Stolen Nvidia certificates used to sign malware—here’s what to do
As we wrote on March 3, 2022 Nvidia, was recently attacked by the LAPSUS$ ransomware group. The ensuing data leak included two of NVIDIA’s code signing certificates. Those certificates are now being used to sign malware.
Leaked signing certificates from major vendors like Nvidia come with huge security implications. And the fact that the certificates have expired does not lessen the burden much.
A code signing certificate is used to authenticate the identity of a software developer or publisher, and it provides cryptographic assurance that a signed piece of software has not been altered or tampered with. Signing certificates are considered trustworthy because they are cryptographically signed by a Certificate Authority (CA). This creates a “chain of trust” between a signature on a piece of software and a CA—like DigiCert or Let’s Encrypt—that operating systems trust.
Code signing is used by Windows and macOS to ensure that users only run software from trusted sources. This is a powerful security feature, provided that code signing certificates are kept out of the hands of cybercriminals.
Leaked Nvidia certificates
The data the LAPSUS$ group stole from Nvidia contained two code signing certificates. As is often the case in ransomware attacks, the exfiltrated data was published on a leak site. From there, any cybercriminal that wanted to could grab the certificates and use them to sign their malware.
The two leaked Nvidia certificates have expired, being valid from 2011 to 2014 and 2015 to 2018. But, Windows will accept expired certificates for drivers, which makes the leaked certificates very useful to cybercriminals.
So useful, in fact, that the first malware samples signed with these certificates started to show up only one day after they were leaked.
Expired certificates
A compromised certificate can only be revoked by its CA. CAs maintain Certificate Revocation Lists (CRLs) which—as the name implies—list certificates that have been revoked. But certificates only get revoked if they are compromised before their expiration date.
Unless a system knows that a certificate has been revoked or suspended, the system will continue to trust that certificate.
Microsoft has always made an exception for signed drivers, so that drivers don’t brick a system just because the certificate that signed them has expired. To prevent these drivers from getting loaded, it requires that the certificates are added to the CRL. Then your system needs to be made aware of the revocation. Which basically means they get added to the “Untrusted Certificates” after a Windows update. Microsoft may be reluctant to do this because doing so could block legitimate Nvidia drivers.
But until then, malware can get loaded as a driver that’s been signed with these leaked certificates.
Mitigation
There are some additional protection mechanisms that can protect you from malicious signed drivers.
- Normally, users running a system protected by Secure Boot would be protected because Secure Boot does not allow certificates without a time-stamp. Unfortunately an exception was made for certificates that were created before July 29, 2015. And both of the leaked certificates were created before that date. One of them just barely (by two days).
- The signing certificates do not stop anti-malware solutions from recognizing the malware.
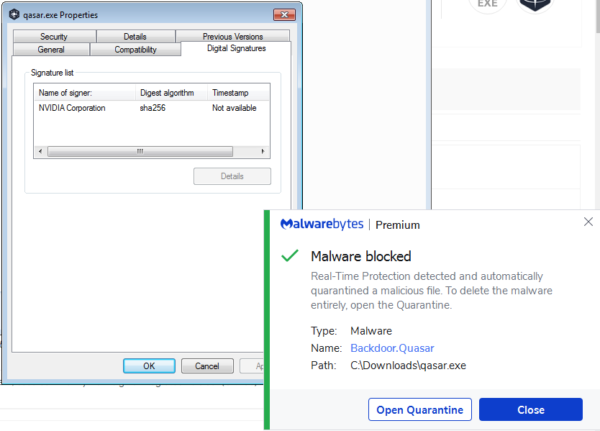
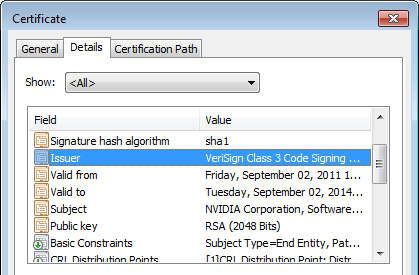
Should you decide to update your Nvidia drivers, make sure to get them from the Nvidia download site and check the installer before you run it, to see that the driver’s certificate is still valid and not expired or revoked. To check, right click and select Properties, look at the Digital Signatures tab and select the Nvidia signature > click on the Details button > on the General tab click on View Certificate > then look at the Details tab for the Valid to date.
For system administrators, David Weston, Vice President of OS Security and Enterprise at Microsoft, has tweeted some guidance on how you can configure Windows Defender Application Control policies to control which Nvidia drivers can be loaded.
If you want to check if any of the leaked certificates are on your systems, the serial numbers of the leaked certificates are:
43BB437D609866286DD839E1D00309F5 14781bc862e8dc503a559346f5dcc518
There is also a Yara rule to be found on GitHub that can be used by security teams to search for files signed with these certificates in their environments.
Stay safe, everyone!
The post Stolen Nvidia certificates used to sign malware—here’s what to do appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



