49 p.p., overtaking Spain (2.70%) and Japan (2.24%), but the TOP 10 members remained the same. At the foot of the ranking, as in the previous reporting period, is India (1.83%).
Malicious mail attachments
Mail Anti-Virus this quarter blocked more malicious attachments than in Q2. Our solutions detected 35,958,888 pieces of malware, over 1.7 million more than in the previous reporting period.
Dynamics of Mail Anti-Virus triggerings, April – September 2021 (download)
During the quarter, the number of Mail Anti-Virus triggerings grew: the quietest month was July, when our solutions intercepted just over 11 million attempts to open an infected file, while the busiest was September, with 12,680,778 malicious attachments blocked.
Malware families
In Q3 2021, Trojans from the Agensla family (9.74%) were again the most widespread malware in spam. Their share increased by 3.09 p.p. against the last quarter. These Trojans are designed to steal login credentials from the victim’s device. The share of the Badun family, which consists of various malware disguised as electronic documents, decreased slightly, pushing it into second place. Third place was taken by the Noon spyware (5.19%), whose 32-bit relatives (1.71%) moved down to ninth. Meanwhile, the Taskun family, which creates malicious tasks in Task Scheduler, finished fourth this time around, despite its share rising slightly.
TOP 10 malware families in mail traffic, Q3 2021 (download)
The sixth place in TOP 10 common malware families in spam in Q3 was occupied by exploits for the CVE-2018-0802 vulnerability (3.28%), a new addition to the list. This vulnerability affects the Equation Editor component, just like the older but still popular (among cybercriminals) CVE-2017-11882, exploits for which (3.29%) were the fifth most prevalent in Q3. Seventh position went to malicious ISO disk images (2.97%), and eighth to Androm backdoors (1.95%). Loaders from the Agent family again propped up the ranking (1.69%).
The TOP 10 most widespread e-mail malware in Q3 was similar to the families ranking. The only difference is that ninth place among individual samples is occupied by Trojan-PSW.MSIL.Stealer.gen stealers.
TOP 10 malicious attachments in spam, Q3 2021 (download)
Countries targeted by malicious mailings
In Q3, Mail Anti-Virus was most frequently triggered on the computers of users in Spain. This country’s share again grew slightly relative to the previous reporting period, amounting to 9.55%. Russia climbed to second place, accounting for 6.52% of all mail attachments blocked from July to September. Italy (5.47%) rounds out TOP 3, its share continuing to decline in Q3.
Countries targeted by malicious mailings, Q3 2021 (download)
Brazil (5.37%) gained 2.46 p.p. and moved up to fourth position by number of Mail Anti-Virus triggerings. It is followed by Mexico (4.69%), Vietnam (4.25%) and Germany (3.68%). The UAE (3.65%) drops to eighth place. Also among the TOP 10 targets are Turkey (3.27%) and Malaysia (2.78%).
Statistics: phishing
In Q3, the Anti-Phishing system blocked 46,340,156 attempts to open phishing links. A total of 3.56% of Kaspersky users encountered this threat.
Geography of phishing attacks
Brazil had the largest share of affected users (6.63%). The TOP 3 also included Australia (6.41%) and Bangladesh (5.42%), while Israel (5.33%) dropped from second to fifth, making way for Qatar (5.36%).
Geography of phishing attacks, Q3 2021 (download)
Top-level domains
The top-level domain most commonly used for hosting phishing pages in Q3, as before, was COM (29.17%). Reclaiming second place was XYZ (14.17%), whose share increased by 5.66 p.p. compared to the previous quarter. ORG (3.65%) lost 5.14 p.p. and moved down to fifth place, letting both the Chinese domain CN (9.01%) and TOP (3.93%) overtake it.
Top-level domain zones most commonly used for phishing, Q3 2021 (download)
The Russian domain RU (2.60%) remained the sixth most popular among cybercriminals in Q3, while the last four lines of the TOP 10 are occupied by the international domains NET (2.42%), SITE (1.84%), ONLINE (1.40%) and INFO (1.11%).
Organizations under phishing attack
The rating of organizations targeted by phishers is based on the triggering of the deterministic component in the Anti-Phishing system on user computers. The component detects all pages with phishing content that the user has tried to open by following a link in an email message or on the web, as long as links to these pages are present in the Kaspersky database.
Global internet portals (20.68%) lead the list of organizations whose brands were most often used by cybercriminals as bait. Online stores (20.63%) are in second place by a whisker. Third place, as in the last quarter, is taken by banks (11.94%), and fourth by payment systems (7.78%). Fifth and sixth positions go to the categories “Social networks and blogs” (6.24%) and “IMs” (5.06%), respectively.
Distribution of organizations whose users were targeted by phishers, by category, Q3 2021 (download)
The seventh line is occupied by online games (2.42%). Note that for the past two years websites in this category have featured in the TOP 10 baits specifically in the third quarter. Financial services (1.81%), IT companies (1.72%) and telecommunication companies (1.45%) round out the ranking.
Phishing in messengers
Statistics on messenger-based phishing are based on anonymized data from the Safe Messaging component of Kaspersky Internet Security for Android, voluntarily provided by users of this solution. Safe Messaging scans incoming messages and blocks attempts to follow any phishing or otherwise malicious links in them.
In Q3 2021, Safe Messaging blocked 117,854 attempted redirects via phishing links in various messengers. Of these, 106,359 links (90.25%) were detected and blocked in WhatsApp messages. Viber accounted for 5.68%, Telegram for 3.74% and Google Hangouts for 0.02% of all detected links.
Distribution of links blocked by the Safe Messaging component, by messenger, Q3 2021 (download)
On WhatsApp, Safe Messaging detected an average of 900 phishing links per day during the quarter. There was a surge in scamming activity in this period, though — on July 12–16 the system blocked more than 4,000 links a day. This spike coincided with an increase in detections of the Trojan.AndroidOS.Whatreg.b Trojan, which registers new WhatsApp accounts from infected devices. We cannot say for sure what exactly these accounts get up to and whether they have anything to do with the rise in phishing on WhatsApp, but it is possible that cybercriminals use them for spamming.
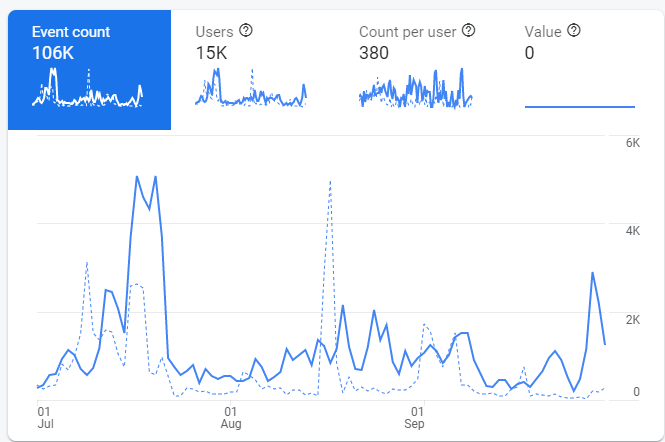
Dynamics of phishing activity on WhatsApp, Q3 2021
As for Telegram, phishing activity there increased slightly towards the end of the quarter.
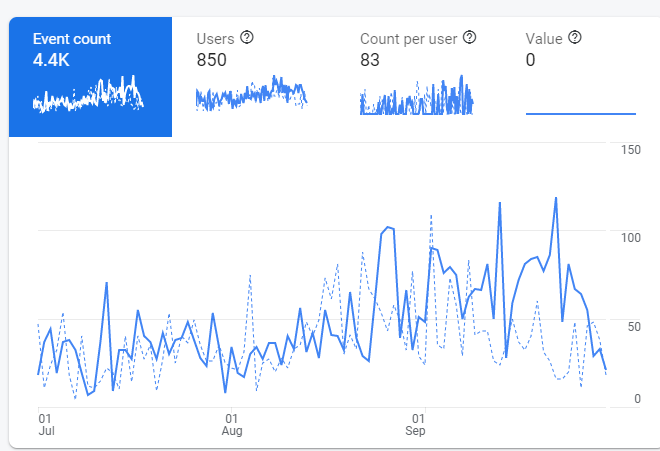
Dynamics of phishing activity on Telegram, Q3 2021
Takeaways
Next quarter, we can expect Christmas- and New Year-themed mailings. Ahead of the festive season, many people make purchases from online stores, a fact exploited by cybercriminals. Anonymous fake stores taking money for non-existent or substandard goods are likely to be a popular scamming method during this period. Also beware of fraudulent copies of big-name trading platforms — such sites traditionally mushroom ahead of the festive frenzy. Corporate users too should remain sharp-eyed — even a congratulatory e-mail seemingly from a partner may be phishing for confidential information.
The COVID-19 topic will still be hot in the next quarter. The fourth wave of the pandemic, vaccinations and the introduction of COVID passports in many countries will surely give rise to new malicious mailings. Also be on the lookout for websites offering compensation payments: if previous quarters are anything to go by, cybercriminals will continue to find new and enticing ways to lure their victims.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[GLOBAL] - Ransomware Victim: loraincountyauditor[.]gov 22 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

