Malware Analysis – evasion – 912e4121a6c9471070938340eec18263
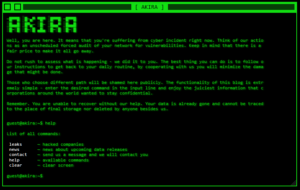
Score: 9 MALWARE FAMILY: evasionTAGS:evasion, ransomwareMD5: 912e4121a6c9471070938340eec18263SHA1: beb717e36becb891c99df74ee82f548f4914c063ANALYSIS DATE: 2023-06-30T15:57:49ZTTPS: ScoreMeaningExample10Known badA malware family was detected.8-9Likely maliciousOne or more known...







![LockBit 3.0 Ransomware Victim: tsmc[.]com 17 image-11](https://www.redpacketsecurity.com/wp-content/uploads/2022/06/image-11-300x142.png)
![Cobalt Stike Beacon Detected - 42[.]192[.]16[.]196:9998 19 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
