SpyLoan Android malware on Google Play downloaded 12 million times

More than a dozen malicious loan apps, which are generically named SpyLoan, have been downloaded more than 12 million times this year from Google Play but the count is much larger since they are also available on third-party stores and suspicious websites.
SpyLoan Android threats steal from the device personal data that includes a list of all accounts, device info, call logs, installed apps, calendar events, local Wi-Fi network details, and metadata from images. Researchers say that the risk also extends to contacts list, location data, and text messages.
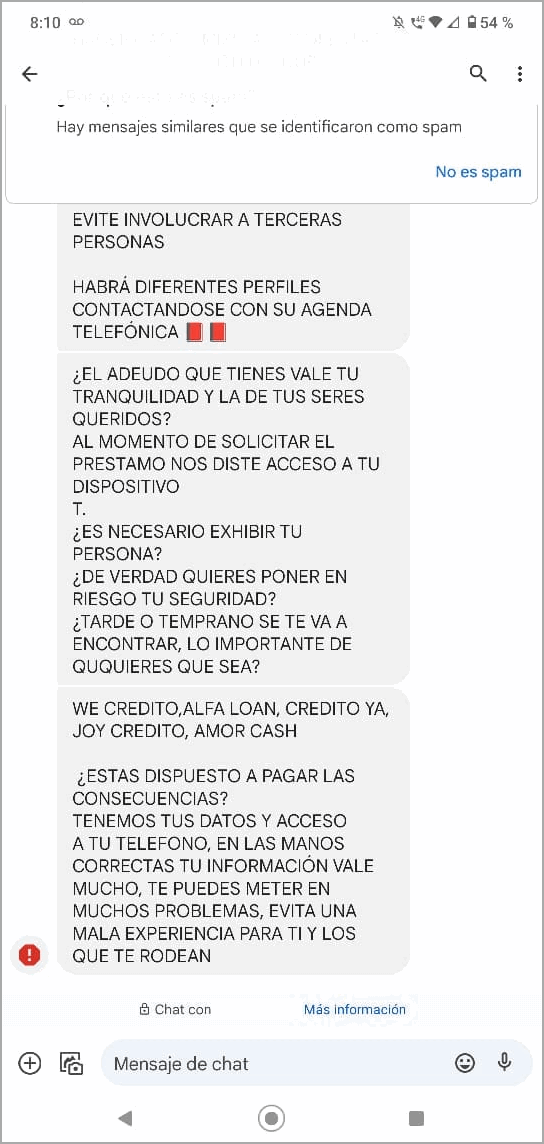
They pose as legitimate financial services for personal loans that promise “quick and easy access to funds.” However, they trick users into accepting high-interest payments and then the threat actor blackmails victims into paying the money.
Since the start of the year, cybersecurity company ESET, a member of the App Defense Alliance dedicated to detecting and eradicating malware from Google Play, has discovered 18 SpyLoan apps.
Google reacted to ESET’s reporting and removed 17 of the malicious apps, while one of them is now available with a different set of permissions and functionality and is no longer detected as a SpyLoan threat.

Rise of SpyLoan
SpyLoan apps were first seen in 2020 but starting last year they became more prevalent on both Android and iOS systems, according to ESET, Lookout, Zimperium, and Kaspersky.
ESET says the current distribution channels include fraudulent websites, software on third-party app stores, and Google Play.
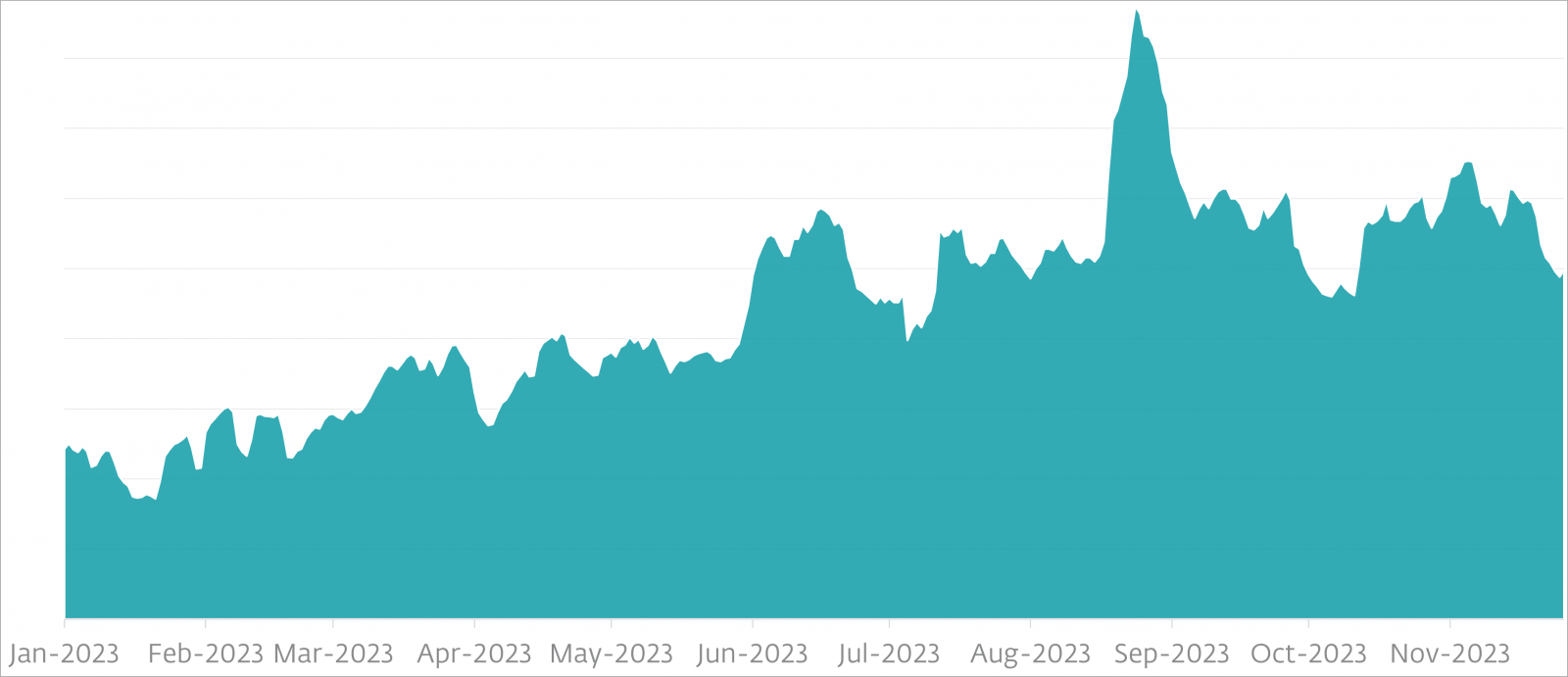
Based on data from ESET, SpyLoan detection has increased throughout 2023, the threat being more prominent in Mexico, India, Thailand, Indonesia, Nigeria, Philippines, Egypt, Vietnam, Singapore, Kenya, Colombia, and Peru.
To infiltrate Google Play, these apps are submitted with compliant privacy policies, follow the required know your customer (KYC) standards, and have transparent permission requests.
In many cases, the fraudulent apps link to websites that are blatant ripoffs of legitimate company sites, even showing employee and office photos to create a false sense of authenticity.
Multi-faceted risks
SpyLoan apps violate Google’s Financial Services policy by unilaterally shortening the tenure for personal loans to a few days or any other arbitrary period and threatening the user with ridicule and exposure if they don’t comply.
Additionally, what is mentioned in the privacy policies is deceptive, presenting seemingly legitimate reasons to obtain risky permissions.
For example, the camera permission is supposedly needed to allow photo data uploads for KYC and access to the user’s calendar to schedule payment dates and reminders, but those are extremely intrusive practices.
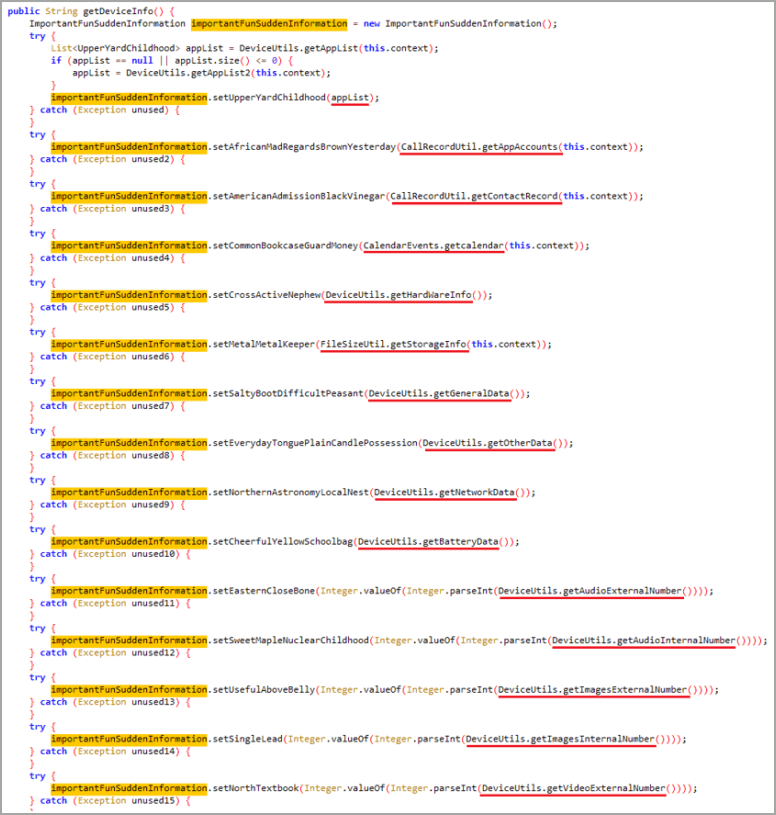
Moreover, SpyLoan apps request permissions that shouldn’t be needed at all, like access to call logs and contact lists, which they use for extorting users when they resist absurd payment demands.
(ESET)
“While these SpyLoan apps technically comply with the requirements of having a privacy policy, their practices clearly go beyond the scope of data collection necessary for providing financial services and complying with the KYC banking standards,” ESET explains.
“We believe the real purpose of these permissions is to spy on the users of these apps and harass and blackmail them and their contacts,” the researchers add.
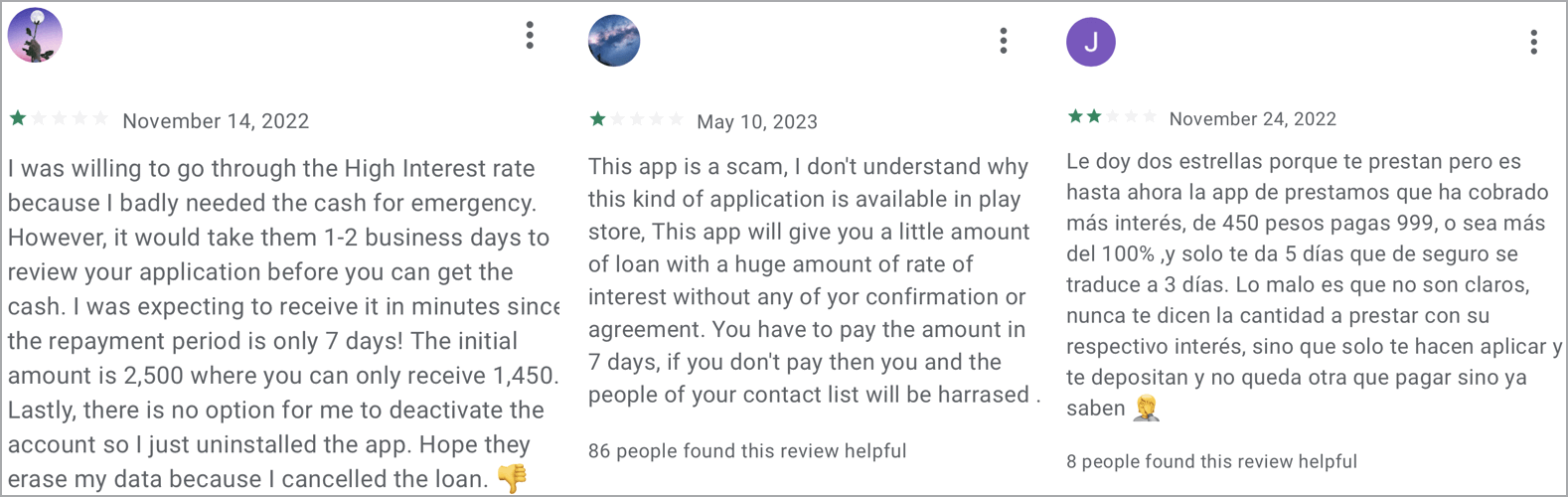
To defend against the SpyLoan threat, only trust established financial institutions, carefully review the requested permissions upon installing a new app, and read user reviews on Google Play, which often contain clues about the fraudulent nature of the app.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[FLOCKER] - Ransomware Victim: G*********************y[.]org 7 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

