Threat spotlight: RobbinHood ransomware takes the driver’s seat
Despite their name, the RobbinHood cybercriminal gang is not stealing from the rich to give to the poor. Instead, these ransomware developers are more like big game hunters—attacking enterprise organizations and critical infrastructure and keeping all the spoils for themselves.
In 2019, the RobbinHood ransomware creators successfully attacked and received ransom payouts from the cities of Baltimore, Maryland, and Greenville, North Carolina. Not ones for humility, they now mention those successes in revised ransom notes, pointing out to victims that it’s useless to try recovering their files in any other way than paying the ransom.
And the ransom isn’t exactly cheap. RobbinHood ransom demands can range from 3 Bitcoins for a single computer up to 13 Bitcoins for a complete network, which translates to tens of thousands of dollars.
How RobbinHood ransomware works
Like many other ransomware families, RobbinHood, which Malwarebytes detects as Ransom.RobbinHood, has been observed gaining access to organizations’ networks through brute force of Remote Desktop Protocols (RDP) or by using other Trojans that provide access to the attackers.
Once the attacker has gained sufficient access to the system, researchers found that in some cases they introduce a vulnerable kernel driver from Gigabyte. This driver is signed by the motherboard manufacturer and will be accepted by Windows because of the digital signature. But the driver has a long-standing vulnerability listed as CVE-2018-19320, which allows a local attacker to take complete control of the affected system.
The attacker uses this vulnerability to stop 181 specific services, disabling many protective programs, backup software, and deleting files that would normally be locked. System services often keep critical files in use, so they can’t be deleted or modified. Being able to stop these services from the kernel driver level makes taking full control of a system much easier.
Before the actual encryption begins, RobbinHood also disconnects all network shares, deletes all shadow copies, clears event logs, and disables Windows automatic repair.
For the encryption process itself, it fetches a public key from the file pub.key in the Windows temp folder. While encrypting files, an AES key is created for each separate file. The ransomware will then encrypt the AES key and the original filename with the public RSA encryption key and append it to the encrypted file. Each encrypted file will then be renamed using the format:
Encrypted_[randomstring].enc_robbinhood
During encryption, these folders are skipped:
- ProgramData
- Windows
- bootmgr
- Boot
- $WINDOWS.~BT
- Windows.old
- Temp
- tmp
- Program Files
- Program Files (x86)
- AppData
- $Recycle.bin
- System Volume Information
Four different ransom notes are dropped in every folder that contains encrypted files. Most of the notes contain information similar to the one below:
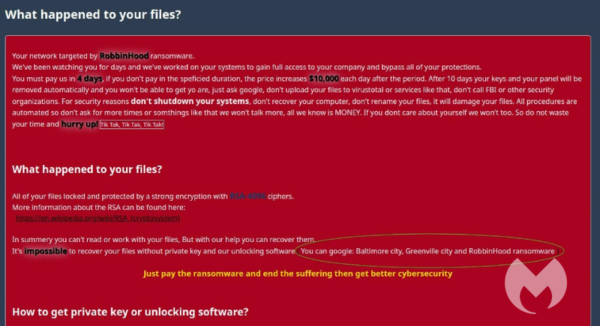
What happened to your files?
All your files are encrypted with RSA-4096, Read more on https://en.wikipedia.org/wiki/RSA_(cryptosystem)
RSA is an algorithm used by modern computers to encrypt and decrypt the data. RSA is an asymmetric cryptographic algorithm. Asymmetric means that there are two different keys. This is also called public key cryptography, because one of the keys can be given to anyone:
1 -We encrypted your files with our “Public key”
2 -You can decrypt, the encrypted files with specific “Private key” and your private key is in our hands ( It’s not possible to recover your files without our private key )
Is it possible to get back your data?
Yes, We have a decrypter with all your private keys. We have two options to get all your data back.
Follow the instructions to get all your data back:
OPTION 1
Step 1: You must send us 3 Bitcoin(s) for each affected system
Step 2: Inform us in panel with hostname(s) of the system you want, wait for confirmation and get your
OPTION 2
Step 1: You must send us 13 Bitcoin(s) for all affected system
Step 2: Inform us in panel, wait for confirmation and get all your decrypters
Our Bitcoin address is: xxx BE CAREFUL, THE COST OF YOUR PAYMENT INCREASES $10,000 EACH DAY AFTER THE FOURTH DAY
Access to the panel ( Contact us )The panel address: hxxp://xbt4titax4pzza6w[.]onion/
Alternative addresses
hxxps://xbt4titax4pzza6w.onion[.]pet/
hxxps://xbt4titax4pzza6w.onion[.]to/
Access to the panel using Tor Browser
If non of our links are accessible you can try tor browser to get in touch with us:
Step 1: Download Tor Browser from here: https://www.torproject.org/download/download.html.en
Step 2: Run Tor Browser and wait to connect
Step 3: Visit our website at: panel address
If you’re having a problem with using Tor Browser, Ask Google: how to use tor browser
Wants to make sure we have your decrypter?
To make sure we have your decrypter you can upload at most 3 files (maximum size allowance is 10 MB in total) and get your data back as a demo.
Where to buy Bitcoin?
The easiest way is LocalBitcoins, but you can find more websites to buy bitcoin using Google Search: buy bitcoin online
Decrypting may not be enough
As a warning to those who might consider paying the ransom, as Baltimore and Greenville did: Simply decrypting the files may not be enough to bring systems back online. The introduction of the vulnerable kernel driver and changing the behavior of the kernel may cause other problems on affected systems, which may result in deprecated performance or BSODs.
Reportedly, the recovery from the ransomware attack cost the city of Baltimore over US$10 million, which dwarfs the paid ransom of 13 Bitcoin (roughly US$80,000).
How to prevent RobbinHood ransomware
As with all ransomware families, the best method of protection is preventing the infection from happening in the first place. Since RobbinHood targets organizations, IT and security teams should take the following common precautions to secure against its attack:
- Secure your Remote Desktop Protocol (RDP) access
- Disable or block unused ports in general
- Apply the latest Microsoft updates
- Keep your anti-malware software up to date
Recommended reading: How to protect your RDP access from ransomware attacks
How Malwarebytes protects against ransomware
Malwarebytes can protect systems against RobbinHood ransomware in several ways.
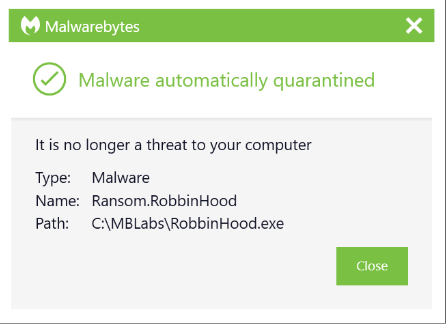
The Malwarebytes Anti-Malware technology detects malicious files, browser modifications, and system modifications on Windows PCs using a combination of signature-based and signatureless technologies. This layer of protection detects the RobbinHood binary itself. Detections can happen in real time as the binary is run or the infection can be rooted out from an already-compromised machine by conducting a full system scan.
Anti-Ransomware is a signatureless technology in charge of monitoring system activity of processes against a certain subset of data in specific locations on the endpoint. Using patented technology, Anti-Ransomware assesses changes in those data files. If an internal scoring threshold is crossed by a monitored process, it triggers a detection from the Anti-Ransomware component.
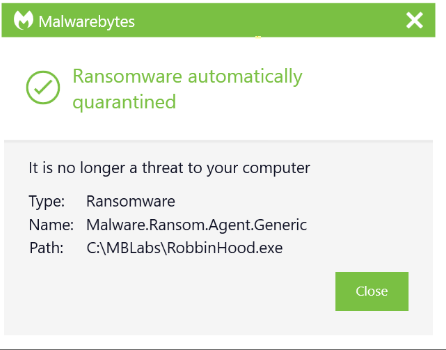
For those already infected, Ransomware Rollback can help recover encrypted files within 72 hours of the attack. Rollback creates a local cache on the endpoint to store changes to files on the system. It can use this cache to help revert changes caused by a threat. The Rollback feature is dependent on activity monitoring available in Malwarebytes Endpoint Detection and Response.
IOCs
Files (SHA256 hashes):
- 791c32a95f401f7464214960e49e716656f6fd6fff135ac2a6ba607236d3346e
- 99c3cc348f8ee4e87bce45b1dd185d31830c370ac43fd3e39ac50340f029ef79
- e9188ace227b00cbf1f6fba3ceb32af8e4d456c3a0815300a224a9d9e00778a8
- 47d892da6a49b02a2904bdc0d03ecef66c076481d19ab19251d86d11be494765
Ransom notes:
- _Decrypt_Files.html
- _Decryption_ReadMe.html
- _Help_Help_Help.html
- _Help_Important.html
Extension of encrypted files:
.enc_robbinhood
Stay safe everyone!
The post Threat spotlight: RobbinHood ransomware takes the driver’s seat appeared first on Malwarebytes Labs.


