Tampa Bay Times hit with Ryuk ransomware attack
Florida newspaper The
Tampa Bay Times suffered a Ryuk ransomware attack Thursday, making it the
latest major victim of the notorious ransomware family that continues to rise
in popularity.
Curiously, the paper is at least the third Florida-based Ryuk
victim in the past year.
The attack, which The Tampa Bay Times reported on itself, did not result in any breached data. Sensitive customer information, such as subscriber addresses and credit card details, was not disclosed in the breach, the newspaper said.
The Tampa Bay Times
chief digital officer Conan Gallaty said the paper had “a lot of plans for
systems that go down,” and that its priority was in restoring and securing
operations.
“The focus for us is to fully recover and then work on
further preventative measures,” Gallaty said.
The newspaper did not respond to the threat actors, and
Gallaty said the paper would have refused any ransom payment demanded. This
stalwart opposition is becoming less common today, as increasingly companies
are forced to choose between the loss of several hundred thousand dollars in
ransom payments, or several hundred thousand dollars in database and operations
recovery.
Further, when some companies hire the help of outside malware recovery firms, they may be signing up, quietly, for ransomware negotiations. A ProPublica investigation last year found that at least two cybersecurity firms that touted allegedly advanced technology solutions would, in fact, pay off the ransoms demanded by the threat actors who breached their clients.
The investigation of two firms found that:
“The [cybersecurity] firms are alike in other ways. Both
charge victims substantial fees on top of the ransom amounts. They also offer
other services, such as sealing breaches to protect against future attacks.
Both firms have used aliases for their workers, rather than real names, in
communicating with victims.”
Though The Tampa Bay Times did not disclose the Ryuk ransomware attack vector, Gallaty said he believed the paper was unlikely to be a specific target for the threat actors. That’s hard to reconcile with Ryuk’s history—already it has been responsible for crippling the delivery operations for at least four major US newspapers, including The Chicago Tribune and The Los Angeles Times.
In speaking with The
Tampa Bay Times, Malwarebytes senior security researcher JP Taggart
explained the calculus behind potential Ryuk ransomware targets:
“They’re looking at the people that have the most to lose.”
That bears true when looking at recent Ryuk victims.
In June 2019, the government of Lake City, Florida, crawled to a halt, with phones and computer systems stalled after threat actors successfully implanted a Ryuk variant into the city’s network. Unable to work themselves out of the problem, even with the help of the FBI, the city had to make a choice. It chose to pay $460,000. A similar situation happened months later, in October, when the Alabama-based DCH Health System was forced to partially shut down three of its hospitals after a Ryuk attack. Again, unable to solve the problem, and unable to continue to turn away all but the most critical patients, the hospital operator decided to prioritize patient care, paying an undisclosed amount to the threat actors.
Those payments add up. According to CrowdStrike, Ryuk’s deployment teams have amassed more than $3.7 million in paid ransoms.
When Ryuk’s threat actors haven’t successfully scored a big pay day, though, they’ve still managed to do enormous damage. In April 2019, Imperial County, California, refused to pay an enormous $1.3 million ransom from a Ryuk attack, but, according to The Wall Street Journal, the city has spent $1.6 million in recovery efforts. In late December, the US Coast Guard publicly announced that it suffered a Ryuk attack that shut down a maritime facility for 30 hours.
The ransomware campaigns became so common that the FBI warned the public that threat actors had used Ryuk to target more than 100 US and international businesses since its emergence in August 2018.
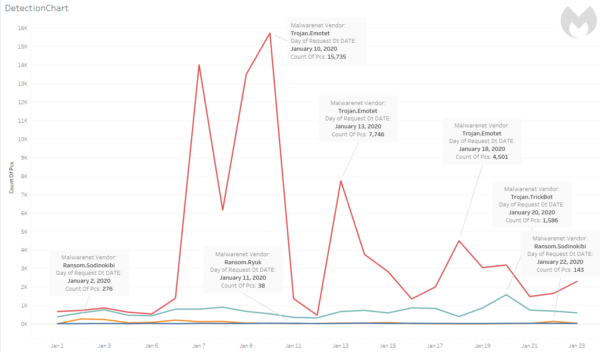
According to new Malwarebytes data, those attacks have
continued. From January 1–23, 2020, Malwarebytes recorded a cumulative 724 Ryuk
detections. The daily detections fluctuated, with the lowest detection count at
18 on January 6, and the highest detection count at 47 on January 14.

The ransomware frequently works in conjunction with Emotet
and TrickBot in multi-stage attacks. Those separate malware families have also
been active in the new year, with small spikes into the thousands of
detections. Emotet, particularly, kicked
itself into high gear again starting on January 13.
As we explained before in our threat spotlight on Ryuk:
“The first stage of the attack starts with a weaponized
Microsoft Office document file—meaning, it contains malicious macro
code—attached to a phishing email.
Once the user opens it, the malicious macro will run cmd and execute a PowerShell command. This command
attempts to download Emotet.
Once Emotet executes, it retrieves and executes another
malicious payload—usually TrickBot—and collects information on affected systems. It
initiates the download and execution of TrickBot by reaching out to and
downloading from a pre-configured remote malicious host.
Once infected with TrickBot, the threat actors then check if the
system is part of a sector they are targeting. If so, they download an additional
payload and use the admin credentials stolen using TrickBot to perform lateral
movement to reach the assets they wish to infect.
The threat actors then check for and establish a connection with
the target’s live servers via a remote desktop protocol (RDP).
From there, they drop Ryuk.”
The Tampa Bay Times
did not specify which systems, or how many computers, were disrupted in
Thursday’s attack. Instead, the only hint of inconvenience in the newspaper’s routine
was the acknowledgement that Friday’s newspaper would be published with an
earlier deadline.
The show must go on.
The post Tampa Bay Times hit with Ryuk ransomware attack appeared first on Malwarebytes Labs.


