Trick or Treat! What We Can Learn from the Spookiest Vulnerabilities of the Year

Spooky season is in full swing, and we’re not just talking about Halloween. Security vulnerabilities can range from tiny errors to large-scale gaps in protection, and all have different consequences. We put together a list of some of the scariest vulnerabilities of the year (the tricks!) and the remediation solutions that can help you stay on guard in the future (the treats!).
SMBghost
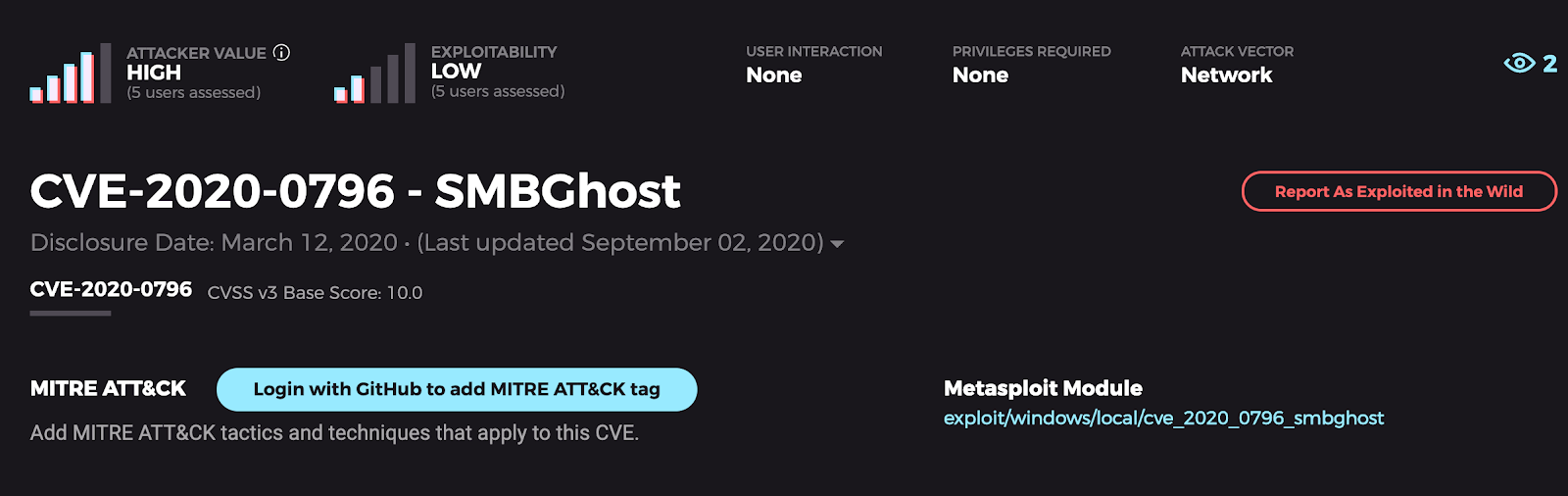
The Trick: SMBghost is a buffer overflow vulnerability when compression is enabled in Microsoft SMB Servers. The vulnerability is due to an error when the vulnerable software handles a maliciously crafted compressed data packet. A remote, unauthenticated attacker can exploit this to execute arbitrary code within the context of the application. Yikes!
The impact that the exploitation of this vulnerability has is very high, due to this having the ability to be exploited remotely and the sense that it grants system-level access in kernel mode. This vulnerability has also been deemed as wormable, which makes it a priority for attackers to utilize.
The Treat: Though the attacker value is very high, most AttackerKB users have noted that the vuln’s exploitability is relatively low. Microsoft has since released a patch for this vulnerability and suggests that users take proper precaution when enabling compression within SMB. Now, with many knowledge workers still stuck at home thanks to the pandemic, and therefore not spending a lot of time hanging out in SMB-heavy environments, this sequestration might actually be limiting the value of this and other SMB vulnerabilities—maybe working from home might actually be good for security!
BlueGate
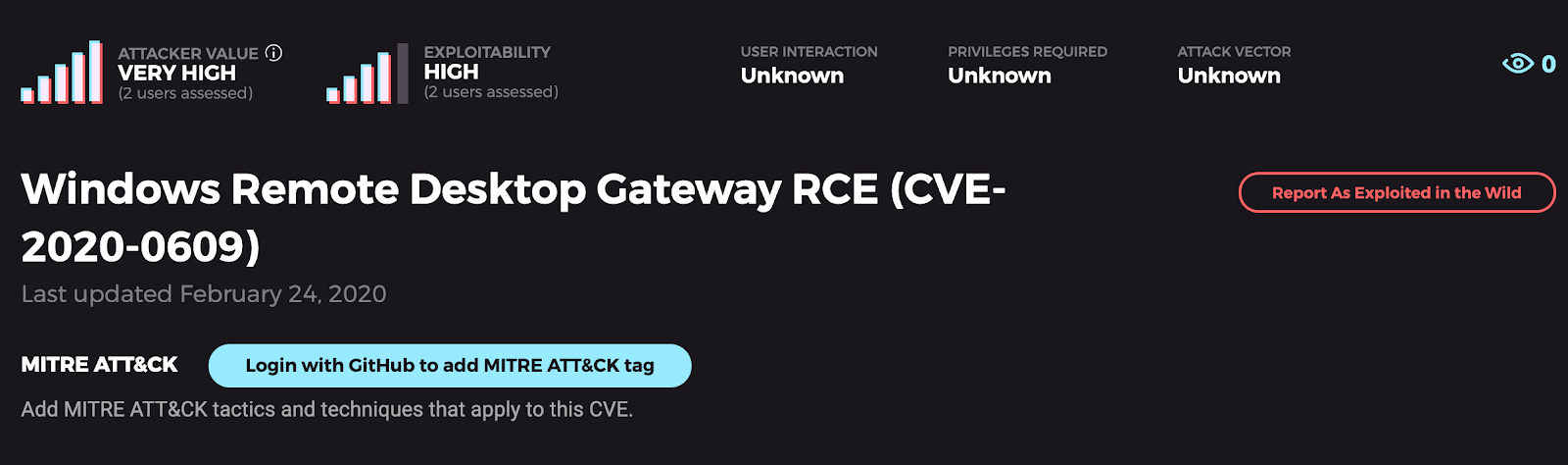
The Trick: A remote code execution vulnerability exists in Windows Remote Desktop Gateway (RD Gateway) when an unauthenticated attacker connects to the target system using RDP and sends specially crafted requests. This vulnerability is pre-authentication and requires no user interaction. An attacker who successfully exploited this vulnerability could execute arbitrary code on the target system. An attacker could then install programs, view, change, or delete data, or create new accounts with full user rights. A ghost-like attacker messing with your data? Pretty spooky.
The Treat: This ghost is probably going away with regular and timely security patches. Though it goes against expert advice to deploy right smack on the internet, maintainers of such servers just need to keep up on their patches in the same way a typical IIS administrator does. The Microsoft-issued update addresses the vulnerability by correcting how RD Gateway handles connection requests.
Ripple20
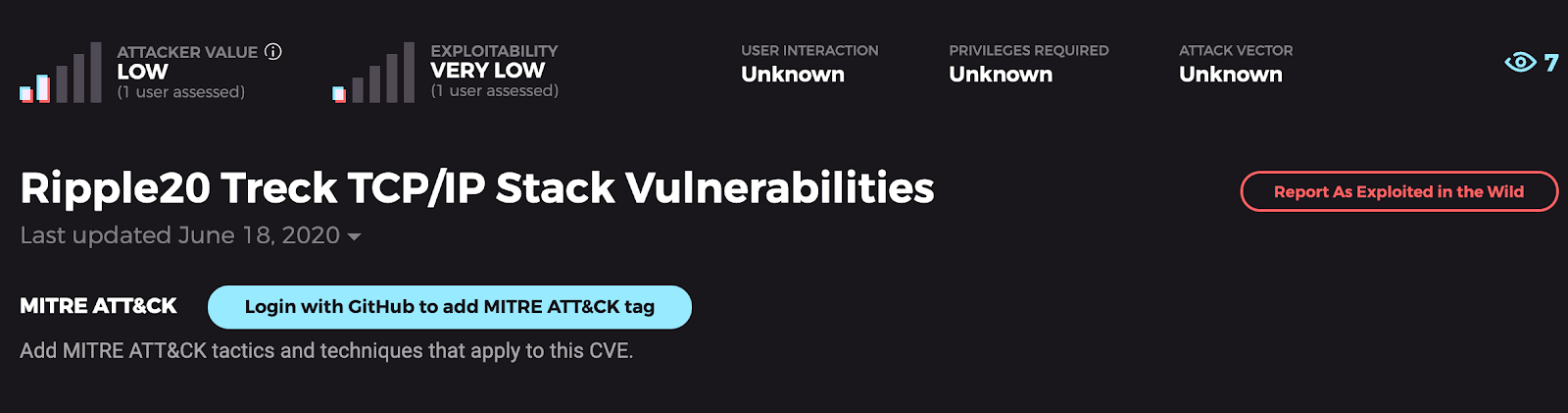
The Trick: In June, security firm JSOF published research on a collection of 19 vulnerabilities in a low-level TP/IP software library developed by Trek, a company that has distributed embedded internet protocols since the ’90s. The 19 vulnerabilities “affect hundreds of millions of devices (or more),” thanks to the ripple effect of the supply chain. Consider “19” to be quite the opposite of a magic number. The 19 vulnerabilities are not equal in their severity and potential impact and are likely to persist for some time.
The Treat: Is there any good news? Well, the practical attacker value of this suite of vulnerabilities is, on the whole, relatively low. This is in large part because of the lack of attack scalability: Each attack will, in all likelihood, need to be tailor-made for the target device, and even the value of targeting specific devices is heavily dependent on device capabilities and the context in which that device is used. The Treck TCP/IP stack is geared toward low-resource devices, which makes the Ripple20 vulnerabilities significantly less likely to be targeted in resource-heavy attacks such as crypto-mining or ransomware campaigns. If users want to change course from a scary ending to a happy one, users are best served by applying detections at the edge and internal network level to filter out malformed TCP/IP packets, IP fragments, and other lesser-used networking features, where possible.
Bad Neighbor
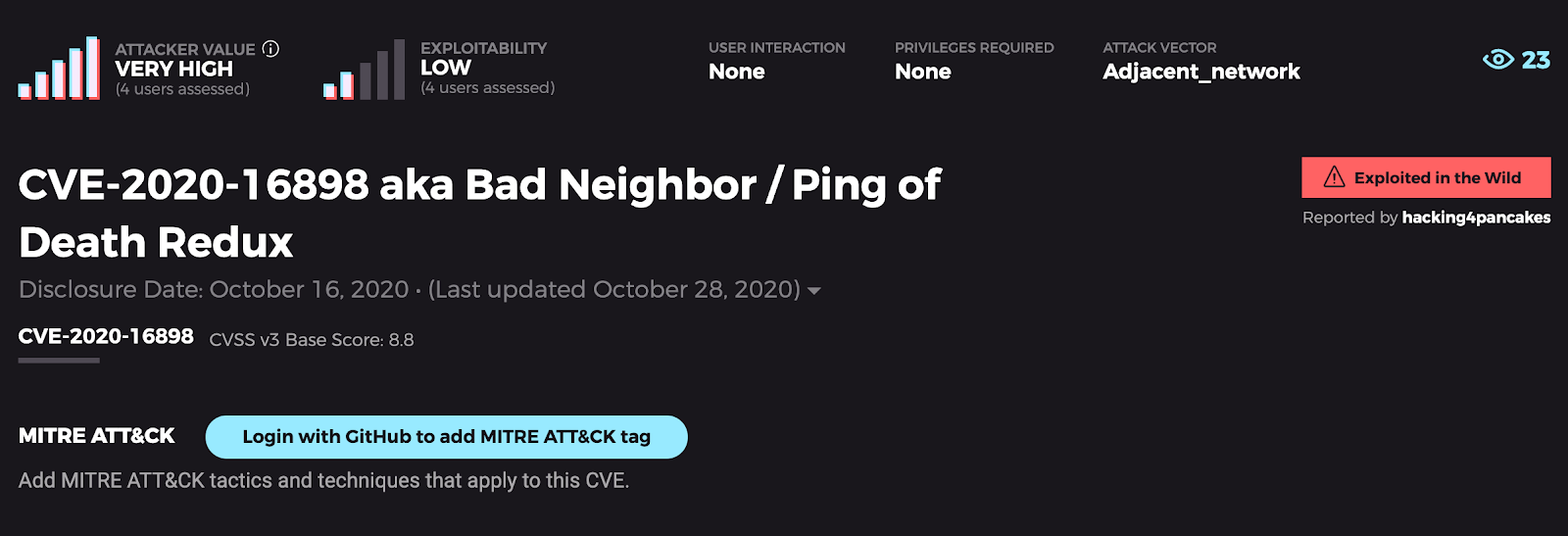
The Trick: Bad Neighbor is a remote code execution vulnerability that arises when the Windows TCP/IP stack improperly handles ICMPv6 Router Advertisement packets. An attacker who successfully exploits this vulnerability could gain the ability to execute code on the target server or client. The vulnerability has garnered broad attention as potentially wormable. This bad neighbor is probably someone who gives out wormable apples instead of candy.
The Treat: You can’t call the homeowners association on this one, but we recommend applying the patch for CVE-2020-16898 (Bad Neighbor) as soon as possible. For those who are unable to patch immediately, consider disabling ICMPv6 RDNSS as a workaround.
RECON
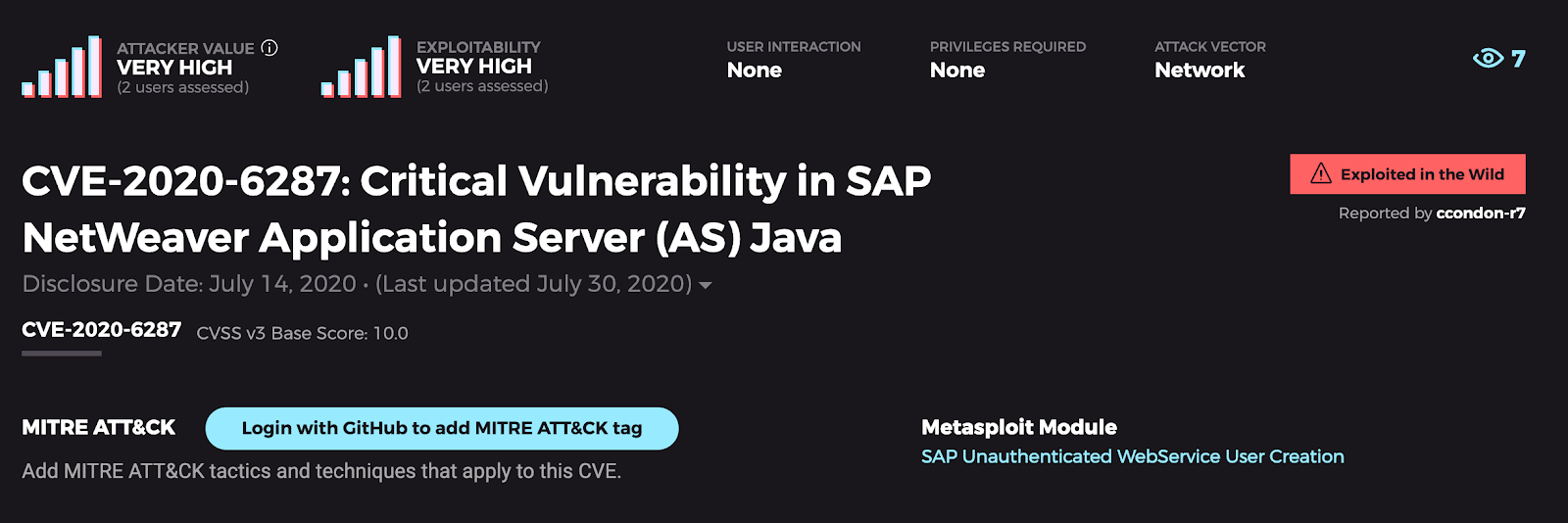
The Trick: This critical SAP vulnerability (RECON) from July affects the SAP NetWeaver Application Server (AS) Java component LM Configuration Wizard. Though a few months have passed since its publication, it’s still a big deal, especially since exploit code is publicly available. Businesses rely on SAP for a wide variety of processes, capturing everything from financial data to business intelligence. Most organizations use it as a tool to manage compliance and ensure access is provisioned (and, more importantly, deprovisioned) with urgency. The critical component to this vulnerability is that it does not require authentication to exploit, meaning any SAP NetWeaver system with the vulnerable components exposed to the internet—currently estimated to be at least 4,000—can be trivially compromised to wreak havoc on business systems. So, yeah, this one is big-time scary.
The Treat: This trick feels more like a long con. And how do you unravel the layers and remediate a long con? Conversations should begin with IT by identifying which physical or virtual assets are affected. SAP NetWeaver serves as the base layer for many SAP products, so many applications and processes are likely affected. Understanding how many systems you need to apply this patch to will help you begin to communicate estimated downtime to the business. Treating vulnerabilities, especially severe ones like this, is an exercise in diplomacy, politics, and trade-offs. For some, this will require removing SAP’s direct access to the internet. For others, it will require implementing WAF and/or IPS rules. CISA strongly recommends closely monitoring SAP NetWeaver AS for anomalous activity. SAP customers should be on the lookout for unusual processes spawned under the context of users that match the <sid>adm naming convention. File metadata may also be a good way to identify when SAP NetWeaver software spawns non-SAP binaries. Rapid7 also recommends ensuring that any web service does not run using a privileged account. For others, it will result in accepting the risk. The key message here is to sit down with all stakeholders, including business leaders, to get on the same page about the severity of this vulnerability, develop and activate a treatment plan, and make sure to have, at a minimum, detective controls in place to respond.
SigRed
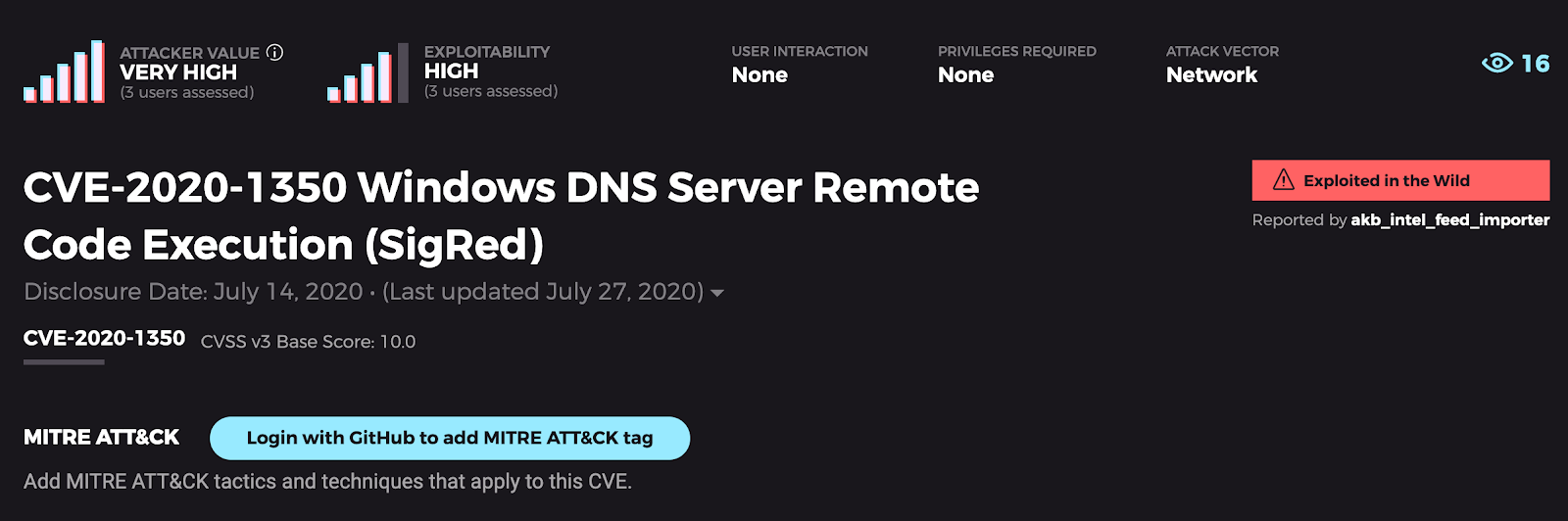
The Trick: A remote code execution vulnerability codenamed “SigRed” exists in Windows Domain Name System servers when they fail to properly handle requests. Successful exploitation can result in domain administrator privileges, compromising critical business data, assets, and infrastructure. If that wasn’t scary enough, Homeland Security decided to get involved. The U.S. Department of Homeland Security issued an emergency directive on July 16, 2020 requiring federal agencies to patch or mitigate the vulnerability within 24 hours—only the third time CISA’s current director has taken such an action. As with any vulnerability known to be wormable, CVE-2020-1350, or SigRed, will make an attractive target for ransomware campaigns in addition to stealthier threat actors.
The Treat: CISA put out urgent guidance to those who have Windows servers running DNS: patch on an emergency basis. Microsoft released guidance on mitigations for those who cannot patch, but as with other recent high-severity, high-urgency vulnerabilities, it is highly recommended that defenders prioritize patching over mitigation wherever possible. When attacker value is this high, don’t just run for the hills—instead, follow the rules and prioritize patching to keep monsters out of your servers.
Curveball
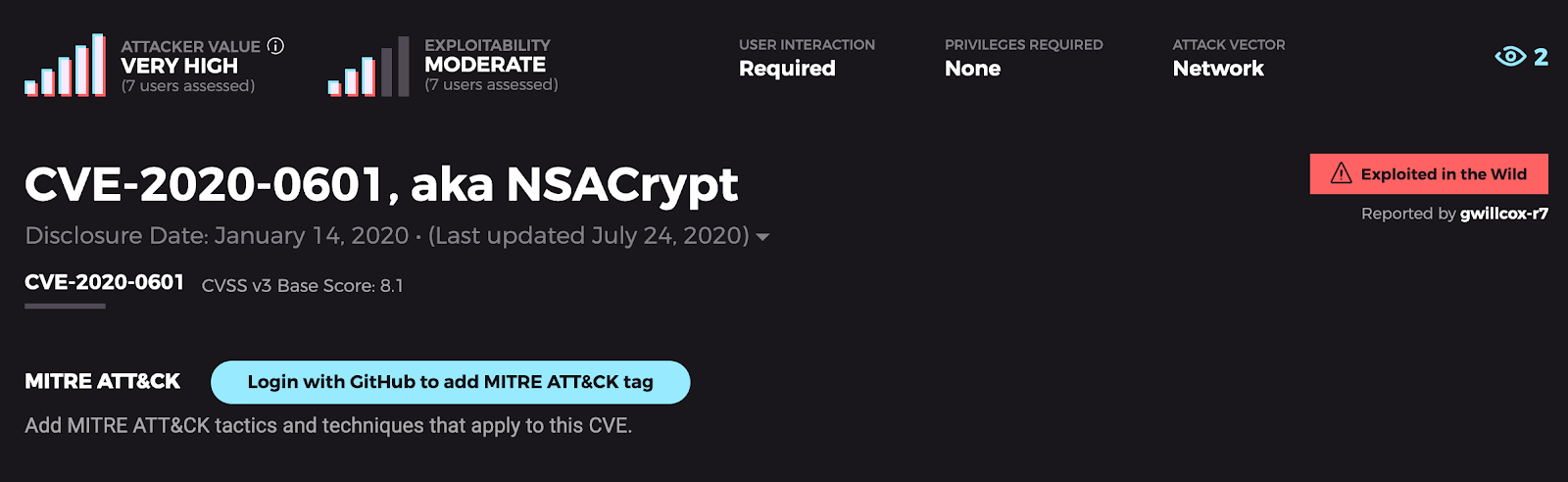
The Trick: In January, a flaw (CVE-2020-0601 or Curveball) was found in the way the Microsoft Windows CryptoAPI performs certificate validation, allowing attackers to spoof X.509 vulnerabilities. This is core cryptographic functionality used by a number of different software components, with far-reaching impact ranging from programming languages to web browsers.
The Treat: This year started out with a fright, but there are some silver linings. The mitigation steps taken by Microsoft and others (e.g., Google Chrome) to detect and alert users to exploitation attempts are a welcome development for defenders and users. Windows Update services were not affected by this due to extended hardening in years past, showing that defense-in-depth is important for maintaining critical infrastructure. This vulnerability also highlights a specification flaw that software projects should heed: Untested features are likely vulnerable features. Because this vulnerability is in an extremely seldom-used feature of the TLS specification that allows users to specify their own elliptical curves, it meant the feature was largely untested. Vulnerability hunters and defenders may be on the lookout for similar bugs in other TLS implementations in the future.
It’s Halloween, not April fools, and these vulnerabilities are no joke. As with any security scare, it’s important not only to remediate, but to reflect on what we can learn from these mistakes. If you’re looking for more visibility into which of these vulnerabilities is present in your organization, learn more about our vulnerability management tool, InsightVM.
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.




