Threat spotlight: Conti, the ransomware used in the HSE healthcare attack
On the 14th of May, the Health Service Executive (HSE), Ireland’s publicly funded healthcare system, fell victim to a Conti ransomware attack, forcing the organization to shut down more than 80,000 affected endpoints and plunging them back to the age of pen and paper. This happened a week after DarkSide, another ransomware strain, hit the USA’s Colonial Pipeline systems.
More than 290 healthcare and first-responder organizations (of the 400 affacted worldwide) that fell victim to a Conti ransomware attack were based in the US. New Zealand, too, has reported of at least 5 hospitals shutting down their IT network in response to a similar attack.
In this blog, we’ll home in on Conti, the strain identified by some as the successor, cousin or relative of Ryuk ransomware, due to similarities in code use and distribution tactics.
Threat profile: Conti ransomware
Conti ransomware is created and distributed by a group the cybersecurity industry has named Wizard Spider, the same Russian cybercriminal group that created the infamous Ryuk ransomware. It is offered to trusted affiliates as Ransomware-as-a-service (RaaS).
According to Coveware, a company that offers incident response services to organizations impacted by ransomware attacks, Conti is the second most common ransomware family that victim organizations have reported in the first quarter of 2021. (The first is Ransom.Sodinokibi, which Malwarebytes has already profiled and has been detecting since 2019.)
There are several ways Conti ransomware could end up on a corporate network. As with other “big game” ransomware, the delivery method changes according to the preferences of the group operating it, but among the most common attack vectors are remote desktop protocol (RDP), phishing, and weaknesses in either software or hardware.
In the case of phishing campaigns, Wizard Spider and its affiliates have been known to use legitimate Google document URLs in the email body. Recipients are encouraged to click this link, which actually contains code that allows for the download and execution of either Bazar, a backdoor, or IcedID (aka BokBot), a Trojan.
Much like other RaaS tools, part of the overall Conti ransomware attack is human-operated, which means actors behind these attacks move laterally within compromised networks using tools like RDP, PsExec, and Cobalt Strike. The ransomware is executed manually in memory across all active endpoints, after as many files as possible have been exfiltrated. The files are then held for ransom and the victim is threatened by data loss, because of the encryption, and leaking of the exfiltrated data. Files are encrypted with a combination of AES-256 and RSA-4096 via the Microsoft CryptoAPI, as per CrowdStrike. Earlier versions appended the .CONTI extension to encrypted files. Newer versions now append a random 5-character string.
Below are screenshots of two of the four possible ransom notes that Conti ransomware leaves behind after fully encrypting affected endpoints. Known ransom note file names are CONTI.txt, R3ADM3.txt, readme.txt, and CONTI_README.txt.
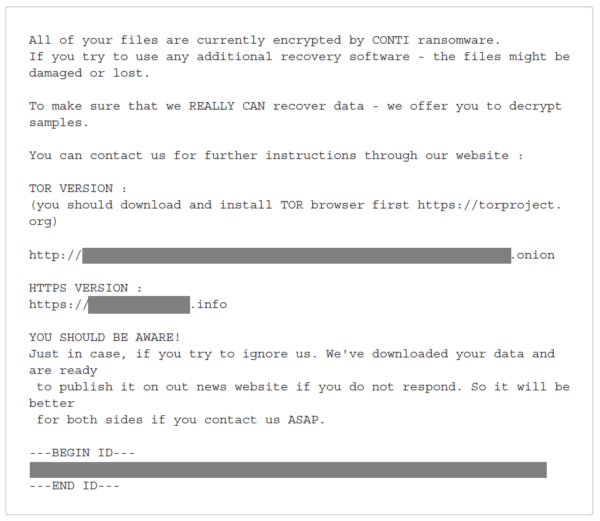
All of your files are currently encrypted by CONTI ransomware.
If you try to use any additional recovery software – the files might be damaged or lost.To make sure that we REALLY CAN discover data – we offer you to decrypt samples.
You can contact us for further instructions through our website :
TOR version :
(you should download and install TOR browser first https://torproject.org)[redacted]
HTTPS VERSION :
[redacted]YOU SHOULD BE AWARE!
Just in case, if you try to ignore us. We’ve downloaded your data and are ready to publish it on out [sic] news website if you do not respond. So it will be better for both sides if you contact us ASAP.
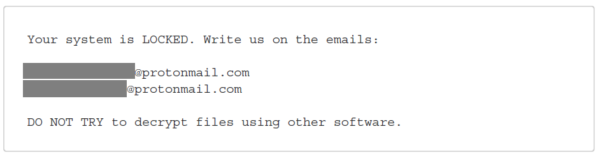
Your system is LOCKED. Write us on the emails:
[redacted]
[redacted]
DO NOT TRY to decrypt files using other software.
Conti is thought to be related to Ryuk ransomware somehow. In a conversation with BleepingComputer, threat hunter and CEO of Advanced Intelligence (AdvIntel) Vitali Kremez said, “Based on multiple incident response matters and current assessment, it is believed that Conti ransomware is linked to the same Ryuk ransomware developer group based on the code reuse and unique TrickBot distribution. The same distribution attack vector is used widely by the Ryuk deployment group.”
Conti is unique in terms of its “lightning-fast” ability to encrypt files, and how much control it gives to its operator, according to Carbon Black’s Threat Analysis Unit (TAU). When encrypting, Conti uses 32 simultaneous CPU threads for speedier encryption—a huge number of threads compared to other ransomware families that also support multi-threaded operations.
Conti gives its controller the fine-grained option of skipping encrypting files on a local drive in favor of encrypting those on network shares by allowing a human to instruct it via a command-line interface.
Lastly, Conti misuses the Windows Restart Manager to free up files being used by applications—whether they are writing to or reading them—at time of infection by safely terminating these apps so Conti can encrypt the freed files as well.
Malwarebytes’ signature-less protection detects all known variants of Conti.
Adversary profile: Wizard Spider
Wizard Spider is a cybercrime group affiliated with a what is sometimes called the Ransomware Cartel, a collective of underground groups identified by threat intelligence company Analyst1. The group is known to operate a roster of technical tools it created and will willingly let other crime groups use—as long as they are trustworthy enough. When it first surfaced in September 2016, they were using TrickBot, aka TrickLoader, a highly popular banking Trojan.
They changed their tactics in 2018 and started using ransomware in the form of Ryuk. They are perhaps one of the early groups that got into “big game” attacks—and Ryuk was designed for this very purpose. Two years later, the group moved to using Conti, in May 2020.
It is believed that some members of Wizard Spider were once associated with the Dyre/Dyreza group. If you may recall, the group behind Dyre was responsible for attacking Sherwin-Williams, an Ohio-based building materials and paint company.
Unlike some other underground cybercriminal gangs, Wizard Spider doesn’t openly advertise on underground forums, perhaps for security reasons.
The sophisticated tools Wizard Spider have created tell us something of the threat group’s character: they’re resilient, persistent, adaptive, determined, and overall, very efficient.
Prepare for hard battles ahead
The Conti attack against the HSE has poleaxed Ireland’s healthcare system. Fifteen days after the attack, the Irish Independent reports that about half of outpatient appointments are being cancelled daily. At the time of writing, that adds up to just over 100,000 appointments cancelled so far. HSE head Paul Reid estimates that the cost of restoring and updating its systems could reach €100m.
Ransomware attacks, after all, are not just about systems getting crippled and files being held hostage for a fee. It’s also knowingly putting lives at risk to satisfy a deep, insatiable want for money.
Indeed, hard battles are ahead. And as much as we’d like to think that HSE might be a step too far, even for ruthless threat groups like Wizard Spider, it’s not. We should continue to expect the worst, and remember that prevention is better than attempting to apply a cure after the attackers arrive.
Below is a list of recommended mitigations from the FBI, which it issued along with an alert on Conti ransomware late last week:
- Regularly back up data, air gap, and password protect backup copies offline. Ensure copies of critical data are not accessible for modification or deletion from the system where the data resides.
- Implement network segmentation.
- Implement a recovery plan to maintain and retain multiple copies of sensitive or proprietary data and servers in a physically separate, segmented, secure location (i.e., hard drive, storage device, the cloud).
- Install updates/patch operating systems, software, and firmware as soon as they are released.
- Use multi-factor authentication where possible.
- Use strong passwords and regularly change passwords to network systems and accounts, implementing the shortest acceptable timeframe for password changes. Avoid reusing passwords for multiple accounts.
- Disable unused remote access/RDP ports and monitor remote access/RDP logs.
- Require administrator credentials to install software.
- Audit user accounts with administrative privileges and configure access controls with least privilege in mind.
- Install and regularly update anti-virus/anti-malware software on all hosts.
- Only use secure networks and avoid using public Wi-Fi networks. Consider installing and using a VPN.
- Consider adding an email banner to messages coming from outside your organizations.
- Disable hyperlinks in received emails.
- Focus on cyber security awareness and training. Regularly provide users with training on information security principles and techniques as well as overall emerging cybersecurity risks and vulnerabilities (i.e., ransomware and phishing scams).
The post Threat spotlight: Conti, the ransomware used in the HSE healthcare attack appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.




