The Vice Society ransomware group has adopted new custom ransomware with a strong encryption scheme in recent intrusions
The Vice Society ransomware group has adopted new custom ransomware, with a strong encryption scheme, in recent intrusions.
SentinelOne researchers discovered that the Vice Society ransomware gang has started using a custom ransomware that implements a robust encryption scheme, using NTRUEncrypt and ChaCha20-Poly1305 algorithms.
Vice Society ransomware has been active since June 2021, it is considered by researchers a spin-off of the HelloKitty ransomware, the malware targets both Windows and Linux systems primarily belonging to small or midsize victims.
This group focuses on public school districts and other educational institutions, like other ransomware gangs it implements a double extortion model and publishes data stolen from the victims on a data leak site.
The new variant, dubbed “PolyVice”, was used in a recent attack and appended the file extension “.ViceSociety” to all encrypted files. The malware dropped ransom notes with the file name “AllYFilesAE” in each encrypted directory.
The researchers speculate the ransomware was in the early stages of development, they found debugging messages in the code.
SentinelOne noticed a significant overlap with the process implemented in the RedAlert ransomware, a circumstance that suggests that both variants were developed by the same threat actor.
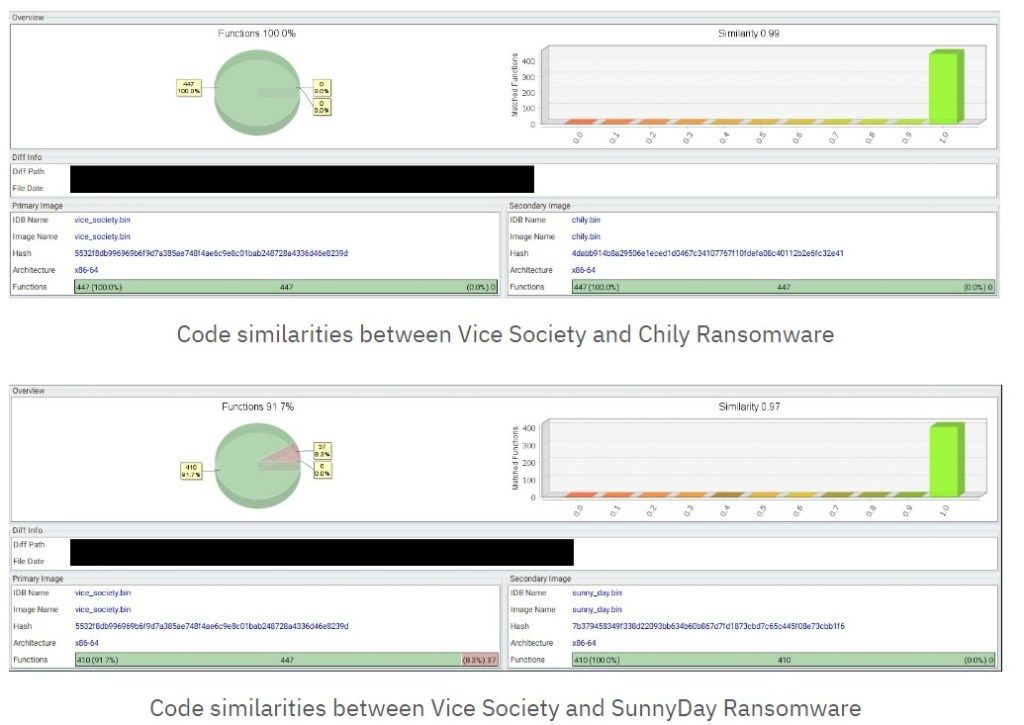
Further investigation also revealed that codebase for the Vice Society Windows payload has been used to build custom-branded payloads for other ransomware groups, such as “Chily” and “SunnyDay.”
“We assess it’s likely that a previously unknown developer or group of developers with specialized expertise in ransomware development is selling custom-branded ransomware payloads to multiple groups. The details embedded in these payloads make it highly unlikely that Vice Society, SunnyDay, and Chily ransomware are operated by the same group.” continues the report. “The delivery method for this “Locker as a Service” is unclear, but the code design suggests the ransomware developer provides a builder that enables buyers to independently generate any number of lockers/decryptors by binary patching a template payload.”
Buyers can customize their ransomware without revealing any source code and can generate branded payloads to run their own RaaS programs.
The encryption scheme used by PolyVice combines asymmetric and symmetric encryption to securely encrypt files. It leverages a quantum-resistant NTRUEncrypt algorithm for asymmetric encryption, and an open source implementation of the ChaCha20-Poly1305 algorithm for symmetric encryption.
The PolyVice locker implement a multi-threading approach to parallelize the encryption process.
The malware uses the CreateThread function to spawn multiple workers and relies on a WaitForMultipleObject call to synchronize with the main thread,
The main thread and the worker threads use an I/O Completion Port to exchange data.
PolyVice worker reads the file content to determine the speed optimizations to apply which depend on the file size. The PolyVice ransomware applies intermittent encryption selectively.
- Files smaller than 5MB are fully encrypted.
- Files with a size between 5MB and 100MB are partially encrypted:
- A total of 5MB of content is encrypted by splitting them into 2 chunks of 2.5MB. First chunk from the top and the second chunk from the bottom of the file.
- Files bigger than 100MB are partially encrypted:
- A total of 25MB of content is encrypted in intermittent mode split into 10 chunks of 2.5MB distributed every 10% of the file size.
“The adoption of the PolyVice Ransomware variant has further strengthened their ransomware campaigns, enabling them to quickly and effectively encrypt victims’ data using a robust encryption scheme.” concludes the report. “The ransomware ecosystem is constantly evolving, with the trend of hyperspecialization and outsourcing continuously growing.”
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on Patreon using the button below

To keep up to date follow us on the below channels.