The Dreambot Malware Botnet Appears To Have Gone Silent and Possibly Shut Down

Dreambot’s backend servers as per a report published by the CSIS Security Group, a cyber-security firm situated in Copenhagen, seem to have gone quiet and potentially shut down completely.
It started in March around the same time when the cybersecurity community likewise stopped seeing the new Dreambot samples disseminated in the wild.
Benoit Ancel, the malware analyst at the CSIS Security Group, says, “The lack of new features? The multiplication of new Gozi variants? The huge rise of Zloader? COVID-19? We can’t be sure exactly what was the cause of death, but more and more indicators point at the end of Dreambot.”
The Dreambot malware’s apparent demise put an end to a six-year-old “career” on the cybercrime landscape. First spotted in 2014, it was created on the leaked source code of the more seasoned Gozi ISFB banking trojan, one of the most reused bits of malware today.
With time, Dreambot received new highlights, like the Tor-hosted command and control servers, a keylogging capacity, the capacity to steal browser cookies and information from email clients, a screenshot feature, the capacity to record a victim’s screen, a bootkit module, and a VNC remote access feature – just to name the most significant.
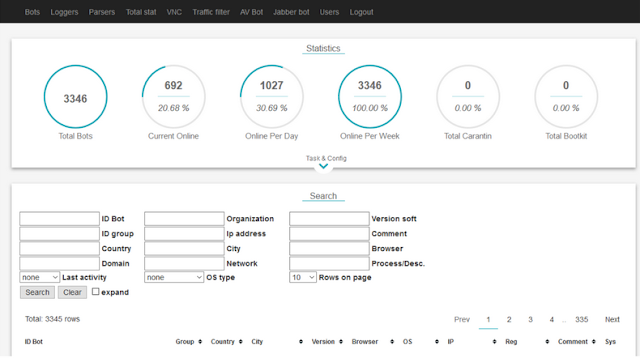 |
| Typical Dreambot Control Panel |
Besides, Dreambot likewise evolved from a private malware botnet into what’s known as a Cybercrime-as-a-Service (CaaS).
As a CaaS, the Dreambot creators would publicize access to their botnet on hacking and malware forums. Various crooks could gain access to a part of Dreambot’s infrastructure and an adaptation of the Dreambot malware, which they’d be answerable for distributing to victims.
Dreambot “customers” would infect victims, steal funds, and pay the Dreambot gang a week after week, month to month, or at a yearly expense. CSIS says this model seems to have been fruitful. “We counted more than a million [Dreambot] infections worldwide just for 2019,” Ancel said.
In any case, the CSIS researcher additionally said that as of late, Dreambot developed from being only a banking trojan. All the more explicitly, it evolved from a specific banking trojan into a generic trojan.
Criminals would lease access to the Dreambot cybercrime machine, yet not use it to steal money from bank accounts. Instead, they’d taint countless computers, and afterward review each target, searching for explicit computers.
Nonetheless, Dreambot operators have not been ‘publicly identified’ and stay on the loose. The explanation behind this whole cybercrime platform’s current disappearance likewise stays a mystery. Be that as it may, with the operators everywhere, Dreambot’s return ‘remains a possibility’.


