Reconmap – VAPT (Vulnerability Assessment And Penetration Testing) Automation And Reporting Platform
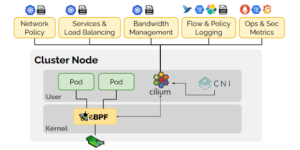
Reconmap is a vulnerability assessment and penetration testing (VAPT) platform. It helps software engineers and infosec pros collaborate on security...





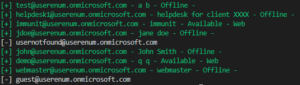


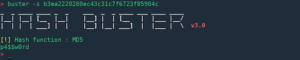


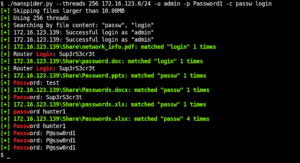
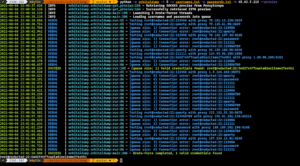





![[QILIN] - Ransomware Victim: bagnoles[.]nl 25 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
![Cobalt Strike Beacon Detected - 196[.]251[.]69[.]253:4433 28 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)
