UK and allies expose Russian FSB hacking group, sanction members

The UK National Cyber Security Centre (NCSC) and Microsoft warn that the Russian state-backed actor “Callisto Group” (aka “Seaborgium” or “Star Blizzard”) is targeting organizations worldwide with spear-phishing campaigns used to steal account credentials and data.
Callisto is an advanced persistent threat actor (APT) that has been active since late 2015 and has been attributed to Russia’s ‘Centre 18’ division of the Federal Security Service (FSB)
Last year, Microsoft’s threat analysts disrupted a group’s attack targeting various European NATO countries by deactivating the threat actor’s Microsoft accounts used for surveillance and email collection. Microsoft also reported 69 domains associated with their phishing campaigns to shut down the sites.
In January this year, NCSC warned about Callisto’s attacks, underlining the group’s open-source intelligence (OSINT) and social engineering skills.
Today, the United Kingdom officially attributed attacks to Callisto that led to the leaking of UK-US trade documents, the 2018 hack of the UK think tank Institute for Statecraft, and more recently, the hack on StateCraft’s founder Christopher Donnelly.
In addition, the UK says the group is behind credential and data theft attacks against parliamentarians from multiple political parties, universities, journalists, the public sector, non-government organizations, and other civil society organizations.
“The Foreign, Commonwealth and Development Office has also summoned the Russian Ambassador to express the UK’s deep concern about Russia’s sustained attempts to use cyber to interfere in political and democratic processes in the UK and beyond,” reads a press statement from UK.
Callisto’s latest tactics
In a bulletin published today, the UK’s NCSC says Callisto remains focused on launching spear-phishing attacks targeting the country’s governmental organizations, think tanks, politicians, defense-industrial units, and various NGOs.
“This advisory raises awareness of the spear-phishing techniques Star Blizzard uses to target individuals and organisations. This activity is continuing through 2023,” warns the NCSC.
The attackers source key information from social media platforms like LinkedIn and then approach their targets by emailing personal addresses that are less likely to be monitored by enterprise security software.
After building rapport with the target over time, Callisto sends a malicious link embedded in a PDF document hosted on Google Drive or OneDrive, which takes the target to a phishing site.
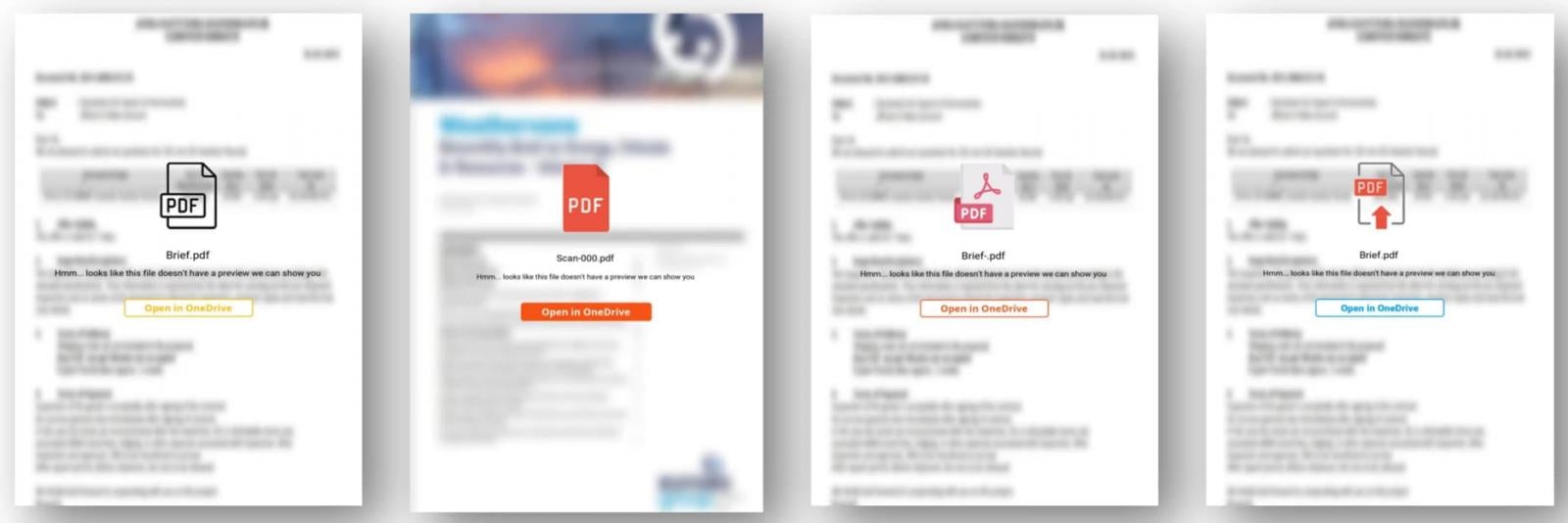

The phishing sites, hosted on illegitimate domains, target Microsoft, Yahoo, and other emailing platforms and are often protected by a CAPTCHA to filter out bots and give a sense of extra legitimacy.
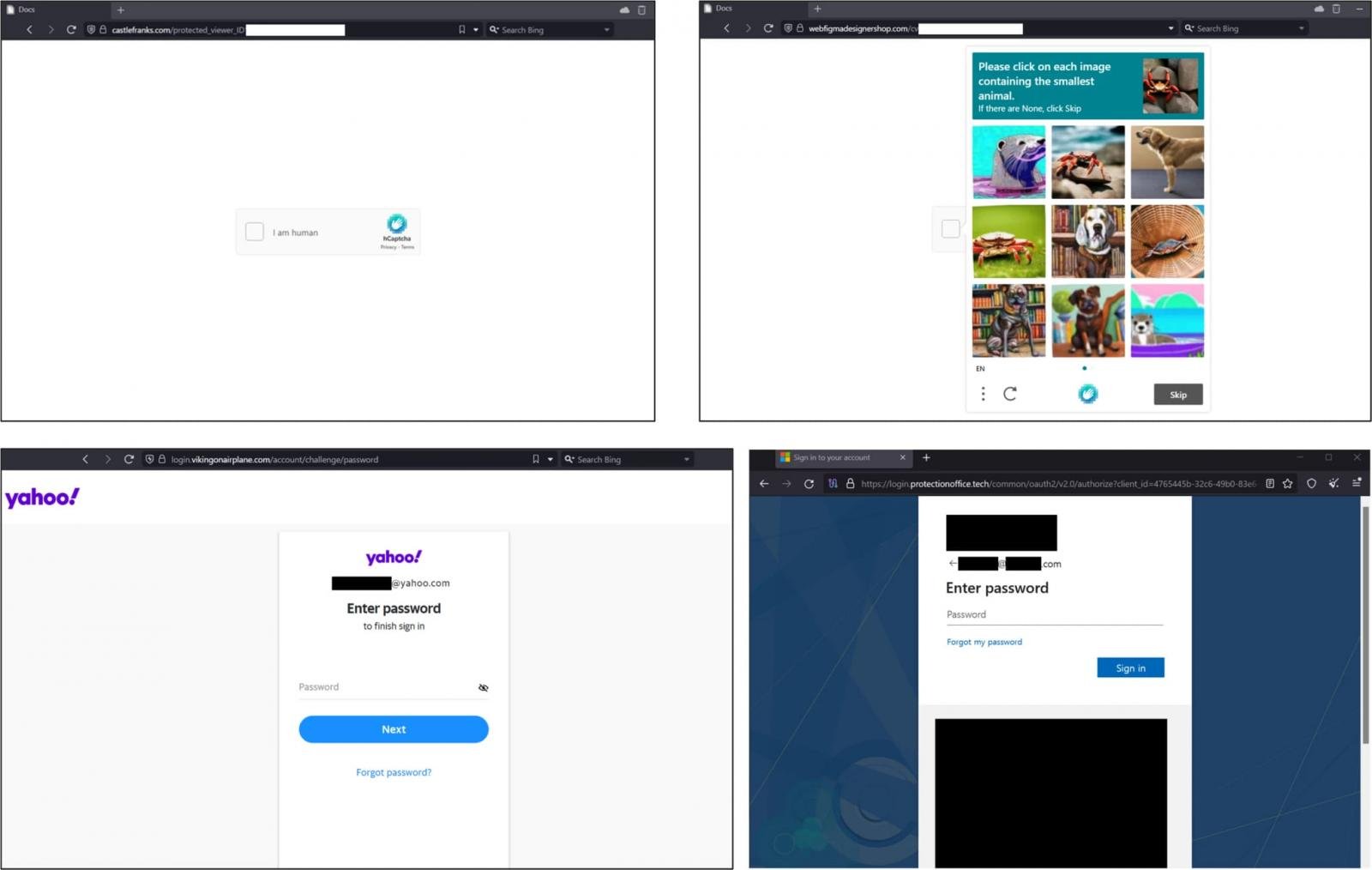

The phishing operation is backed by the open-source EvilGinx proxy attack framework that steals both user credentials and session cookies. This allows Callisto to bypass two-factor authentication when logging in with the stolen credentials.
Next, the attackers use the stolen information to access the victim’s email account, analyze their inbox, and set up forwarding rules that give them ongoing access to the victim’s future communications.
At this final stage, Callisto operators identify and engage in any lateral phishing opportunities, using their access to the victim’s inbox to hit other key targets.
Microsoft has also published a report today highlighting the following new techniques, tactics, and procedures adopted by the threat actor after April 2023:
- Use of server-side scripts that block automated scanning of the malicious infrastructure.
- Use of email marketing platform services like HubSpot and MailerLite to mask true email addresses.
- Use of DNS provider to mask the IP addresses of the VPS infrastructure.
- Use of domain generation algorithm (DGA) for better evasion and resistance to blocks.
Defending against the Callisto threat and any spear-phishing attack requires a multi-faceted approach, including using phishing-resistant MFA methods like hardware keys, implementing strict conditional access policies, and monitoring for abnormal activity.
Sanctioned by the US and UK
An international law enforcement consisting of agencies from the UK, US, Australia, Canada, and New Zealand has identified two members of the Callisto hacking group.
Those are Aleksandrovich Peretuatko, believed to be an FBS Center 18 intelligence officer, and Andrey Stanislavovich Korinets, aka “Alexey Doguzhiev.”
The two are considered directly responsible for Callisto operations targeting multiple UK organizations, some resulting in unauthorized access and exfiltration of sensitive data.
As part of today’s announcement, both the UK and the US have sanctioned the two members for attempting to undermine the UK’s democratic process. The US Department of Justice has also indicted the members for “malign influence operations designed to influence the U.K.’s 2019 Elections.”
“The United Kingdom has sanctioned two individuals for engaging in spear phishing operations with the intention to use information obtained to undermine UK democratic processes,” reads a press statement from the US Department of the Treasury.
“The United States, in support of and in solidarity with the United Kingdom, has also taken action against the same individuals, identifying their connection to the FSB unit and its activity that has targeted US critical government networks.”
The US government’s Rewards for Justice program also offers a $10 million reward for information on Callisto’s group members and their activities.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


![Sliver C2 Detected - 45[.]140[.]143[.]62:31337 7 Sliver C2](https://www.redpacketsecurity.com/wp-content/uploads/2024/02/Sliver-C2-300x142.jpg)
