The human impact of a Royal Mail phishing scam
Last week, we looked at a Royal Mail themed scam which has very quickly become the weapon of choice for phishers. It’s pretty much everywhere at this point. Even one of my relatives with a semi-mystical ability to never experience a scam ever, received a fake SMS at the weekend.
The problem with common attacks is we grow complacent, or assume it isn’t really a big deal. Sadly, they’re always going to be a problem for someone. It doesn’t matter how tech-savvy you are, nothing is bulletproof. Anybody, including myself, can be caught out by a momentary lapse in concentration.
People who lose out to internet fakery often feel guilty, or assume that they messed up somehow. Nobody wants to be laughed at via internet shenanigans. I’d like to think most folks are sympathetic when people are brave enough to speak out.
“Surely people don’t fall for these things” is a well worn refrain. Sadly they do, and one such person spelt out the awful cost last Sunday. They had indeed received a bogus Royal Mail text, and entered their payment details into the phishing page. How bad could things get?
We’re about to find out.
Things have gotten: very bad
The victim was asked for a bogus £2.99 postage fee last Friday, having not seen the scam warnings circulating online. Below is an example of the scam that Malwarebytes Labs received:
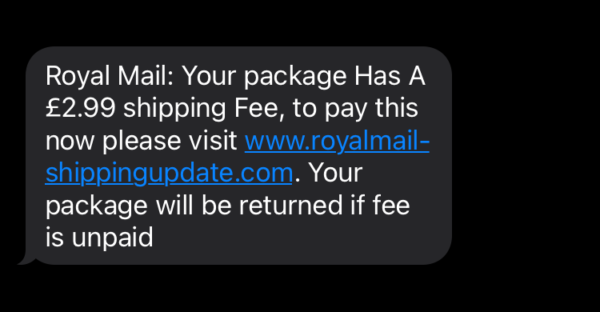
Royal Mail: Your package Has A £2.99 shipping Fee, to pay this now please visit www[dot]royalmail-shippingupdate[dot]com. Your package will be returned if fee is unpaid
In our last post about it, we pointed out that these scams work because with so much online ordering going on during this cardboard-laden pandemic, people aren’t 100% sure what’s due to arrive. And that means speculative messages about fake parcels have a good chance of success.
A similar thing happened here. If the target wasn’t due a birthday, the scam may not have worked on them. But the message will have gone to lots of people, and one of them, perhaps many, will have been expecting a delivery. As it was, they were expecting “a couple of packages” and so “thought nothing else of it”.
This is absolutely the key moment where the battle was already lost.
The scam asks recipients to pay a £2.99 GBP fee, but of course the scammers are after much more. To pay the fee, the victim has to enter their personal details, and credit card details.
Scammers get to work
The victim’s bank accounts were compromised very quickly, and the phishers wasting no time at all in going for gold. A day or so after they paid the bogus fee, the bank contacted the victim to let them know what had gone wrong. As it turns out, quite a lot:
- Multiple direct debits (recurring billing) for mobile phone companies and technology stores
- Transactions of £300 for the Argos store
- Debit cards for banking cancelled, with new ones issued as replacements
- Brand new sort code / account numbers for her bank account, as those had been given to the phishers too
This is really bad news for the victim, and a massive inconvenience. Don’t forget the pandemic impact here, either. At a time when the ideal option is cashless / card payments only, this person now has no cards and no easy way to withdraw money either.
If this had been where it ended, that would be bad enough. However, things were sadly about to get worse.
Phished by phone
The bank phoned the victim asking them to transfer their money into their “replacement” account. I’m sure you can already see where this is going wrong. No bank is going to cold call a scam victim, and also ask them to start transferring money. Why can’t the bank do it?
The answer, unfortunately, is that the bank can do it. This cold caller was a scammer armed with details gathered from the scam page a day or so prior. The follow up strike gave the individual, who was already reeling from rapidly losing lots of money, no time to regain some balance or get their game face on. If this call had come a week or so after the initial phish, the next few paragraphs would possibly look quite different.
From bad to worse
Good news: the victim asked the person on the call to verify their bank credentials. Bad news: they forgot the phisher already had access to everything in their account. As a result, they listed account balances and other information to keep everything nice and convincing.
Two smaller transactions were sent to the “new” account, at which point the victim realised they were being scammed all over again. Every penny they had to their name was gone.
Having wool pulled over your eyes once is bad enough. To then hand over cash to the scammers by telephone is the icing on a very bitter cake. So-called safe account scams are quite the pain, and this is what caught them out second time around.
A simple phish, a massive problem
There is no real happy ending to this tale currently, outside some reassurance the victim will probably get most or all of their money back. Consider that this person’s nightmare scenario began with a simple, believable, SMS message claiming a package was being held.
A few keystrokes, some brief personal information entered on a phishing site with Royal Mail branding, and they’ve been plunged into a situation which could take weeks or more to resolve. All that stress, in the middle of the never-ending pandemic. It’s an awful story, and a chilling insight into how much is at stake every single time a throwaway phish lands in your mailbox or SMS tray.
We wish Emmeline all the best in recovering her money and commend her for her courage in coming forward and showing the true cost of these scams.
The post The human impact of a Royal Mail phishing scam appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[INCRANSOM] - Ransomware Victim: C B King Memorial School(branch) 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)



