The Story Behind Security Breaches

There are many potential causes of security breaches, including malicious attacks, system glitches, equipment failures, software bugs, and zero days. What is a common root cause here? Human error.
According to Micke Ahola, “In a security context, human error means unintentional actions—or lack of action—by employees and users that cause, spread, or allow a security breach to take place.”
During the first quarter of 2020, Rapid7’s Managed Detection and Response (MDR) incident response team produced over 1,600 findings reports for clients, trends about which were revealed in our 2020: Q1 Threat Report. Here are some of the main stories behind security breaches and some ways your organization can effectively respond:
Stolen credentials
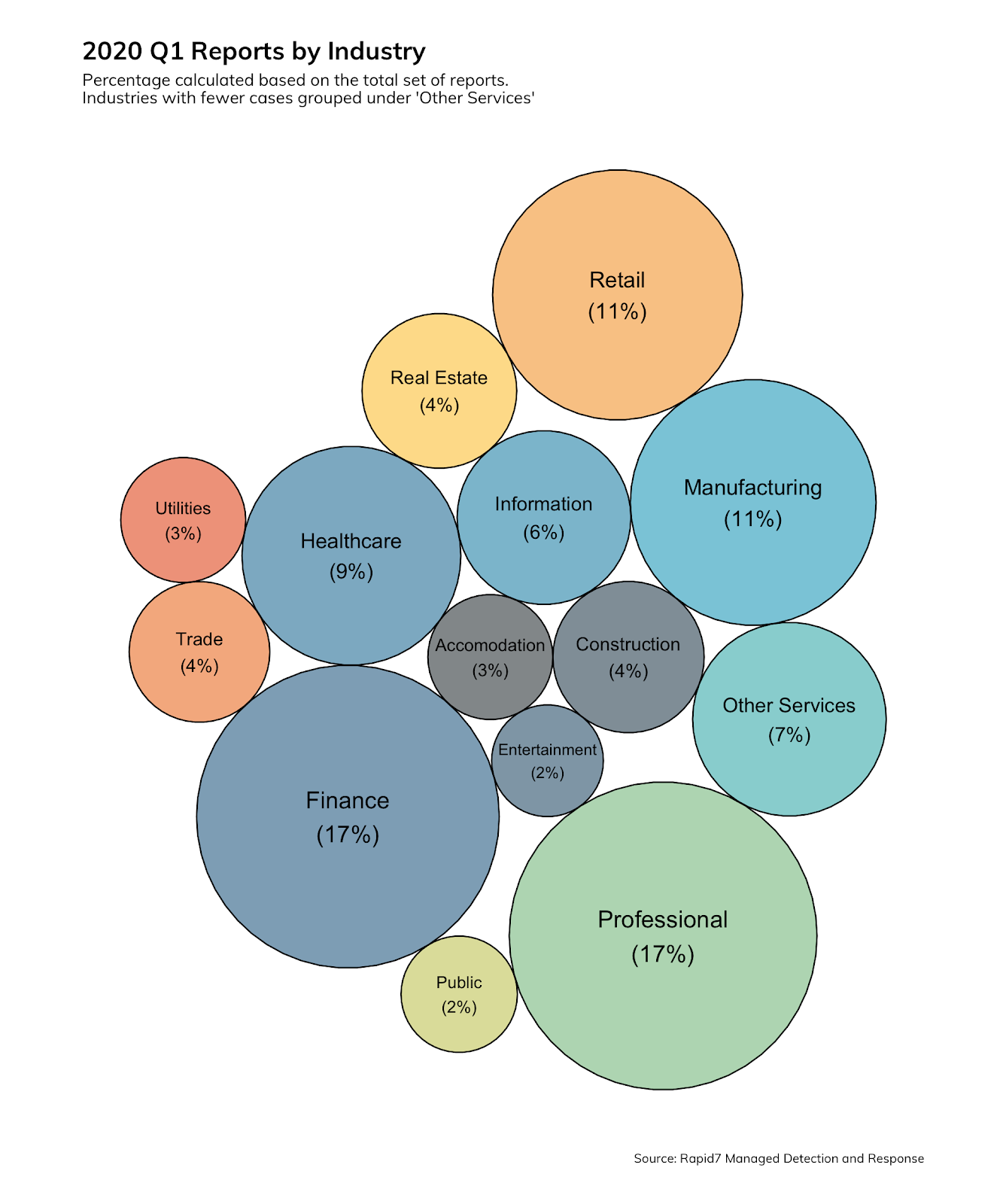
In 96% of Rapid7’s findings, a stolen credential was the cause of an incident. The top four industries affected by stolen credentials were:
- Finance (17%)
- Professional Services (17%)
- Manufacturing (11%)
- Healthcare (9%)
What can your organization do to protect itself against stolen credentials? Put multi-factor authentication (MFA) in place (at the very least for your executives and IT workers), so your users can securely access sensitive information in internal networks and cloud-based applications. Every user should also have a password vault to enable them to create unique passwords on your sites.
Less effective, but still necessary, are policies that explain your organization’s requirements for changing and reusing passwords and the consequences for not following them. User security education is necessary as well, so your users understand why these steps are so important.
Types of attacks and business size
Attacks come in several flavors, but the top three categories are malware, phishing, and malicious documents. Those account for almost 80% of the attacks Rapid7 saw during the first quarter of 2020. However, attack types are only limited by an attacker’s imagination and resources.
The size of a business is an attractor. Attackers scale and target attacks based on the business size. Smaller firms have fewer resources to fight attacks; while the rewards may be smaller, they may be simpler to achieve. A larger enterprise may suddenly become an easier target because of the impact of COVID-19 on available resources.
Examples of security errors
Read the Rapid7 2020 NICER Report for the scoop on internet cyber-exposure. Lack of patching or mitigation against severe vulnerabilities is still a big problem, particularly for critical assets. We have all seen recent severe vulnerabilities announced for such widely used products as Cisco ASA / Firepower, F5 BIG-IP, Microsoft DNS, NetScaler, Palo Alto, SAP, and Sophos XG Firewall. But even worse is running old software. Take SSH for example; 3.6 million servers are running SSH versions that are five years old or older. To fix these issues, setting up a change control process for high-priority vulnerability mitigation is a step in the right direction. Next, developing a process to mitigate zero-day vulnerabilities that are being exploited in the wild is paramount.
Using unencrypted, cleartext protocols to send information is another hazard. According to the NICER report, 42% more plaintext HTTP servers are used than HTTPS. If your organization is sending information that it considers important across the internet, encrypt it!
Misconfiguration of services like SMB is common. Routinely test network ingress and egress filters for SMB traffic and other common services and protocols that could leak important information to the Internet.
Common factors for human error
An organization must ask itself what causative factors are present in their environment that allow their users to make human errors. Here are some common reasons:
1. Action may not be proscribed by policy
2. Circumvention of policy or procedure to do a job function
3. Distraction
4. Environmental conditions
5. Incomplete training
6. Incorrect information
7. Lack of resources
8. Misunderstanding job functions
9. Overcomplicated tasks and procedures
10. Poor security culture or lack of awareness
11. Poorly documented processes and procedures
12. Time constraints
When someone makes a mistake, find out why they made the mistake and work on eliminating those factors.
Poor security culture or lack of security awareness can be a huge contributing circumstance to human error. End users may know the right course of action but fail to carry it out because there is an easier way to do things or they simply do not think it is important. Distraction could be another factor. You might identify with this one. Every office has a person who likes to have loud conversations in the cubicle area (back when we all had cubicles). Could he or she cause someone in the vicinity to make an error?
Other considerations include work environment conditions, such as temperature and privacy. Time constraints and interruptions can also be a factor. Even posture could be an influence, so encourage your users to take stretch breaks!
Preventing errors
Here are some recommendations from Rapid7 for preventing errors. Many of them are just common sense, such as controlling privileges. Everybody knows they should not be reading email from their admin account, but users still do it. Why? Because they can.
1. Reduce the opportunity
- Control privilege
- Control access by using multi-factor authentication
- Classify documents
- Implement asset management
- Implement password management tools
- Job training
- Limit access to customer and corporate private information
- Limit the access and privileges of third parties
- Simplify processes, procedures, and systems
2. Educate users on security best practices
- Educate users on why they should not use employee email addresses and/or reuse passwords on non-work-related sites
- Help your working-from-home users by giving them tips and best practices for using Wi-Fi securely.
3. Change security focus
- Encourage discussions on security topics
- Encourage security- and work-related questions
- Reward good behavior
- Use posters and reminders
Security education
Security education can be an easy way to change a user’s perception of security. Here are a few ideas: The first time a user reports a security issue, give them a coffee cup with a security slogan like “No Phishing Here!” Enter them in a quarterly or yearly drawing for a gift certificate for each subsequent report; it does not have to be for a lot of money. If someone makes a mistake, do not blame them. Help them understand and learn from the experience. (If they do not learn from it, that is a different conversation.)
Our clients tell us that being able to have a two-way conversation with the security team is a real winner. Get your marketing people involved in thinking up security campaigns. Short and sweet reminders work the best. Along with that once-a-year checkbox training, you can cover all the bases. Remember: “Checkbox education means checkbox decision-making when there’s a real threat.”
The bottom line
Enlist your users to help in the fight against human error. Encourage dialogue to root out common causes of errors. Talk to your users when you implement new policies and procedures. Help them understand why the organization is putting them in place.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[LYNX] - Ransomware Victim: Greta Group 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
