The story of the year: remote work

The coronavirus pandemic has caused sudden, sweeping change around the world. The necessary social distancing measures are having an impact on all of us. One large part of society that has been affected by these measures more than others is the employed. While direct customer facing businesses like restaurants and retailers have had to change their opening hours, adapt their business models or close their doors entirely, there are still millions of jobs that can be done at home, outside of the usual office working environment.
Organizations need to adapt to meet employee needs and ensure they stay productive, motivated and secure. With so many of us being asked to work in new ways in order to stay connected to our colleagues and customers, it is important to remember both the professional and personal challenges working from home on a permanent basis can bring. Quite obviously, this situation has brought a lot of issues into our lives. A survey conducted in April 2020, as things were changing rapidly, revealed that around half (46%) of respondents had never worked from home before and therefore, were not entirely ready for such changes.
There is a lot to be said about social and productivity issues caused by the new rhythm of work, but in fact, things were not that bad, because remote work in some cases helped people to have a better work-life balance and even be more productive.
What changed: guilty pleasures and life-work disbalance
Remote work is not an entirely new phenomenon; its benefits have been discussed for years now. In some industries, like IT, remote work has already been quite widespread. Last year, Kaspersky analyzed some of the positives of remote work. This research highlighted some of the most significant benefits of remote work, including increased employees’ productivity, improved work-life balance and reduced absenteeism. Situation in the world this year made it possible to verify such assumptions.
At the same time, the massive move towards remote work was not particularly voluntary – employees who were forced to work from home did not always welcome this opportunity as they had to contend with new challenges. However, they have also uncovered some substantial benefits:
- Comfort level: Employees became both more comfortable and uncomfortable. A study by Kaspersky in April found that nearly a third of employees (32%) working from home were struggling with back pain after being forced to use kitchen stools or a sofa to work. However, by November, employees had begun to compensate for this discomfort with certain “guilty pleasures”, such as “working in comfy clothes all day” (with 48% wanting to have this option in the future) and even “working without clothes”.
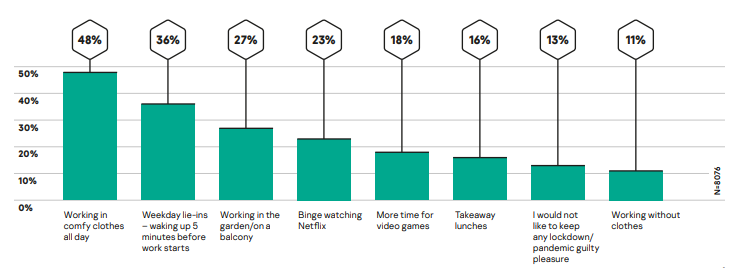
What lockdown/pandemic guilty pleasures would you like to keep?
- Family issues: Being at home all day has, not surprisingly, had an effect on people’s relationships with their loved ones, with 21% of respondents from the same study in April admitting to experiencing family issues due to remote work. Two drivers of this conflict are not having a separate room for every family member who needs to work from home (26%) and arguments about how much children should use the Internet (33%). But remote work is not all bad for families, as recent study found that 47% were now able to spend more time with their families, highlighting it as the key benefit of the whole work-from-home situation.
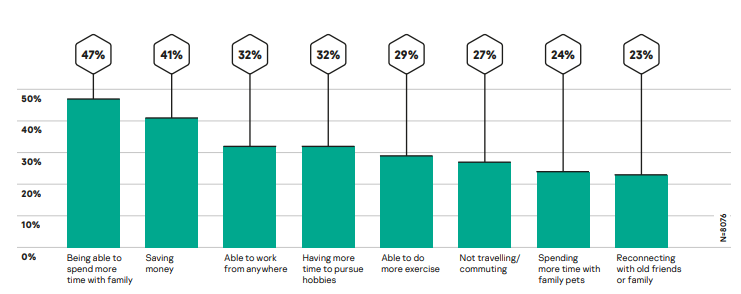
What positive things have come out of the pandemic that you would like to keep?
- Work-life balance: Staying at home has led to difficulties maintaining an appropriate work-life balance, with nearly a third of respondents (31%) from the same survey in April admitting that they were now working more, although 46% admitted they were now spending more time pursuing personal activities. However, by November, employee attitudes appear to have shifted in favor of remote work, with nearly three-quarters (74%) saying they were happy to never return to at least some of the traditional workplace dynamics.
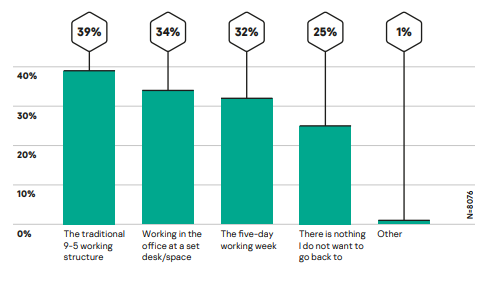
When thinking about the traditional, ‘old ways of working’ what do you not want to go back to?
- Productivity levels: As previously mentioned, studies have indicated that working remotely can actually lead to an increase in productivity. Kaspersky found that a full 40% of employees noticed no change in their productivity levels, with 29% admitting to being more productive. However, it is also important to note employees are still missing some aspects of the traditional workplace environment, chiefly seeing their colleagues face-to-face (34%).
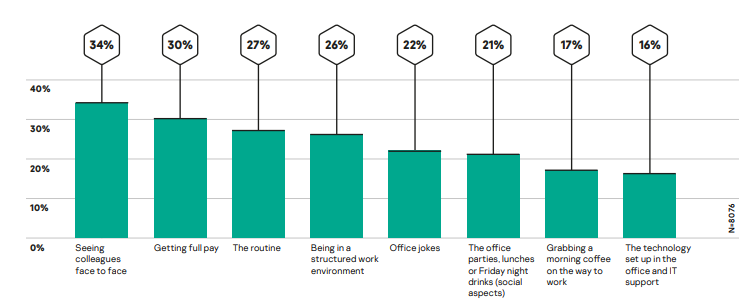
Over the past few months, what, if anything have you missed about work?
Security issues: old, new and refreshed
As shown above, questions regarding remote work – good or bad, better or worse for employees, helpful or not for businesses – are not as obvious as they might seem at first glance. However, in this report, we will focus mainly on what remote work means for businesses and employees from a security perspective. One of the most critical questions of work-from-home security is related to employees’ awareness of the main concepts of cybersecurity. As shown by the survey, by April, 73% of workers had not received any IT security awareness training from their employer since they transitioned to working from home, leading employees to feel unprepared for facing cybersecurity issues that may arise when working remotely.
Moreover, our research showed that remote staff tended to overestimate the level of their knowledge of cybersecurity basics. In the early April of 2020, Kaspersky and Area9 Lyceum released an adaptive learning course for those transitioning to at-home working, covering the basics of secure remote operations. Analysis of anonymized learning results revealed that in 90% of the cases where learners selected an incorrect answer, they evaluated their feelings about the given response as “I know this” or “I think I know this”.
The most dangerous outcome of such a situation is “unconscious incompetence”, when a user is not even thinking about potential risks of some action, because it is habitual and seems to be appropriate.
Shadow IT
Meanwhile, the adoption of video conferencing, file storage services, file sharing services and personal messaging apps are all on the rise as we rely on the Internet for sharing information and keeping in touch for work purposes. Some employees are not strictly using their business accounts for work-related purposes.
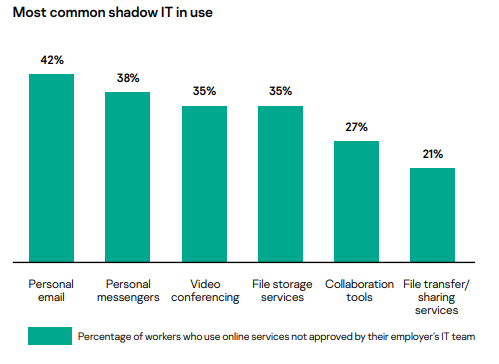
Most common shadow IT in use
For example, 42% of workers say they are using personal email accounts for work and nearly half (49%) have admitted to increasing how often they do this. Additionally, 38% use personal messengers for work purposes, and 60% say they now do this more often because of working from home. File-sharing services that have not been approved by IT departments are also being used a lot, with 53% of respondents saying they are using these more often for work-related purposes. Using such services has great benefits for keeping staff connected but can come at a cost if one or more of them become a target for cybercriminals, as it can lead to both theft of corporate information and unauthorized access to internal resources of the company.
According to our telemetry, cybercriminals were actively trying to masquerade their malware as popular messengers and online conference applications that were used by remote workers to replace offline communications. Kaspersky detected 1.66 million unique malicious files spread under the guise of such applications.
Applications used as lures, January – November 2020 (download)
Once installed, these files would primarily load Adware – programs that flooded victims’ devices with unwanted advertising and gathered their personal data for third-party use, but in particular cases the same spreading technique is used to download malicious implants for targeted espionage.
RDP attacks
Naturally, working from home requires employees to log in to corporate resources remotely from their personal devices. One of the most common tools used for this purpose is RDP, Microsoft’s proprietary protocol that enables users to access Windows workstations or servers. Unfortunately, given that many offices transitioned to remote work with little notice, many RDP servers were not properly configured, something cybercriminals have sought to take advantage of to gain unauthorized access to confidential corporate resources.
The most common type of attack being used is brute-force, wherein criminals attempt to find the username and password for the RDP connection by trying different combinations until the correct one is discovered. Once it is found, the cybercriminals gain remote access to the target computer on the network.
Starting in the beginning of March, the number of Bruteforce.Generic.RDP attacks skyrocketed, resulting in the total number of the attacks within the first eleven months of 2020 reaching 3.3 billion. Within the same eleven-month period in 2019, Kaspersky detected 969 million such attacks worldwide.
RDP attacks dynamics, January – November 2019 and 2020 (download)
Bring Your Own Device
A Kaspersky survey has found that a little more than two-thirds of respondents are using a personal computer to work from home, and nearly half have done so in the past. This kind of policy – Bring Your Own Device – has long been disputed in the cybersecurity world, as it tends to make corporate resources more vulnerable to attack. Even for those who have devices provided by their employers (55%), most do not separate their work and personal activities. In fact, a full 51% admit to watching adult content on the device they use for work, content that is frequently targeted by cybercriminals.
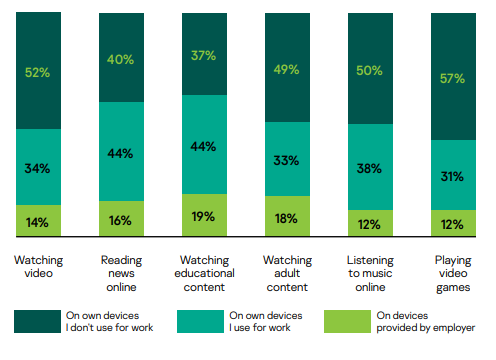
Activities workers are spending more of their time doing
Part of the problem with BYOD policies is that businesses that adopt them often do not accompany them with appropriate cybersecurity measures. The same survey that found that two-thirds of employees used their personal devices also found that half of companies with BYOD policies did not have policies in place to regulate their use – and only a third (32%) provided antivirus software for personal devices.
A virtual private network (VPN) allows for much more secure connections, but only 53% of workers are using one to access their corporate networks. This is particularly problematic if employees log in to corporate resources from unsecured public networks, say, in a coffee shop or restaurant. It is worth noting that, especially in smaller businesses, employees are storing documents with personally identifiable information. Should this information fall into the wrong hands, it would not only be problematic for the company, but would put the employer’s own privacy at risk.
In 2019, before remote work swept the world, Kaspersky found that over half (52%) of enterprises said that their breaches occurred as a result of employees’ inappropriate IT use. Working from home and using personal devices only compounds these risks, particularly when employees are not taught the appropriate cybersecurity policies or given the right tools.
Scam and phishing
One of the most common concerns for workers is related to phishing scams. For instance, more than a quarter (27%) of survey respondents say they have received malicious emails related to COVID-19 while working from home, an activity Kaspersky’s experts are paying strong attention to during the pandemic. Scammers may be trying to prey on worried workers who want to know more about the coronavirus pandemic.
According to Kaspersky telemetry, the amount of scam related to social payments increased fivefold in 2020 compared to the same period in 2019. Fraud emails of this kind offer various financial assistance, surcharges, allowances and other types of payments.

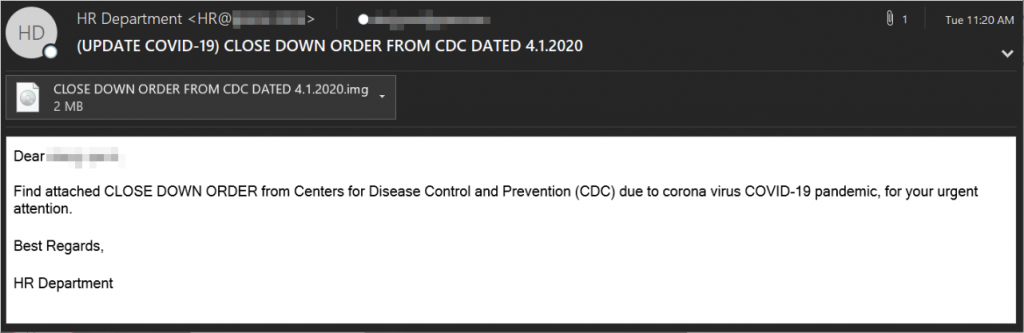
In another scenario, victims, receive email, purportedly from their HR departments, carrying important information about COVID-19 issued by the government institution (CDC) as an attachment. It comes in the form of an IMG file, which is just an enhanced carrier for malicious content capable of bypassing email filters.
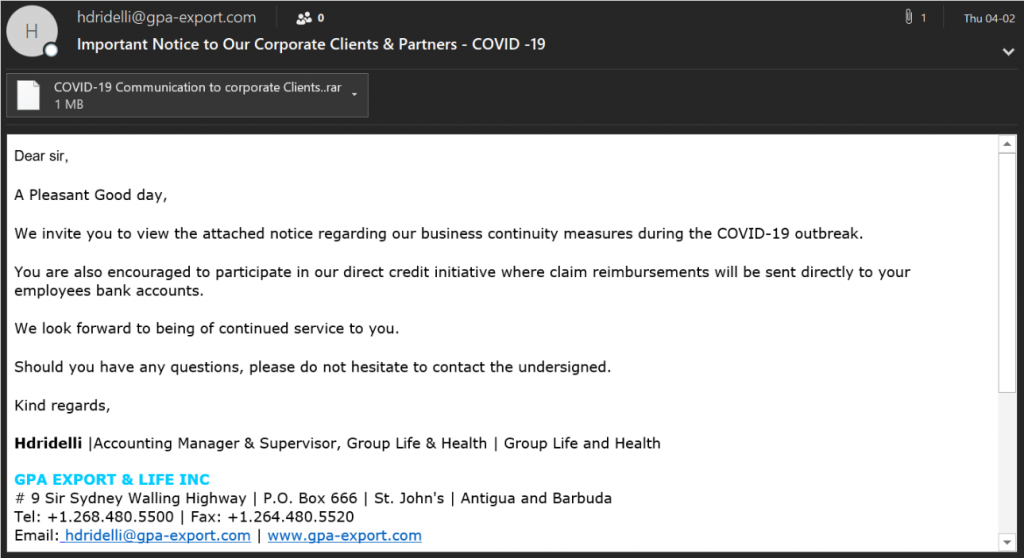
Another popular topic to exploit in times like these is money. Many people have lost their jobs or are close to unemployment. In exploiting the need for money, the attackers are offering reimbursement plans to individual employees. This type of offers characteristically contains a URL that the recipient is asked to follow or an attachment that needs to be opened.
And of course, the attackers could not keep from exploiting the name of the WHO itself.

Using the WHO logo seems to be so effective that sometimes, it occupies half of the email content, again spreading hope and false promises of a vaccine.

One fraudulent mailshot disguised as a WHO newsletter offered tips about staying safe from COVID-19.
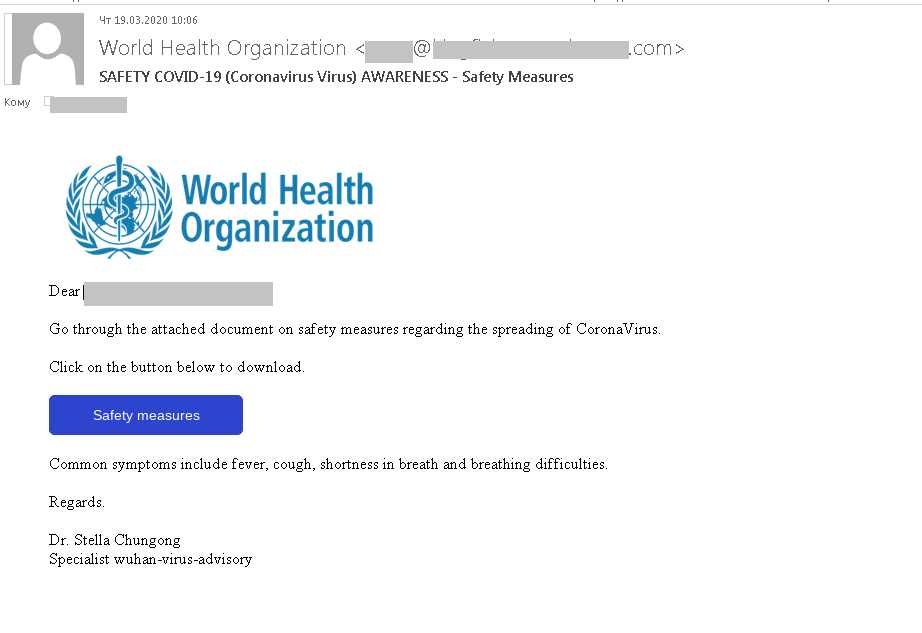
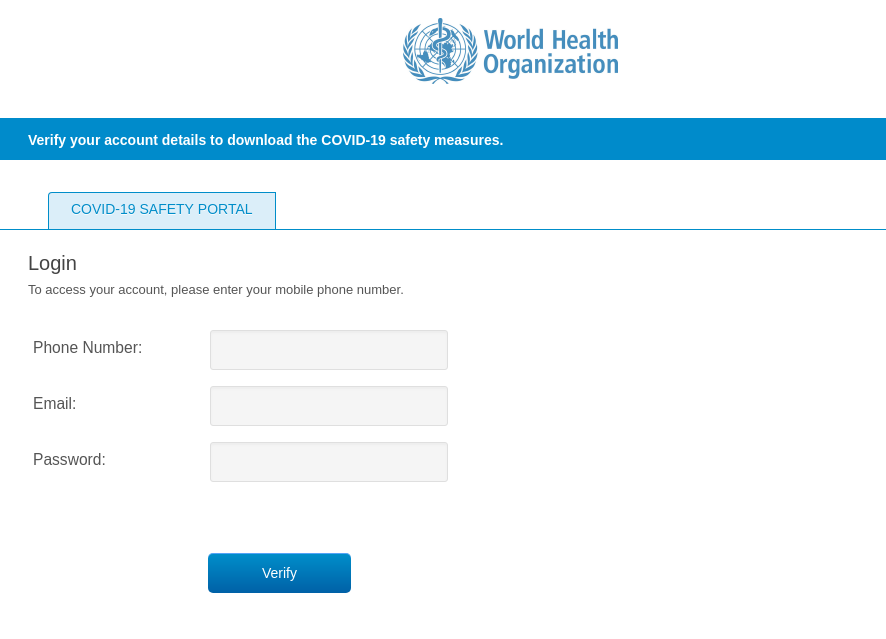
To get the information, the recipient had to click a link pointing to a fake WHO website. The design was so close to the original that only the URL gave away the scam. The cybercriminals were after login credentials for accounts on the official WHO site. Whereas in the mailshots above, only a username and password were asked for, in later ones, a phone number was also requested.
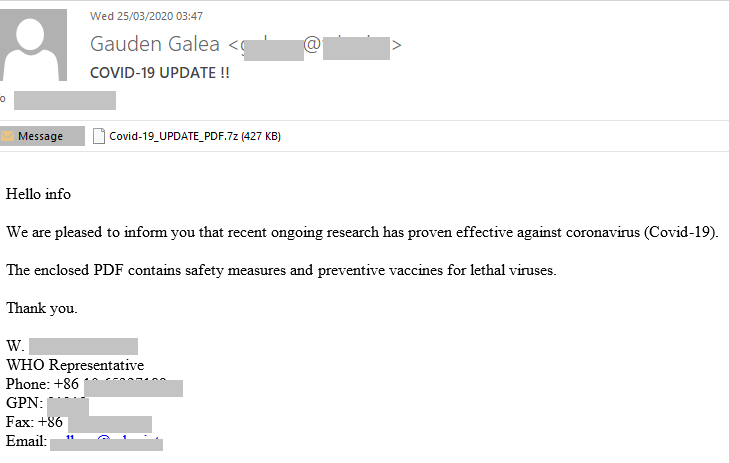
In addition, we detected several emails supposedly from the WHO, containing documents with malware. The recipient was asked to open the attachment in DOC or PDF format, which allegedly offered coronavirus prevention advice. For example, this message contained a copy of Backdoor.Win32.Androm.tvmf:

There were other, less elaborate mailshots with harmful attachments, including ones containing Trojan-Spy.Win32.Noon.gen:
APT groups
The COVID-19 topic was also abused in the world of APTs, where multiple threat actors used it to create lures. This applies, for example, to such threat actors as IronHusky and TransparentTribe.
IronHusky / ViciousPanda
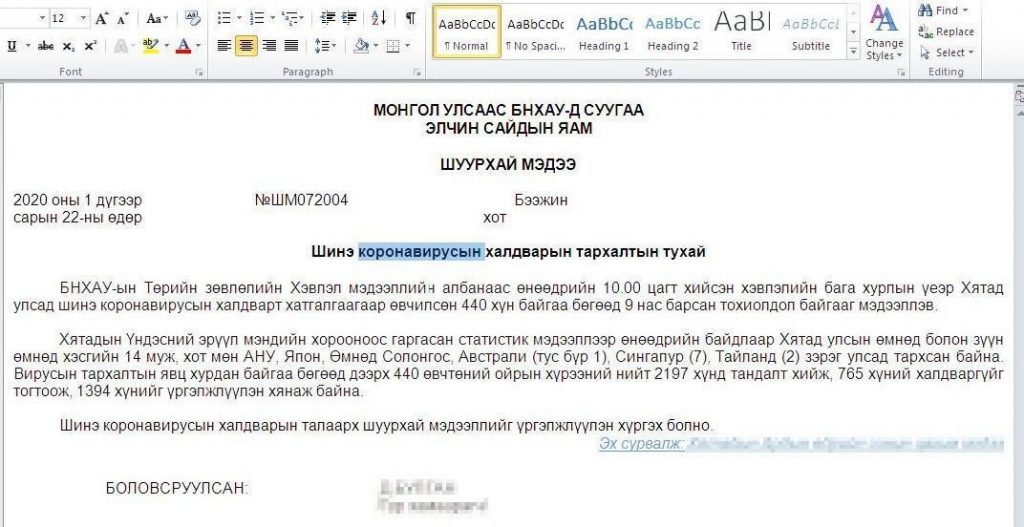
Documents used by this APT group normally contain VisualBasic macros or older exploits for Microsoft Office and, in the case of successful infection, they present decoy content such as shown here: a document in Mongolian, which looks like genuine correspondence between the Mongolian Ministry of External Affairs and China. It mentions concerns about the spreading epidemic in China and growing statistics in Asian countries.
TransparentTribe / MythicLeopard / APT36
This is another example of abusing the COVID-19 topic, this time by another APT group known as TransparentTribe, which reportedly has been active in South Asian countries, such as India and Pakistan. This time, it is an Excel spreadsheet which does not really change the medium of the attack from the previous case.
Ginp and tracking applications
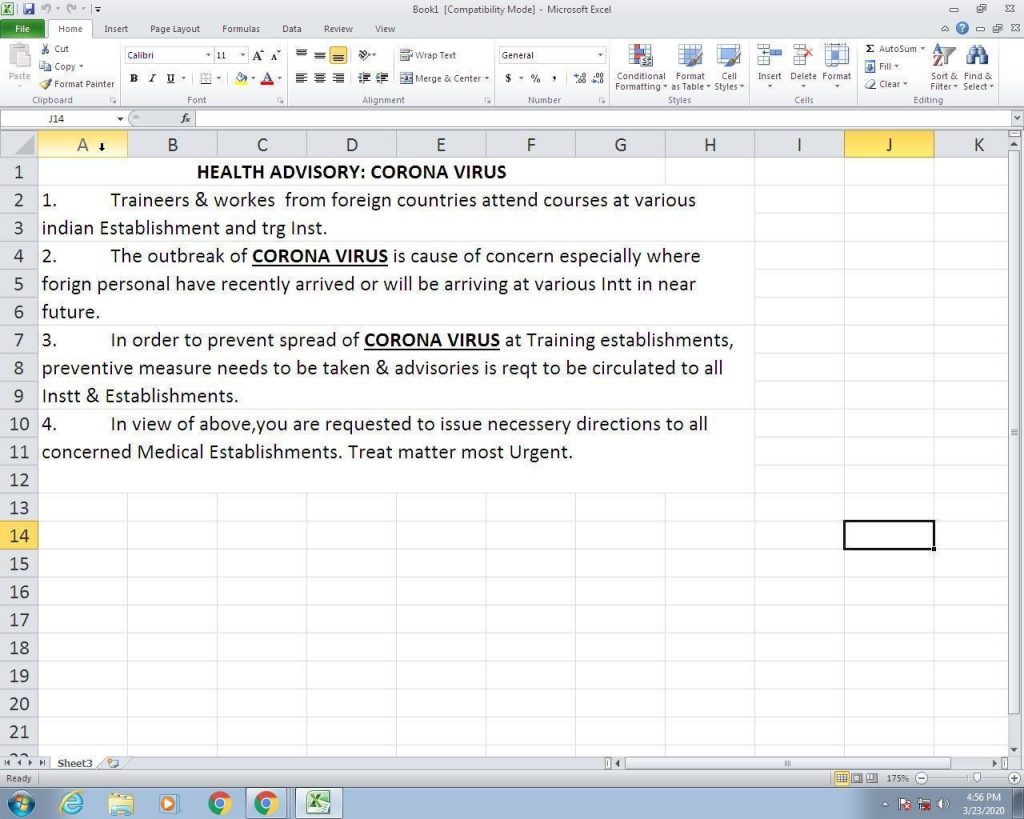
Even those cybercriminals who were acting only in the financial field adapted to the circumstances. A good example is Ginp, a banking trojan for Android used in a campaign exploiting the COVID-19 topic. After Ginp received a special command, it opened a web page titled “Coronavirus Finder”. The page had a simple interface that showed the number of nearby people infected with the coronavirus and urged the user to pay a small amount for seeing their exact locations.
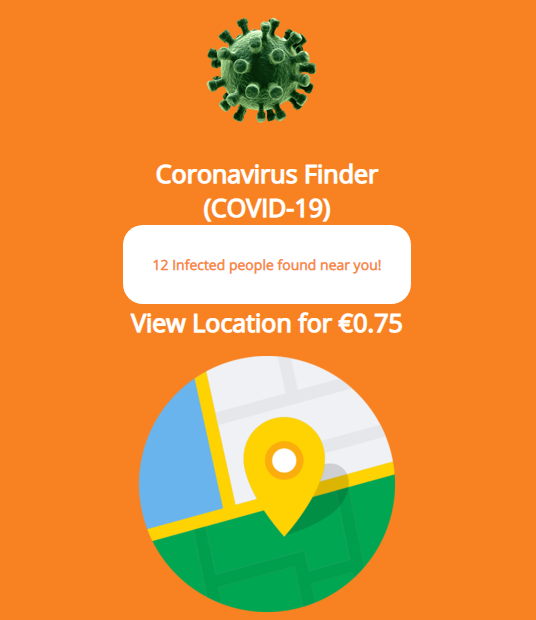
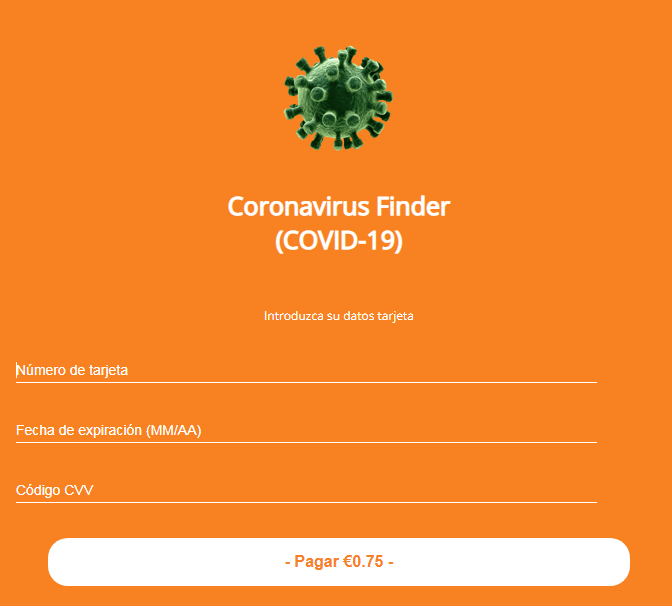
The web page offered the visitor to input bank card details to make the transaction. Once the details were entered, they went directly to the criminals, and nothing else would happen. The attackers did not even charge the victim the small amount. And of course, they did not show any information about the people infected with coronavirus, because they did not have any.
Home entertainment
Not all the threats are related to the work process directly. Employees are spending more time at home, playing games, ordering food and watching movies. Cybercriminals are aware of that and are doing their best to exploit this situation.
Gaming threats
According to our telemetry, in April 2020, the daily amount of attempts to visit malicious websites exploiting the gaming topic increased by 54% as compared to January. Interestingly, Minecraft was the most abused game, followed by Counter Strike: Global Offensive and The Witcher 3.
One of the most popular gaming platforms, Steam, was also frequently imitated by cybercriminals: the number of notifications from fake Steam sites increased by 40% between February 2020 and April. Cybercriminals’ main goal as usual is to persuade users to visit fraudulent sites or download and install malware, which could be anything from keyloggers to ransomware and miners.
Online cinemas
Online cinemas and streaming services were also used to lure users. Threat actors mimicked popular services, such as Netflix, Okko and IVI, to trick users, or simply used the titles of popular TV shows to name malicious files. The most popular TV shows among cybercriminals were Stranger Things, The Witcher, Sex Education and Orange Is the New Black.
This is just more proof that it is vital to use only official streaming services for watching media content and always stay alert while doing something online. In 2019, we published an extensive report on how cybercriminals had disguised malware as episodes of top TV shows. The results of the year 2020 are still waiting to be studied.
Phishing in delivery
Another topic is delivery services. As ordering of food and other products online grows in popularity, the number of scams abusing this topic is growing, too. One of the most common targets is Amazon clients, and in attempts to get them, phishers have used every trick they have: fake delivery confirmations, fake alerts of suspicious activity in the Amazon account, gift card fraud, etc. The names of other delivery services were also used in spam and phishing emails, mostly to give victims malware or links to fraudulent clones of well-known delivery websites.
Conclusion and recommendations
Overall, we have not seen anything conceptually new in the way attacks are executed or the techniques used by the attackers. Instead, we have seen them adapt to the current agenda and environment.
In the B2B sector, this manifested itself either in targeted attacks imitating email from specialized organizations, such as lures using the WHO logo and name, or attempting to take advantage of the fact that companies rapidly transitioned to remote work – often without having the time to ensure that proper security measures were in place. For example, brute-force attacks on RDP are not knew, but never before have so many employees used these protocols. That is likely the reason why they became the primary focus for attackers this year, as did instant messaging applications, with criminals increasingly spreading “fake” applications that mimicked popular ones used by businesses for remote collaboration.
While corporate and perimeter security remains important, the recent mass transition to remote work has shown all too clearly that even the best corporate security cannot compensate for a lack of user awareness. Especially with 60% of companies allowing employees to use their own devices for work, businesses must train their staff in cybersecurity best practices, so that they are aware of the risks and understand how to work securely with corporate resources. This cyberhygiene training must also be accompanied by changes in IT administration. IT needs to provide additional support to employees, making sure updates are applied on time and issues with connecting remotely are fixed promptly.
For many businesses, remote work is not a temporary solution. Many have already announced that, even after the pandemic subsides, work-from-home options and a hybrid model will become a permanent fixture of the employee experience. That means now is the time to reflect on the lessons of 2020 and begin creating a security strategy that protects you and your employees.
Moving forward, businesses will need to rethink the way their corporate networks are organized. Since all machines are not located in the office and hence, not connected to the corporate network, adjustments need to be made to ensure endpoints stay secure and corporate resources are protected. For example, for those with a corporate VPN, they need to take steps to ensure nothing illicit can be downloaded.
The world has been becoming more digital for years, but, in 2020, our entire lives moved online. Even self-described luddites had no choice but to use digital services: for shopping, business meetings, classes. And yes – cybercriminals were ready to jump on this opportunity. Attackers attempted to exploit the COVID-19 topic in every way possible, and they were, quite often, successful.
Part of the problem is that, when we teach good Internet safety practices, we are typically speaking to active internet users. But the pandemic forced everyone to become an active internet user even those who did not want to – and they were, naturally, more vulnerable to attack.
COVID-19 will not be the last crisis, nor will it be the last one attackers exploit for personal gain. Cybercriminals will always be ready to take advantage of disruptive current events. Moving forward, no matter who you are – whether you are a novice Internet user or an experienced one, whether you spend five hours a day online or thirty minutes – you need to be ready for the unexpected in cyberspace. The year 2020 has proven that. Fortunately, staying protected against an evolving set of cyber risks does not require any high tech or advanced programming skills. It just requires a little knowledge of basic cybersafety rules.
Here are some tips to help employers and businesses stay on top of any potential IT security issues and remain productive while staff are working from home:
- Ensure your employees have all they need to securely work from home and know who to contact if they face an IT or security issue.
- Schedule basic security awareness training for your employees. This can be done online and cover essential practices, such as account and password management, email security, endpoint security and web browsing. Kaspersky and Area9 Lyceum have prepared a free course to help staff work safely from home.
- Take key data protection measures including switching on password protection, encrypting work devices and ensuring data is backed up.
- Ensure devices, software, applications and services are kept updated with the latest patches.
- Install proven protection software, such as Kaspersky Endpoint Security Cloud, on all endpoints, including mobile devices, and switch on firewalls.
- Ensure you have access to the latest threat intelligence to bolster your protection solution. For example, Kaspersky offers a free COVID-19-related threat data feed.
- Double-check the protection available on mobile devices. For example, it should enable anti-theft capabilities such as remote device location, locking and wiping of data, screen locking, passwords and biometric security features like Face ID or Touch ID, as well as enable application controls to ensure only approved applications are used by employees.
- In addition to physical endpoints, it is important to protect cloud workloads and virtual desktop infrastructure. As such, Kaspersky Hybrid Cloud Security protects hybrid infrastructure of physical and virtual endpoints, as well as cloud workloads whether running on-premise, in a datacenter or in a public cloud. It supports integration with major cloud platforms, such as VMware, Citrix or Microsoft, and facilitates migration from physical to virtual desktops.
While there is a lot of responsibility on employers to keep corporate devices and networks secure, Kaspersky is also offering the following recommendations for consumers and workers during their time at home:
- Ensure your router supports and works smoothly when transmitting Wi-Fi to several devices simultaneously, even when multiple workers are online and there is heavy traffic (as is the case when using video conferencing).
- Regularly update your router to avoid potential security issues.
- Set up strong passwords for your router and Wi-Fi network.
- If you can, only do work on devices provided by your employer. Putting corporate information on your personal devices could lead to potential security and confidentiality issues.
- Do not share your work account details with anybody else, even if it seems a good idea at the time.
- Always feel able to speak to your employer’s IT or IT security team if you have any concerns or issues while working from home.
- Follow the rules of cyberhygiene: use strong passwords for all accounts, do not open suspicious links from emails and IMs, never install software from third-party markets, be alert and use reliable security solution such as Kaspersky Security Cloud.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.





