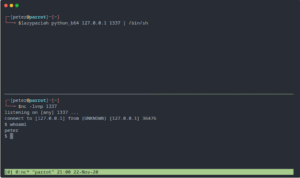
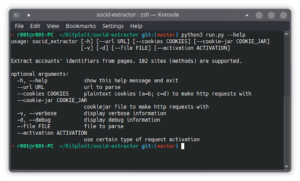
CVE-2022-22963 – PoC Spring Java Framework 0-day Remote Code Execution Vulnerability
To run the Credits https://github.com/hktalent/spring-spel-0day-poc Download CVE-2022-22963 If you like the site, please consider joining the telegram channel or supporting...











![[PLAY] - Ransomware Victim: Fast Freight 27 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
